Content
- Malware Analysis
- Type of Malware Analysis
- Antivirus Scanning
- Hashing
- String Analysis
- Detecting Packers
- PE File Format
- Linked Libraries and Functions
- Resource Section
What is Malware Analysis?
The main goal of malware analysis is to understand the purpose and behavior of suspicious binaries or files.
Typically, the objectives of malware analysis include:
- Gathering information to respond effectively to an intrusion.
- Determining exactly what occurred during the attack.
- Ensuring all infected files are identified and located.
- Understanding the capabilities of the malware, how to detect it, and how to measure and contain the damage it can cause.
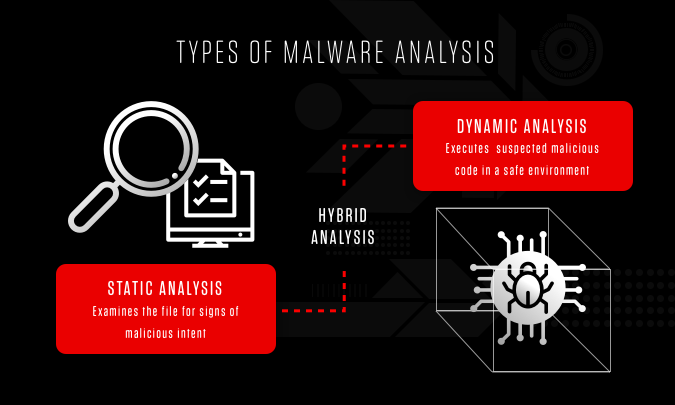
Types of malware analysis
Static Analysis involes examining the malware without running it.
Dynamic Analysis involes running the malware and observe its behavior.
Basic Static analysis can confirm whether a file is malicious, provide information about its functionality, adn sometimes provide information that will allow you to produce simple network signatures. it is straightforward and can be quick, but it is largley ineffective against sophisticated malware, and it can miss important behaviors.
Advanced Static analysis consists of reversing the malware’s internals by loading the binary into disassembler and looking at the program instructions in order to discover what the program does.
In this post, we will focus on Basic Static techniques only.
We’ll discuss techniques one by one.
Antivirus Scanning: A useful first step
First step is to run the the binary through multiple antivirus programs. These antivirus programs depends on database that contains same pieces of file signatures and behavioral and pattern-matching analysis to indentify suspect files.
There are nice websites that allow you to upload a file for scanning by multiple antivirus engines:
Hashing: A fingerprint for malware
Hasing is common method used to uniquesly identify malware. There are many hashing algorithms that generate hash like Message-Digest Algorith(MD5), Secure Hash Algorithm(SHA-1), and many more.
Finding Strings
A program contains strings if it prints a message, connects to a URL, or copies a file to a specific location, including DLLs, and any much more information.
Detecting Packers with PEiD
Malware writers usually use packing or obfuscation to make their files more difficult to analyze or detect. Programs with few strings are either obfuscated or packed.
Packed or obfuscated code will often include at least the functions LoadLibrary and GetProcAddress, which are used to load and gain access to additional functions.
You can use PEiD to detect the type of packer or compiler employed to build an application.
PE File Format
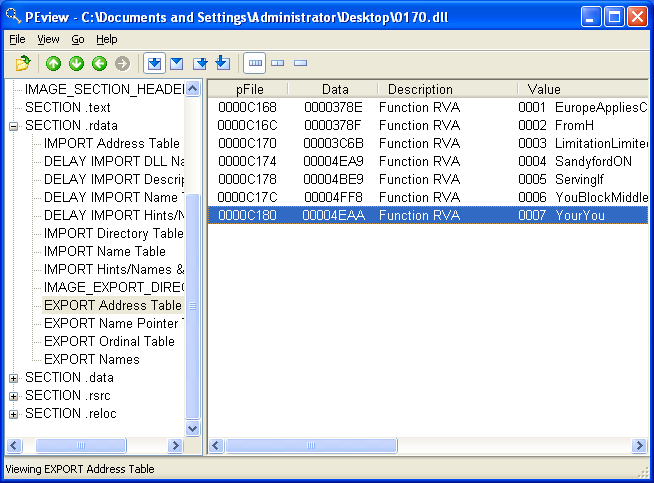
The Portable Executable(PE) file format is used by Windows executables, object code, and DLLs. PE files begin with a header that includes information about the code. PE file header stores information about every library that will be loaded and every function that will be used by the program.
