These Labs are from Chapter 18(Packers and Unpacking) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
Tools used:
- Detect-It-Easy
- CFF Explorer
- IDA Pro
- x64Dbg
Your goal for the labs in this chapter is simply to unpack the code for further analysis. For each lab, you should try to unpack the code so that other static analysis techniques can be used. While you may be able to find an automated unpacker that will work with some of these labs, automated unpackers won’t help you learn the skills you need when you encounter custom packers. Also, once you master unpacking, you may be able to manually unpack a file in less time than it takes to find, download, and use an automated unpacker.
Each lab is a packed version of a lab from a previous chapter. Your task in each case is to unpack the lab and identify the chapter in which it appeared. The files are Lab18-01.exe through Lab18-05.exe.
Lab 18-01
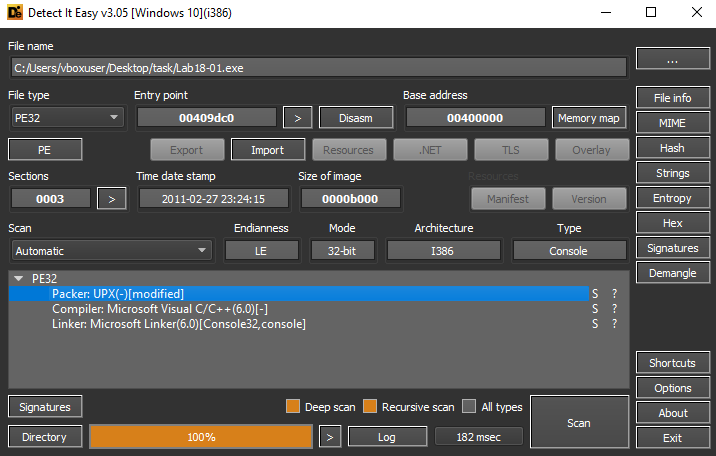
After opening the executable in DiE, we can see that it detected that it is packed by modified UPX.
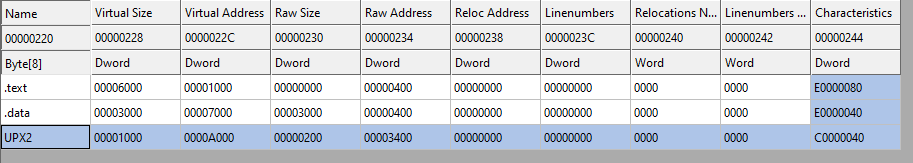
Seeing the sections in CFF Explorer, we can see that it contains a section named “UPX2”.
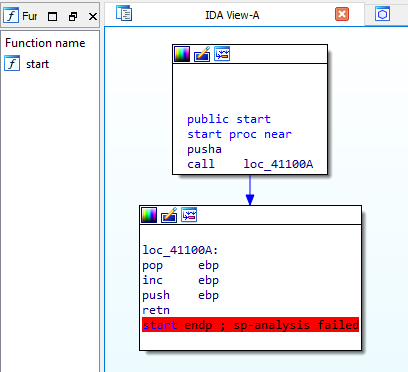
So let’s open the malware in IDA Pro to see the jump to OEP. IDA too gives a warning that this program may be packed while loading the binary.
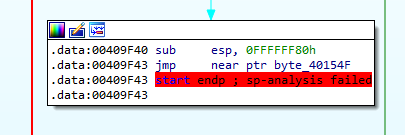
IDA Pro red marked a jump instruction because it couldn’t disassemble the packed data.
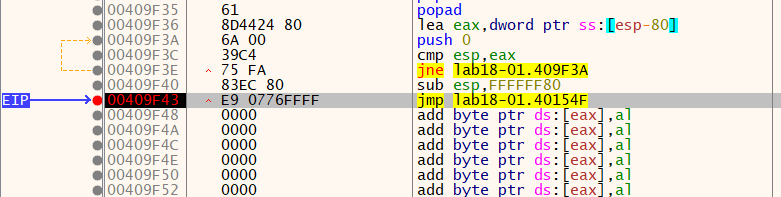
To unpack it we just have to put a breakpoint at this jmp instruction and follow it, we will be able to reach the OEP.
