I have been learning from the Book Practical Malware Analysis written by Michael Sikorski and Andrew Honig. Its a good book, as there are Labs provided at the end of each chapter for practicing your learning.
Here is the walkthrough of first lab of first chapter i.e. “Basic Static Techniques”.
1
Question : This Lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
You can download the binary and dll from here .
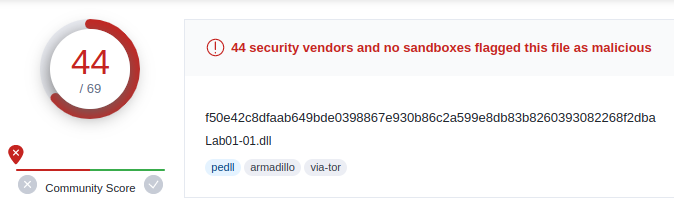
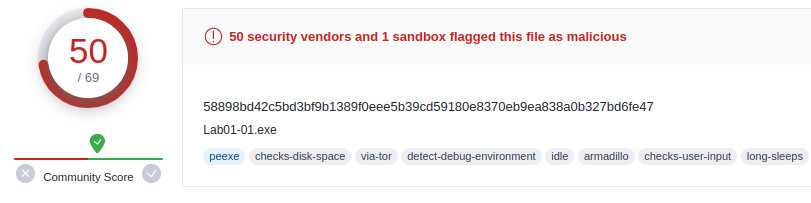
Q1: Upload the files to http://www.Virustotal.com/ and view the reports. Does either file match any existing antivirus signatures?
Dll was flagged malicious by 44 vendors and executable by 50. These were categorised in trojan family.
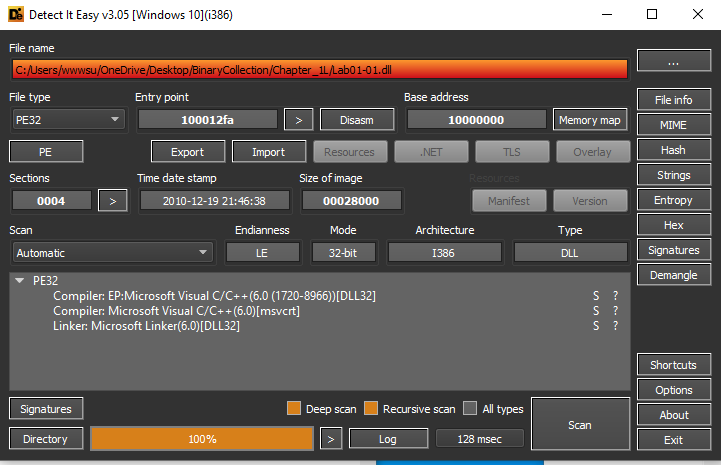
Q2: When were these files compiled?
It can be seen on Detect-it-Easy that both files were compiled on 2010-12-19 21:46:38, within 1 minute of each other. To view the compiled date in PEView, navigate to IMAGE_NT_HEADERS > IMAGE_FILE_HEADERS > Time Date Stamp.
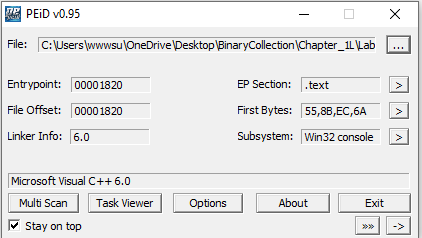
Q3: Are there any indications that either of these files packed or obfuscated? If so, what are these indicators?
PEid don’t detect any packer in both the files. Microsoft Visual C++ 6.0 is the compiler that is shown in PEid.
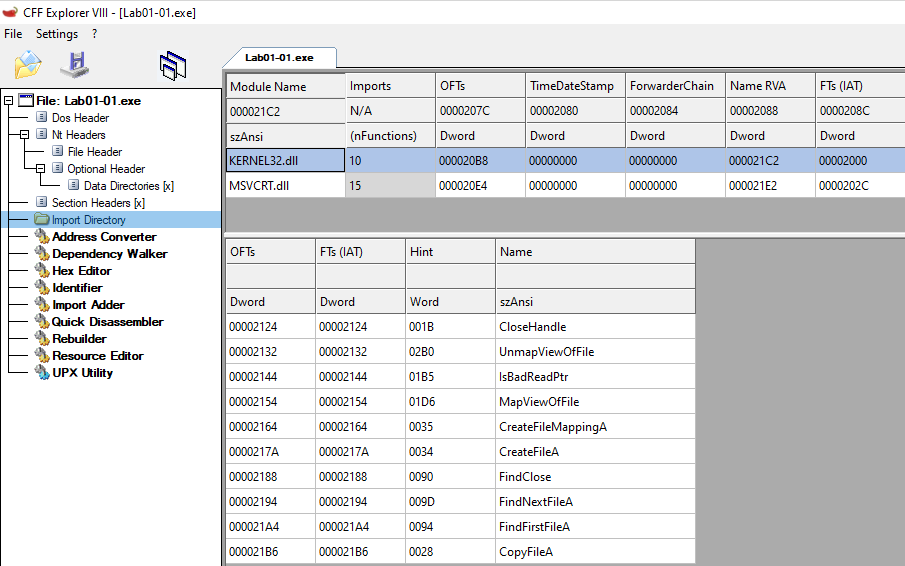
In CFF Explorer, we can see the imports clearly, but the less number of imports indicate that it is small program.
