Endpoint Forensics Challenge Writeup – Android Investigation
Content
About Challenge
Category : Endpoint Forensics
Tags : Android, ALEAPP, sqlitebrowser
Author : Infern0o
Difficulty : Easy(4.6)
Password : cyberdefenders.org
Description
Scenario:
We’re currently in the midst of a murder investigation, and we’ve obtained the victim’s phone as a key piece of evidence. After conducting interviews with witnesses and those in the victim’s inner circle, your objective is to meticulously analyze the information we’ve gathered and diligently trace the evidence to piece together the sequence of events leading up to the incident.
Tools:
Question and Answers
First, unzip the file using the password cyberdefenders.org. Then, re-compress it without a password and use the ALEAPP GUI to extract and analyze the data.”
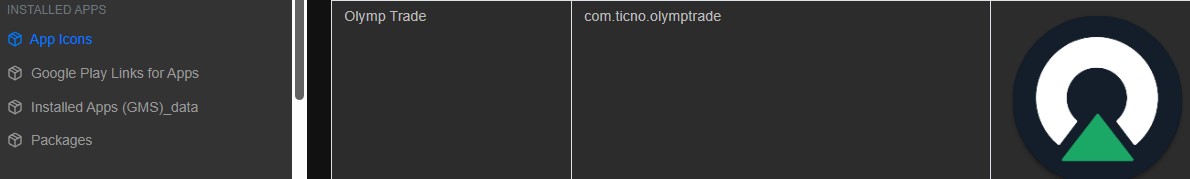
Q1. Based on the accounts of the witnesses and individuals close to the victim, it has become clear that the victim was interested in trading. This has led him to invest all of his money and acquire debt. Can you identify which trading application the victim primarily used on his phone?
Ans. Check the list of installed apps and look for app icons—Olymp Trade should be among them.
Q2. According to the testimony of the victim’s best friend, he said, “While we were together, my friend got several calls he avoided. He said he owed the caller a lot of money but couldn’t repay now”. How much does the victim owe this person?
Ans. Look through the call logs for the number that made multiple calls to the victim.
Next, look for any messages from that same number—it’s possible the caller followed up with an SMS when their calls went unanswered.”
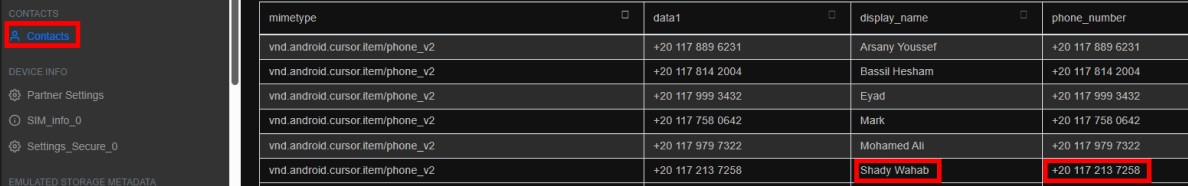
Q3. What is the name of the person to whom the victim owes money?
Ans. Search the contacts for that number.
Q4. Based on the statement from the victim’s family, they said that on September 20, 2023, he departed from his residence without informing anyone of his destination. Where was the victim located at that moment?
Ans. Check the Google Search history for any relevant information. You should find an image of a hotel.
Perform a reverse image search on Google to identify the hotel.
Q5. The detective continued his investigation by questioning the hotel lobby. She informed him that the victim had reserved the room for 10 days and had a flight scheduled thereafter. The investigator believes that the victim may have stored his ticket information on his phone. Look for where the victim intended to travel.
Ans. Keep searching the data for any images related to the ticket.
Q6. After examining the victim’s Discord conversations, we discovered he had arranged to meet a friend at a specific location. Can you determine where this meeting was supposed to occur?
Ans. This one was tricky. I searched for information on Discord chat logs and found helpful details on this.
1
On Android, Discord stores its application files under the "/data/data/com.discord/" directory. Three subdirectories of special interest are "shared_prefs," "cache," and "files" which respectively contain user configuration information in the file called “com.discord_preferences.xml,” cached multimedia files, and Discord usage details such as chat messages. The format and parsing of the Message files is detailed in Technical Series Publication 2020-001.
Check the ‘files’ directory and load the database into DB Browser for further inspection.
That concludes the challenge!