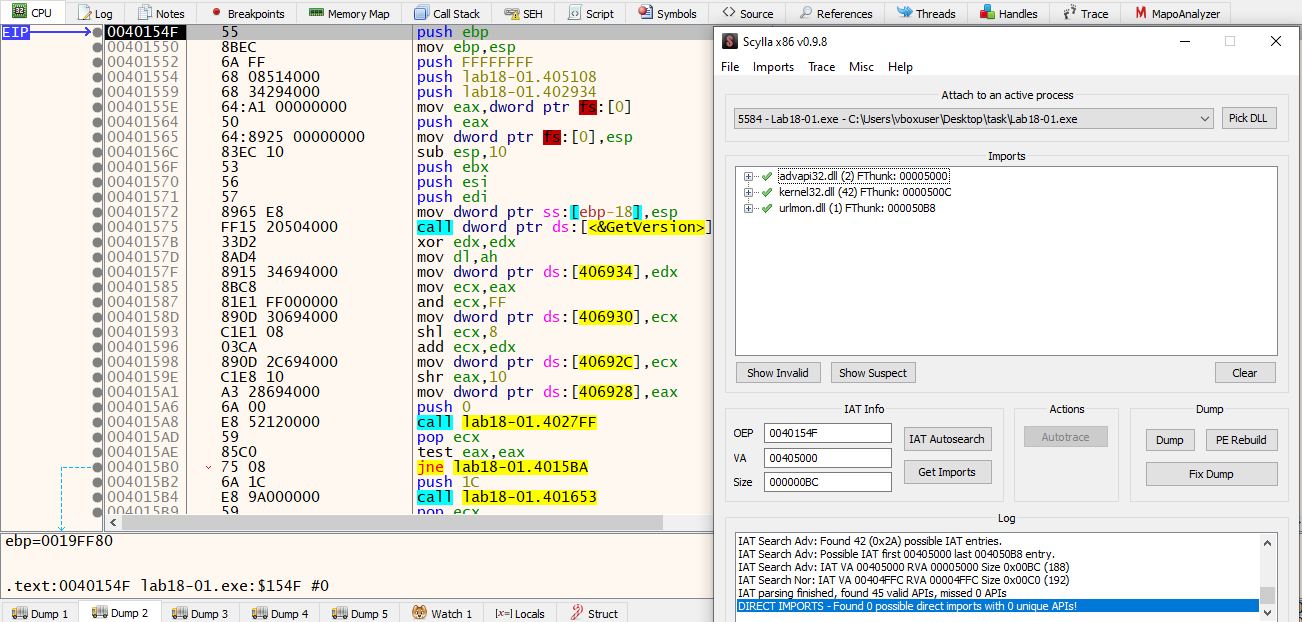
We can see that the jmp instruction is followed by NULL bytes. After single-stepping the jmp instruction, we reach the OEP.
By using the x32dbg plugin Scylla, we can get the imports and dump the unpacked binary.
We can find the tail jump by an another way too. Apply a hardware breakpoint at the esp location where it pushes the first bytes at entrypoint.
After going through the unpacked binary, we identified that this is the sample executable from Lab14-01.
Lab 18-02
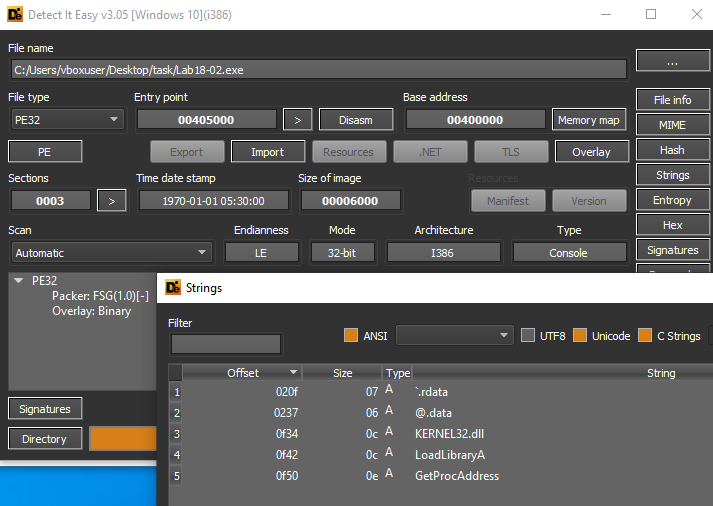
DiE detected that it is packed by FSG(1.0). It don’t contain any strings and only 2 imports(GetProcAddress, LoadLibraryA).
IDA Pro gave a warning while opening this binary.
In IDA, we could see a reference of dword_401090 at 0x4050E1. Other than this we see a red marked instruction at address 0x40508E.