Q4: Do any imports hint at what this malware does? If so, which imports are they?
We can see the imports using the tools Detect it easy or CFF Explorer.
Function imported by exe:
- KERNEL32.dll : It handles the memory usage in “Microsoft Windows”
- CLoseHandle : Closes an open object handle.
- UnmapViewOfFile : Unmaps a mapped view of a file from the calling process’s address space.
- IsBadReadPtr : Verifies that the calling process has read access to the specified range of memory.
- MapViewOfFile : Maps a view of a file mapping into the address space of a calling process.
- CreateFileMappingA : Creates or opens a named or unnamed file mapping object for a specified file.
- CreateFileA : Creates or opens a file or I/O device.
- FindCLose : Closes a file search handle opened by the FindFirstFile, FindFirstFileEx, etc.
- FindNextFileA : Continues a file search from a previous call to the FindFirstFile, FindFirstFileEx, or FindFirstFileTransacted functions.
- FindFirstFileA : Searches a directory for a file or subdirectory with a name that matches a specific name.
- CopyFileA : Copies an existing file to a new file.
- MSVCRT.dll : It is a part of the “Microsoft Visual Studio 6.0” and is crucial for most applications to work properly
Functions imported by dll:
- KERNEL32.dll
- CreateProcessA : Creates a new process and its primary thread.
- CreateMutexA : Creates or opens a named or unnamed mutex object.
- OpenMutexA : Opens an existing named mutex object.
- CloseHandle
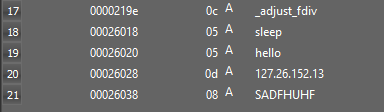
- Sleep
- WS2_32.dll : Used to handle network connections(imports are being imported by ordinal value)
- socket(0x17) : Creates a socket that is bound to a specific transport service provider.
- WSAStartup(0x73) : Initiates use of the Winsock DLL by a process.
- inet_addr(0xb) : Converts a string containing an IPv4 dotted-decimal address into a proper address for the IN_ADDR structure.
- connect(0x4) : Establishes a connection to a specified socket.
- send(0x13) : Sends data on a connected socket.
- shutdown(0x16) : Disables sends or receives on a socket.
- recv(0x10) : Receives data from a connected socket or a bound connectionless socket.
- closesocket(0x3) : Closes an existing socket.
- WSACleanup(0x74) : Terminates use of the Winsock 2 DLL (Ws2_32.dll).
- htons(0x9) : Converts a u_short from host to TCP/IP network byte order.
Executable is importing functions from KERNEL.dll, that are used for opening and manipulating filesystem.
Dll imports Sleep and CreateProcessA from KERNEL32.dll, that are usually used in Backdoors. From WS2_32.dll, it imports functions to connect to internet or an IP to send and receive some data.
Q5: Are there any other files or host-based indicators that you could look for on infected systems?
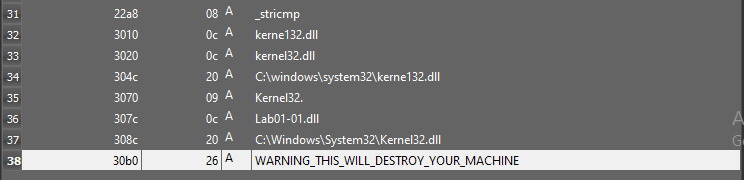
Going through the string in the exe, there are some strings that seems intresting, i.e.: C:\windows\System32\Kernel132.dll, Lab01-01.dll, WARNING_THIS_WILL DESTROY_YOUR_MACHINE.
Q6: What network-based indicators could be used to find this malware on infected machines?
We can clearly see in strings that dll contains an IP address(127.26.152.13) and it imports functions from WS2_32.dll that are required to communicate to it.
Q7: What would you guess is the purpose of these files?
It’s likely to be a Backdoor, as first the exe looks for the C:\windows\system32\kerne132.dll, if it doesn’t exists then it copies the dll to this location. Dll tries to communicate with the IP 127.26.152.13.