Endpoint Forensics: Analyzing a Linux Disk Image in FTK Imager
Challenge Description
Challenge Author: Champlain College
Easy(4.5)
Instructions:
- Unzip the challenge (pass: cyberdefenders.org)
- Load the AD1 image in FTK imager latest Windows version.
Scenario:
After Karen started working for ‘TAAUSAI,’ she began to do some illegal activities inside the company. ‘TAAUSAI’ hired you as a soc analyst to kick off an investigation on this case.
You acquired a disk image and found that Karen uses Linux OS on her machine. Analyze the disk image of Karen’s computer and answer the provided questions.
Tools:
Question & Answer:
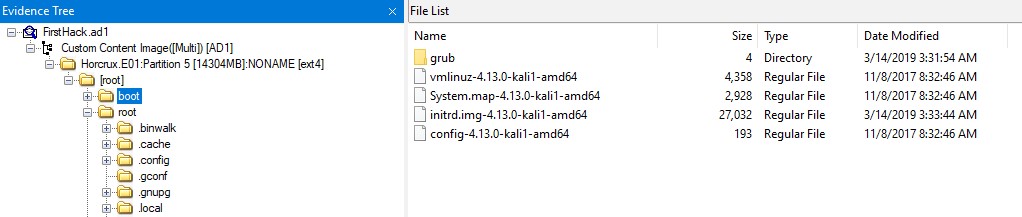
Q1. What distribution of Linux is being used on this machine?
Ans. In the boot section, we can see that the Linux distribution being used is Kali.
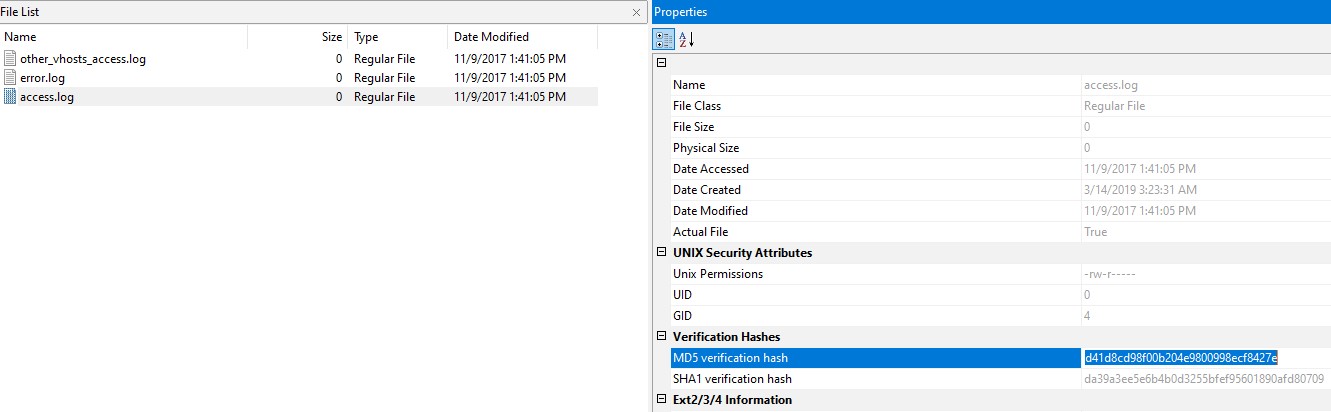
Q2. What is the MD5 hash of the apache access.log?
Ans. In /var/log/apache2/, we can see the access.log file and its MD5 hash in the properties section.
Q3. It is believed that a credential dumping tool was downloaded? What is the file name of the download?
Ans. In the /root/Downloads folder, we can see the file mimikatz_trunk.zip. Therefore, the tool is Mimikatz.
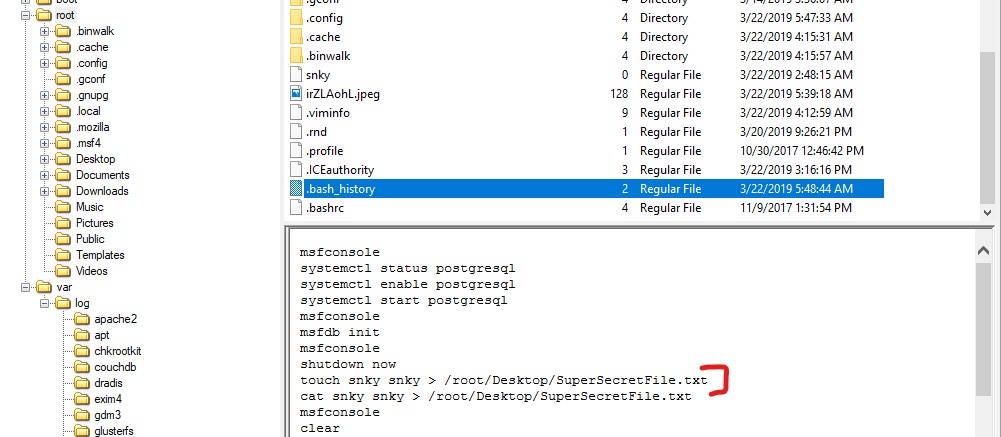
Q4. There was a super-secret file created. What is the absolute path?