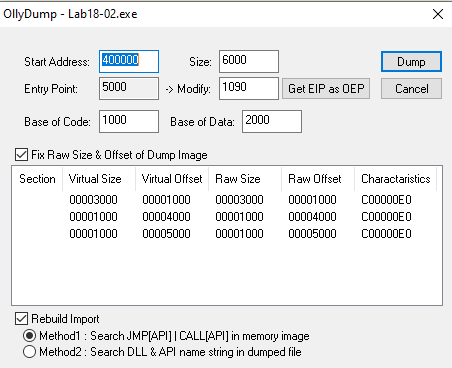
Load the binary in OllyDbg, it stops at 0x405000. We can identify the OEP by using the OllyDump plugin. Plugins -> OllyDump -> Find OEP by Section Hop(Trace over). It will stop the execution at 0x401090, but we can’t see the disassembled instruction at this section.
TO force the OllyDbg to disassemble this code, right click at the byte at 0x401090 and select Analysis -> Analysis code.
You can dump the unpacked malware using Plugins -> OllyDump -> Dump Debugged Process.
Now, we can see all kind of information(imports, strings) in this unpacked malware. Going through this malware reveals that it is the same executable as Lab07-2.exe.
Lab 18-03
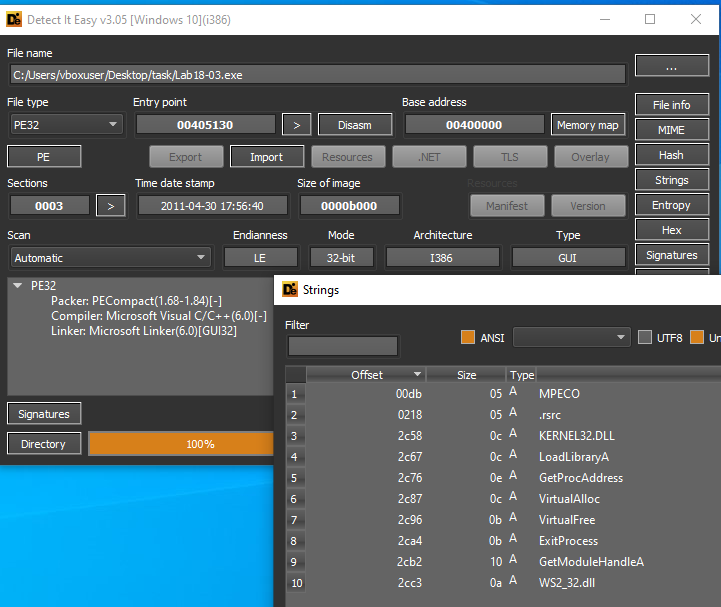
In DiE, we can see that is is packed by PECompact(1.68-1.84). It contains a few strings and imports.
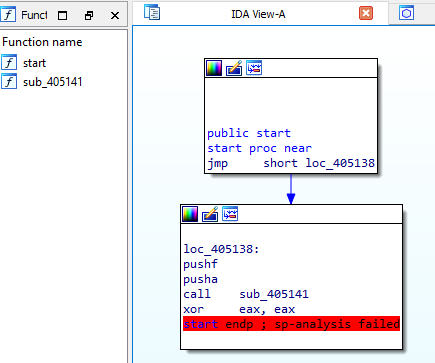
IDA Pro gave warning while opening the malware in it.
IDA only identified two functions which doesn’t give much insight about the tail jump and packing stub.
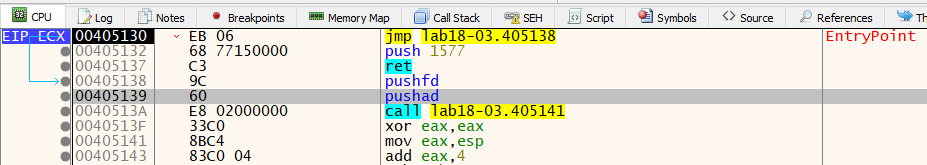
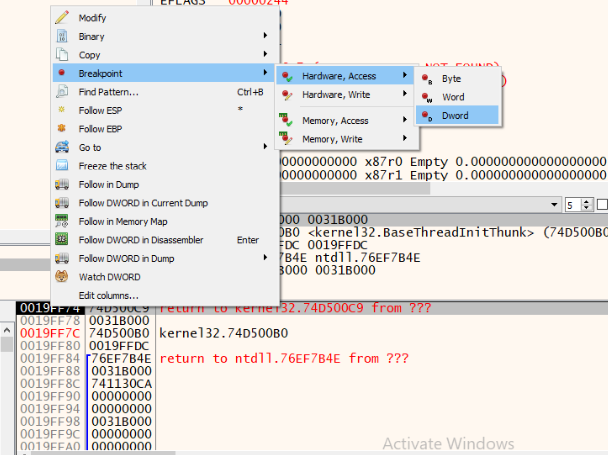
SO, let’s load the binary in x64dbg where it stops the execution at system breakpoint at 0x76F41C33 in ntdll region. It also sets one time breakpoint at 0x405130. Set a read breakpoint on the stack approach, we see a pushad instruction at 0x405139.
