It is a Lab from Chapter 11(Malware Behavior) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
This lab shows a new technique. It Trojanizes windows service and starts Keylogging
Tools used:
- Detect-it-Easy
- Procmon
- IDA Pro
- x64dbg
We are given with Lab11-03.exe and Lab11-03.dll files.
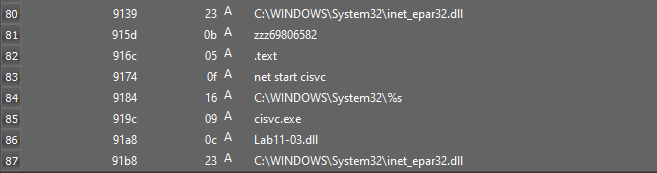
First Load the exe in Detect-it_easy to examine the strings and imports. It contains interesting strings like “C:\WINDOWS\System32\inet_epar32.dll”, “zzz69806582”, “net start cisvc”, etc.
The net start command is used to start a service on windows. The Content Index Service(Cisvc) catalogs and tracks files on the hard drive and indexes them for faster search results.
Next, load the DLL in DiE and we see that it has one export named “zzz69806582”. It contains a string “C:\WINDOWS\System32\kernel64x.dll” and imports like GetForeGroundWindow, GetWindowTextA, GetAsyncKeySate which makes me think that it might be keylogger
GetForeGroundWindow -> Retrieves a handle to the foreground window (the window with which the user is currently working).
GetWindowTextA -> Copies the text of the specified window’s title bar (if it has one) into a buffer.
GetAsyncKeyState -> Determines whether a key is up or down at the time the function is called, and whether the key was pressed after a previous call to GetAsyncKeyState.
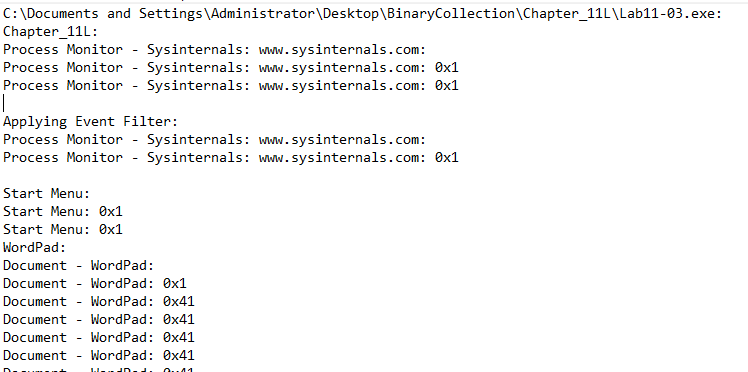
Next, we try to run the executable and observe it in Procmon. We see that it create “C:\WINDOWS\SysWOW64\inet_epar32.dll” and tries to open the file “C:\WINDOWS\SysWOW64\cisvc.exe” and starts the cisvc service by issuing the command “net start cisvc”.
It wasn’t able to run properly, as this Windows 10 doesn’t use cisvc service anymore. So i ran it on Windows XP, and saw that it created “C:\WINDOWS\System32\Kernel64x.dll” which contained the key logs.
For deeper understanding, load the exe in IDA Pro and start by examining the main function.
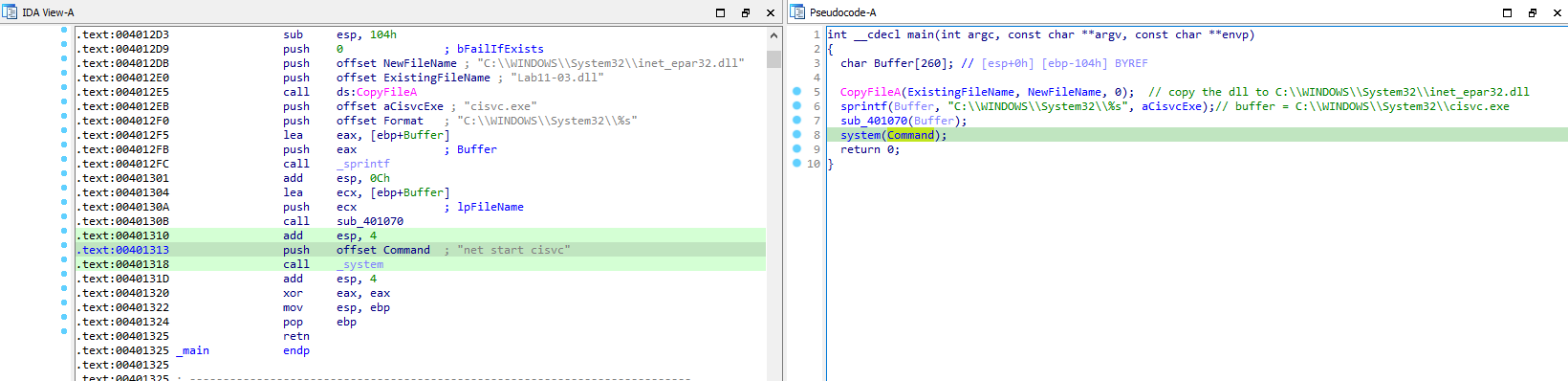
Main function starts by copying the Lab11-03.dll into C:\WINDOWS\SysWOW64\inet_epar32.dll and next it forms a string “C:\WINDOWS\System32\cisvc.exe and passes it to function sub_401070. Finally, it starts the service cisvc by passing the command “net start cisvc” to system.
