BokBot, also known as “IcedID” is a Banking Trojan that targets users’ financial information, login credentials, and other sensitive data. This Trojan is typically delivered via spam emails or phishing messages, where the victim is tricked into downloading a malicious attachment or clicking on a malicious link.
BokBot is known for its advanced features, including the ability to bypass security measures such as obfuscation techniques, two-factor authentication, browser protections, and firewalls. Obfuscation techniques include code obfuscation, anti-debugging, and anti-virtualization techniques, which make it difficult for security software to analyze and detect the Trojan’s malicious behavior.
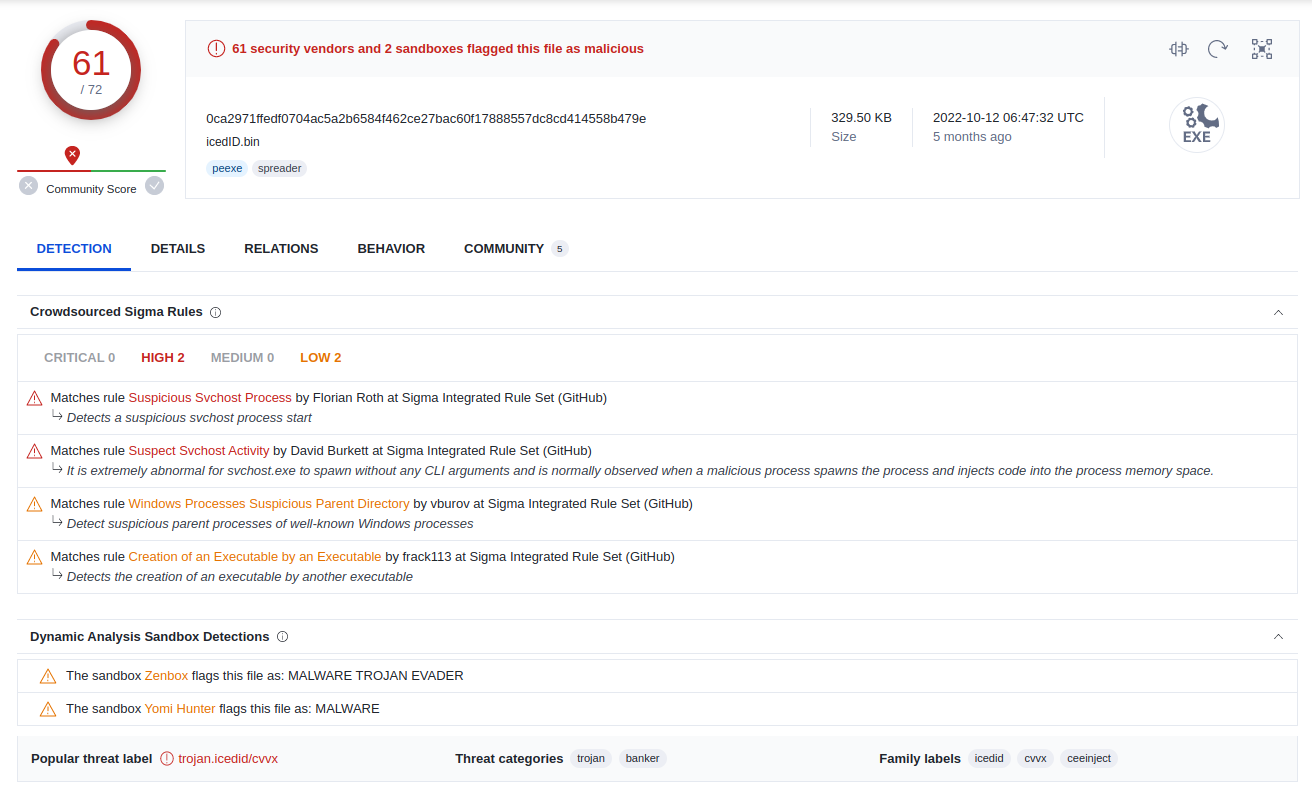
SHA256 : 0ca2971ffedf0704ac5a2b6584f462ce27bac60f17888557dc8cd414558b479e
Download the packed sample from MalShare.
Tools used :
- X64dbg
- PEBear
VirusTotal flagged this file in the category of banking trojan.