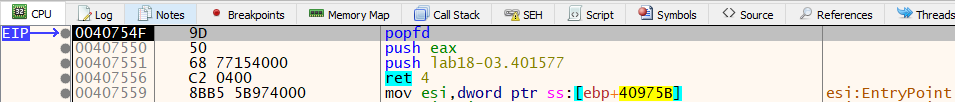
To set a read breakpoint on the stack, left click on the esp when eip reaches 0x40513A. Choose Breakpoint -> Hardware, Access -> Dword. After resuming the execution, debugger hit the breakpoint at 0x40754F on popfd instruction. Under which we see that it pushes an address to stack and return to it.
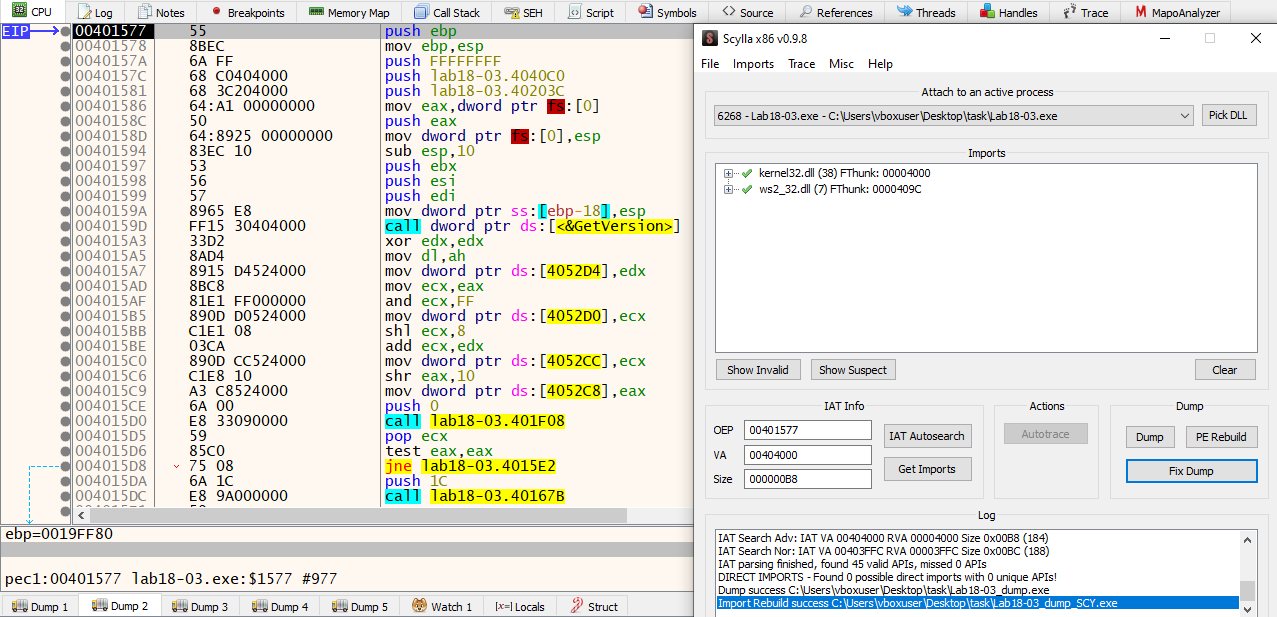
We have found the tail jump and following which we reached the unpacked entrypoint. Usin Scylla, we dump the unpacked malware.
After going through the unpacked malware, we recognise that it is the same sample from Lab09-02.