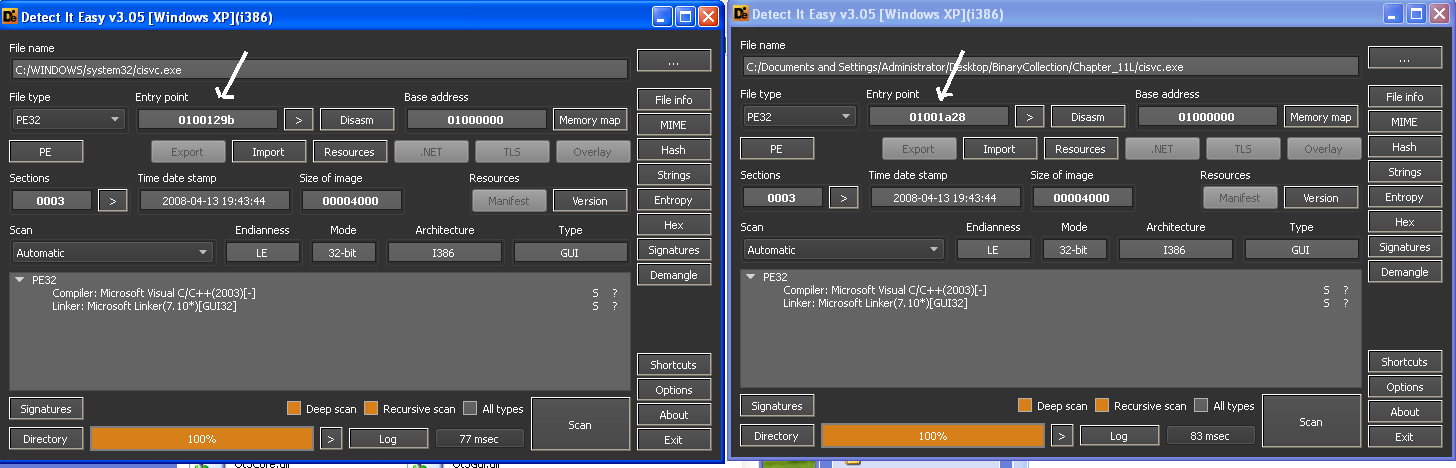
Next the function sub_401070 manipulates the cisvc.exe file using the API calls(CreateFileA, CreateFileMappingA, MapViewOfFile). After loading the cisvc.exe into IDA, we see that the entrypoint in real cisvc and modified cisvc are different.