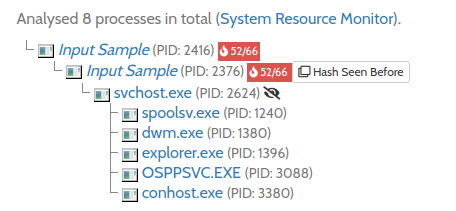
Seeing the Process tree, it indicates that it is doing a PE injection by starting a copy of itself. It also then starts svchost.exe to run the binary in background, that confirms the suspicion.
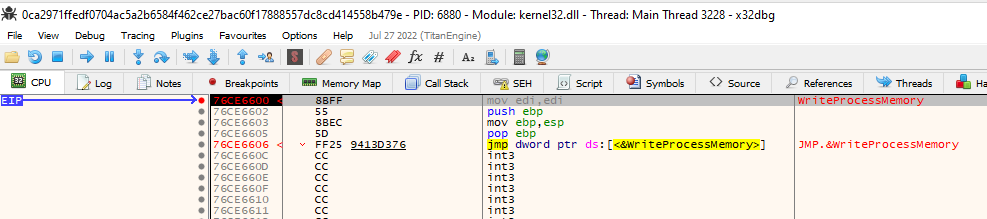
To unpack it, let’s start our Windows VM, and load the binary into x32dbg. Set breeakpoints on CreateProcessInternalW, WriteProcessMemory, ResumeThread.
Breakpoint on ResumeThread is just to make sure we don’t messup, as after loading the buffer into the process, it will resume the Process.
After setting the breakpoints, hit run. It will stop at entrypoint. Keep debugging and will hit the breakpoint at CreateProcessInternalW. And can see in the arguments that it starting a copy of themselves.
Continue debugging, and will hit WriteProcessMemory, where they will try to write something in the process. To know what is being written down, we need to know what arguments are passed to memory.
1
2
3
4
5
6
7
BOOL WriteProcessMemory(
[in] HANDLE hProcess,
[in] LPVOID lpBaseAddress, # address to which data is written
[in] LPCVOID lpBuffer, # buffer that contains the data
[in] SIZE_T nSize,
[out] SIZE_T *lpNumberOfBytesWritten
);
So, it’s the third argument on the stack that contains the data that is going to be written in the memory.
In dump, we can see, what they are going to write in memory, but that’s not a PE file. After 6 breakpoints on WriteProcessMemory, we will get the PE file.
This PE file is being written in the process they already created, so this file is already mapped.
1
2
A mapped PE file refers to a file that has been loaded into memory, typically by a process or application, and is currently being accessed or executed by the system.
On the other hand, an unmapped PE file refers to a file that is not currently being accessed or executed by the system and is not loaded into memory.
Now, dump this PE file out. To dump this file, right click the starting address of PE file in dump and choose Follow in Memory Map. In memory map, right click the PE file section address and choose Dump Memory to file.
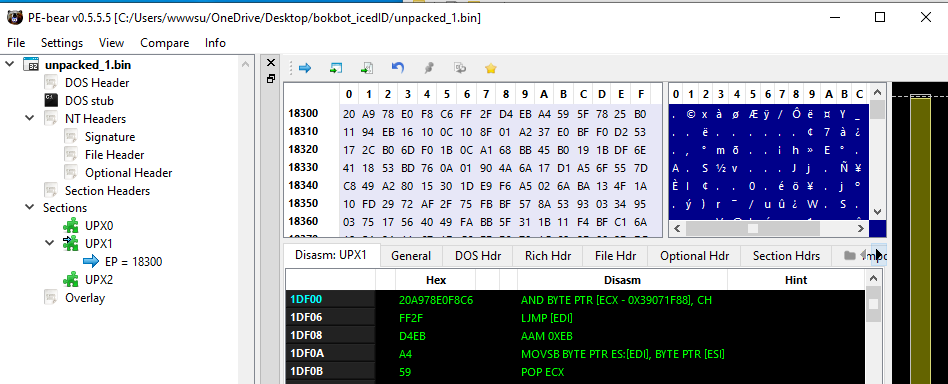
Then, if we look Section Headers of file in PEBear, we can see that Raw addresses and Virtual addresses are different, that means it is mapped. In PEBear, we can clearly see the section named UPX0, UPX1, UPX2, which means it is packed by UPX packer.