Lab 18-04
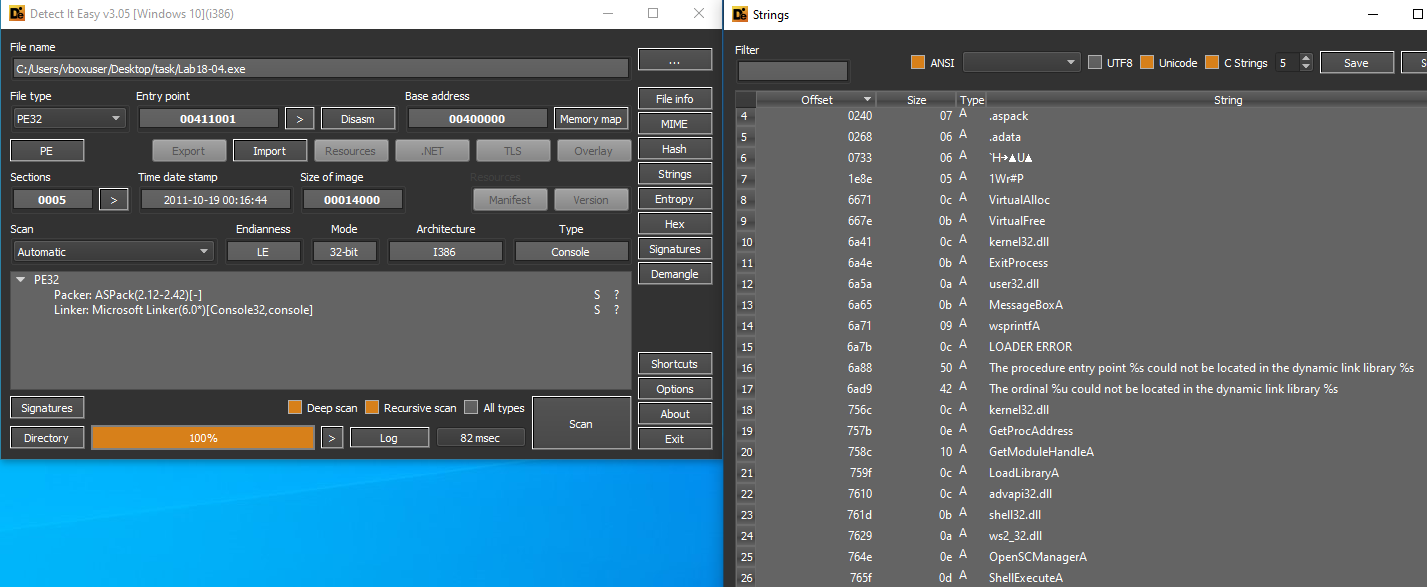
DiE detected that this binary is packed by ASPack(2.12-2.42) packer. We can see that it contains three imports from kernel32.dll and one import from other DLLs.
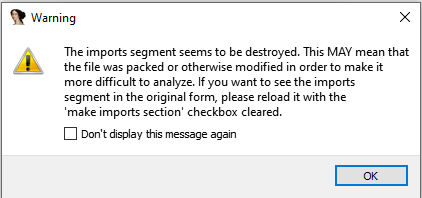
IDA gives a warning about the destroyed imports segment. IDA was able to identify/disassemble only one function.
In book, Author has mentioned the technique to unpack any malware packed by ASPack. So, let’s load the executable in x64dbg, where it stops the execution at system breakpoint 0x76F41C33. Resuming the execution, it again breaks at 0x411001, which is entry point to the packing stub. The instruction at 0x411001 is pushad. Step over this instruction and put a read hardware breakpoint on the stack. After reaching 0x411002, left click on stack top address and choose Breakpoint -> Hardware, Access -> Dword.
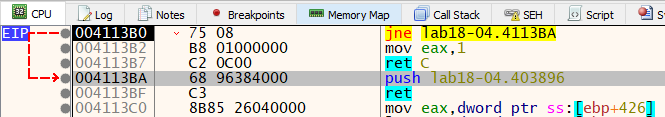
Resuming the execution, it break at 0x4113B0, where it push the address 0x403896 and return to it.
0x403896 is the Original Entry point to the unpacked malware. Using Scylla, we can dump the unpacked sample.
Going through the malware, we can see that it the same sample as Lab09-01.exe.