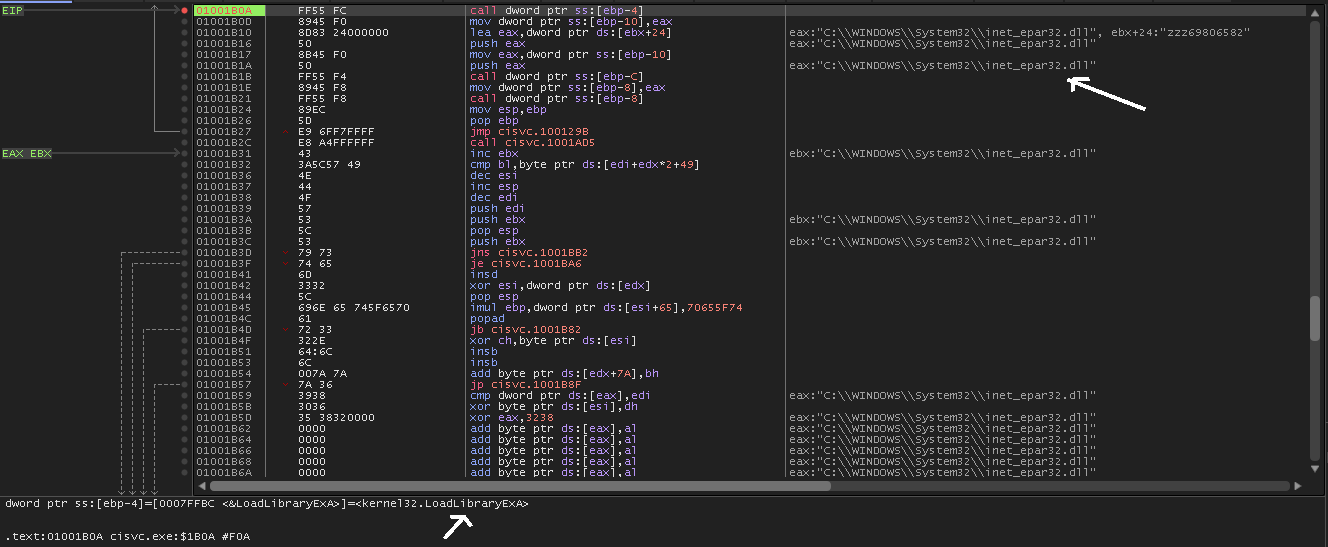
So let’s load the modified cisvc.exe into IDA and follow the jumps.
Load the cisvc.exe into x64dbg and we see that it first calls LoadLibrary to load the inet_epar32.dll and then gets the address of the export function “zzz69806582” by calling GetProcAddress. Then, it calls the function and return to the actual entrypoint.
Next, load the inet_epar32.dll in IDA Pro which is similar to Lab11-03.dll. Export “zzz69806582” creates a thread and return. The thread is passed with StartAddress function as lpStartAddress parameter and set to run just after its creation. So, lets analyse the StartAddress function. At first it checks whether a mutex named “MZ” is exists or not. If it exists it exits and if not then it creates one. Next, it creates a file named “C:\WINDOWS\System32\kernel64x.dll” and it sets the pointer at the end of the file using API SetFilePointer.
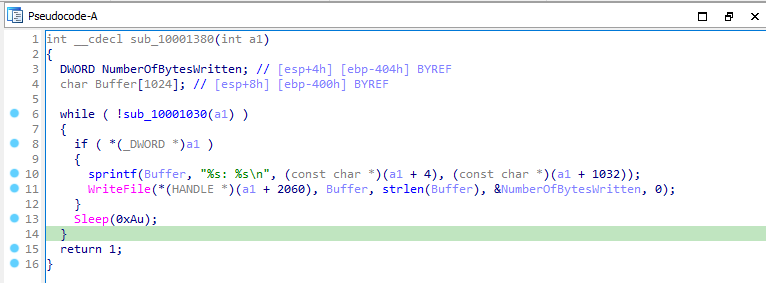
Then it calls a function sub_10001380, which is responsible for keylogging. It contains a loop which calls an function sub_10001030 and logs the keys to the file.
Let’s see the function sub_10001030, it calls another function sub_10001000 which is responsible for getting the windows title bar of the active window through the APIs GetForeGroundWindow and GetwindowTextA. Then the function sub_10001030 checks which keys are being pressed using the API GetAsyncKeyState.
Questions and Answers
Question 1: What interesting analysis leads can you discover using basic static analysis?
Answer: Imports(GetAsyncKeyState and GetForegroundWindow) in Lab11-03.dll indecates that it might be a keylogger. Lab11-03.exe contains strings like “inet_epar32.dll” and “net start cisvc” which make us suspect that it uses cisvc service.
Question 2: What happens when you run this malware?
Answer: It copies the Lab11-03.dll to C:\Windows\SysWOW64\inet_epar32.dll and trojanize the cisvc.exe and starts the cisvc service. Then it creates C:\WINDOWS\System32\kernel64x.dll to log the keystrokes.
Question 3: How does Lab11-03.exe persistently install Lab11-03.dll?
Answer: The malware trojanize C:\WINDOWS\System32\cisvc.exe making it load inet_epar32.dll.
Question 4: Which Windows system file does the malware infect?
Answer: C:\WINDOWS\System32\cisvc.exe
Question 5: What does lab11-03.dll do?
Answer: Lab11-03.dll has an export zzz69806582 which contains all the the keylogging functionality.
Question 6: Where does the malware store the data it collects?
Answer: C:\WINDOWS\System32\kernel64x.dll