To analyse this file, we need to make it in unmapped format, beacuse it is in disk and not loaded in memory. To do that, just edit the raw addresses and raw sizes with the values from virtual addresses and virtual sizes. Save the changes.
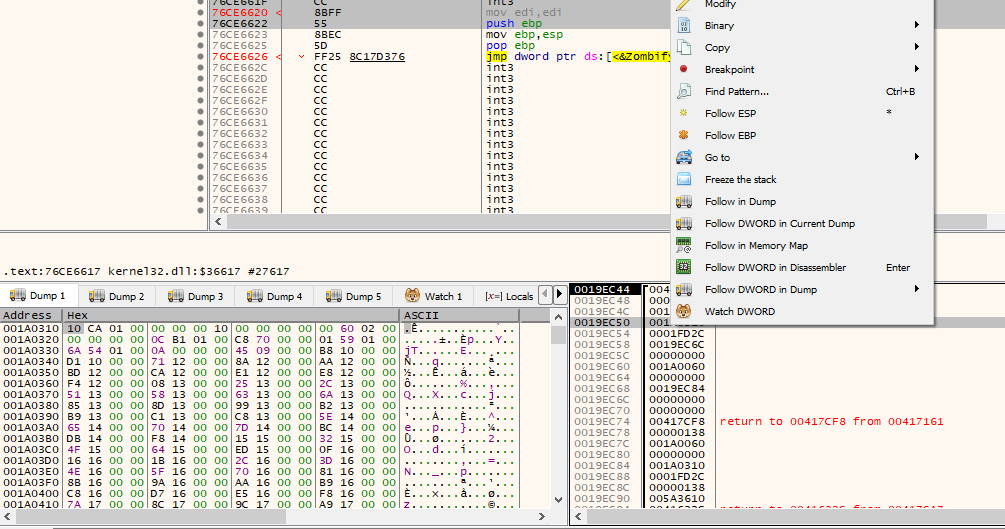
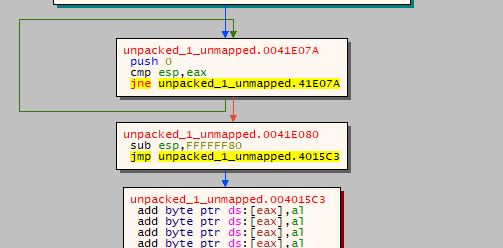
To unpack this packed file, we can’t use usual tools to unpack it beacause it is in it’s mapped format. So, load this file in x32dbg, run it and when you hit the entrypoint, open the graph view and look for a jmp instruction to a register.
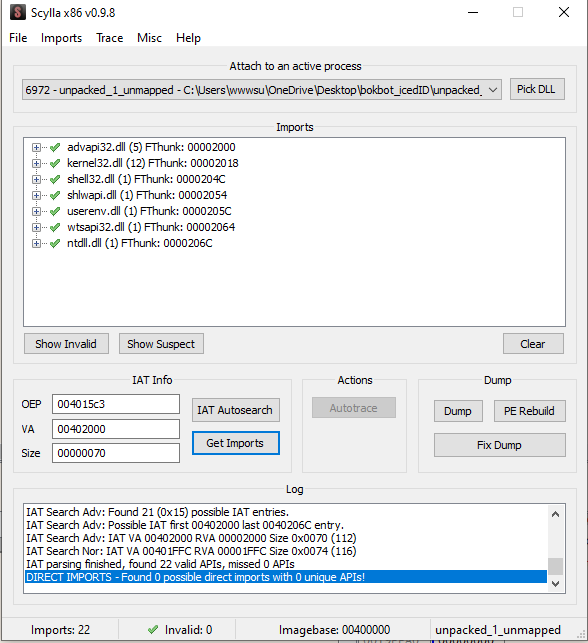
Add a breakpoint to this instruction and when you hit it, jump into that register address. You will reach the OEP(Original Entry Point) for the unpacked section. Use Scylla tool to dump this out. Enter the address of the OEP.
To fix the import address table, do a IAT Autosearch and click get imports. Choose Fix Dump and select the file that you just dumped.
We have unpacked the Bokbot/IcedID payload.
reference : OALabs, VirusTotal