Lab 18-05
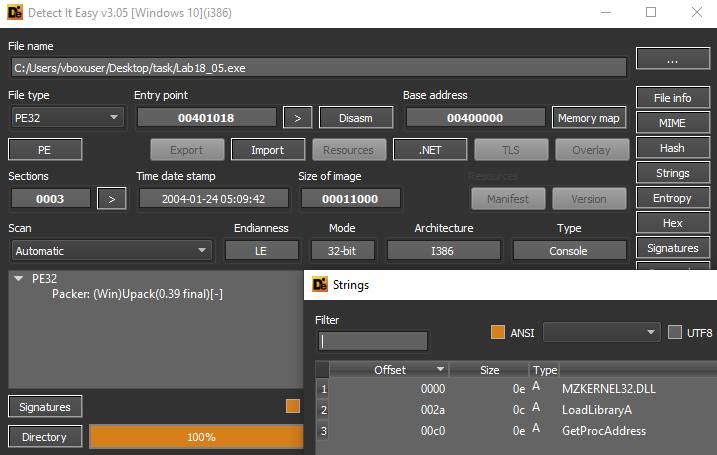
Die detected that this malware is packed by (Win)Upack(0.39 final). It doesn’t contain any strings and imports.
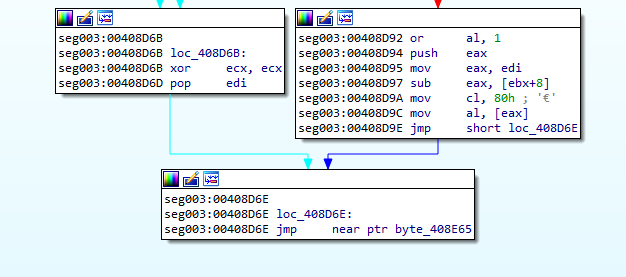
IDA Pro gives all kinds of warning about unaligned section pointers, truncated section, translation for relative address, destroyed imports segment. IDA identified only start function which ends with jmp instruction.
I thought this is the tail jump, so i loaded the malware into x64dbg and put a breakpoint on 0x408D6E. But after some iterations, we can see it unpacking the malware in dump from address 0x401000.
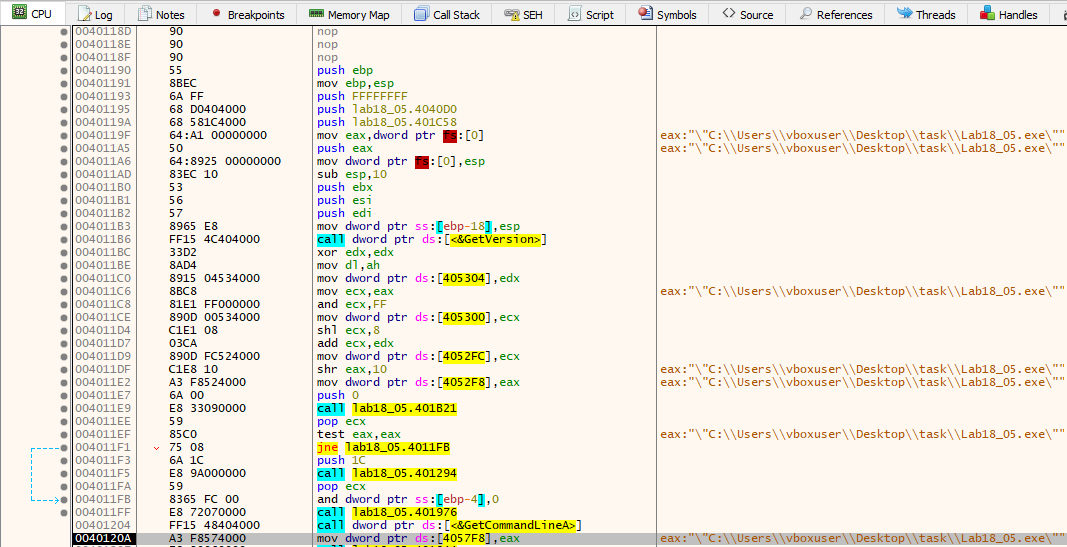
In book, author has mentioned that, to unpack malware packed by WinUpack, put a breakpoint at GetCommandLineA and the OEP should be above it.
So i put the breakpoint at GetCommandLineA, and restarted the debugger. We hit the breakpoint at 0x75FD2580, we run to user code and reach at address 0x40120A. Scrolling above, we can see push ebp instruction at 0x401191 which seems to be the entrypoint.
Now, Dump the unpacked malware using Scylla.
Going through the unpacked malware, we can see that this sample is from Lab07-01.