PE header can be examined through PEview
Linked libraries and Functions
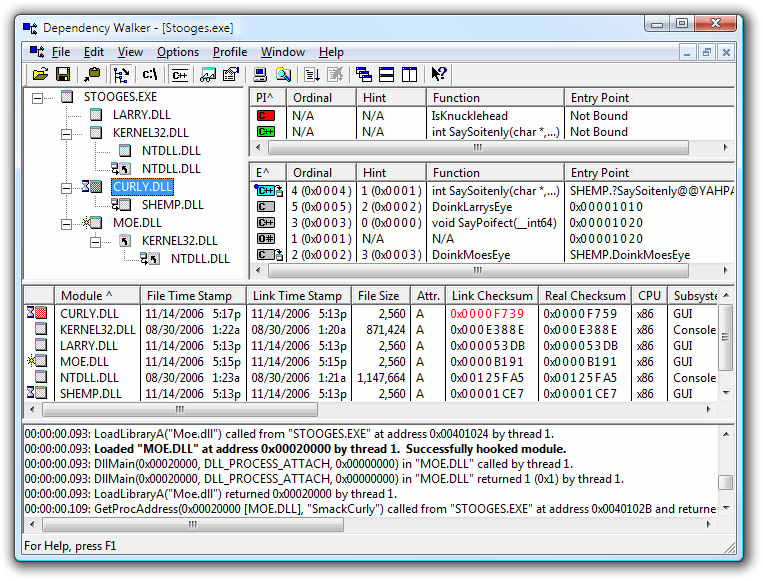
Imports are functions used by one program that are actually stored in a different program, such as code libraries that contain functionality common to many programs. Code libraries can be connected to the main executable by linking.
Dependency Walker program lists dynamically linked functions in an executable.
The libraries used and functions called are often the most important parts of the program, and identifying them is particularly important, as it allows us to guess what the program does.
We can see the Documentation of Windows API on Microsoft Developer Network(MSDN) Library.
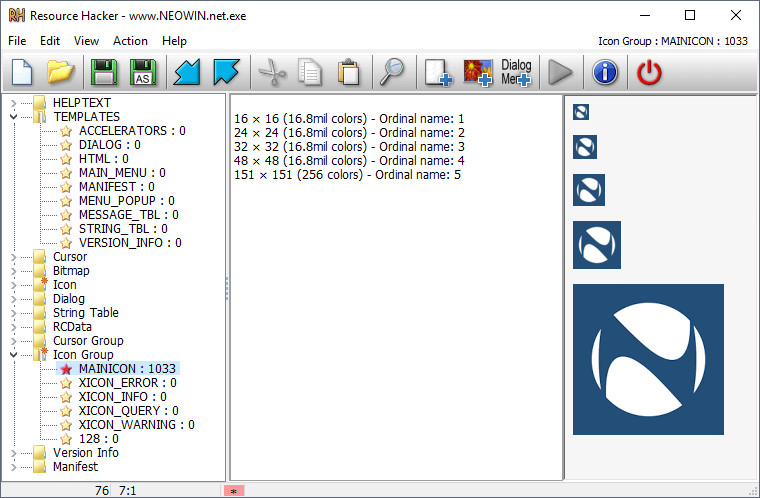
Viewing resource section with Resource Hacker
Resource Hacker can show all the resources included in the executable. Resources like menus, icons, Version info, Dialog, etc.
References : These are notes from “Practical Malware Analysis” book and from my experience.