Ans. In the /root/.bash_history file, we can see the root user history. The absolute path to the secret file is /root/Desktop/SuperSecretFile.txt.
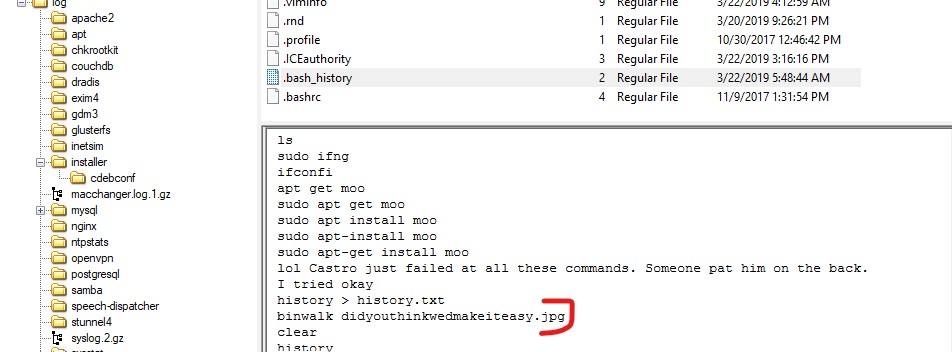
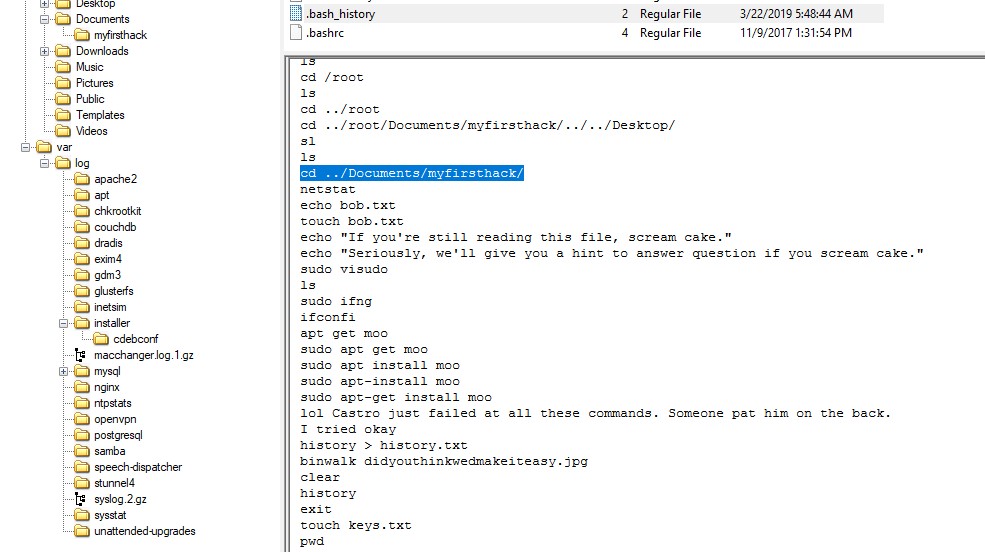
Q5. What program used didyouthinkwedmakeiteasy.jpg during execution?
Ans. In the .bash_history file, we can see that binwalk was used on the PNG file.
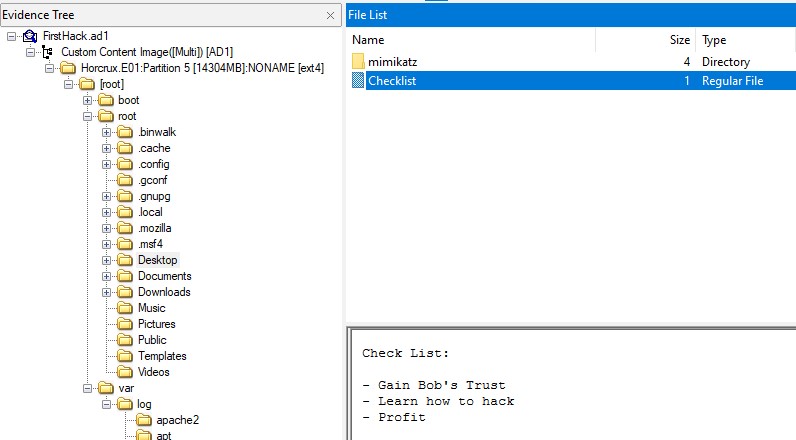
Q6. What is the third goal from the checklist Karen created?
Ans. “Profit” is the third item on the /root/Desktop/Checklist file.
Q7. How many times was apache run?
Ans. In the /var/log directory, there are three log files, all of which are empty. This means Apache never ran.
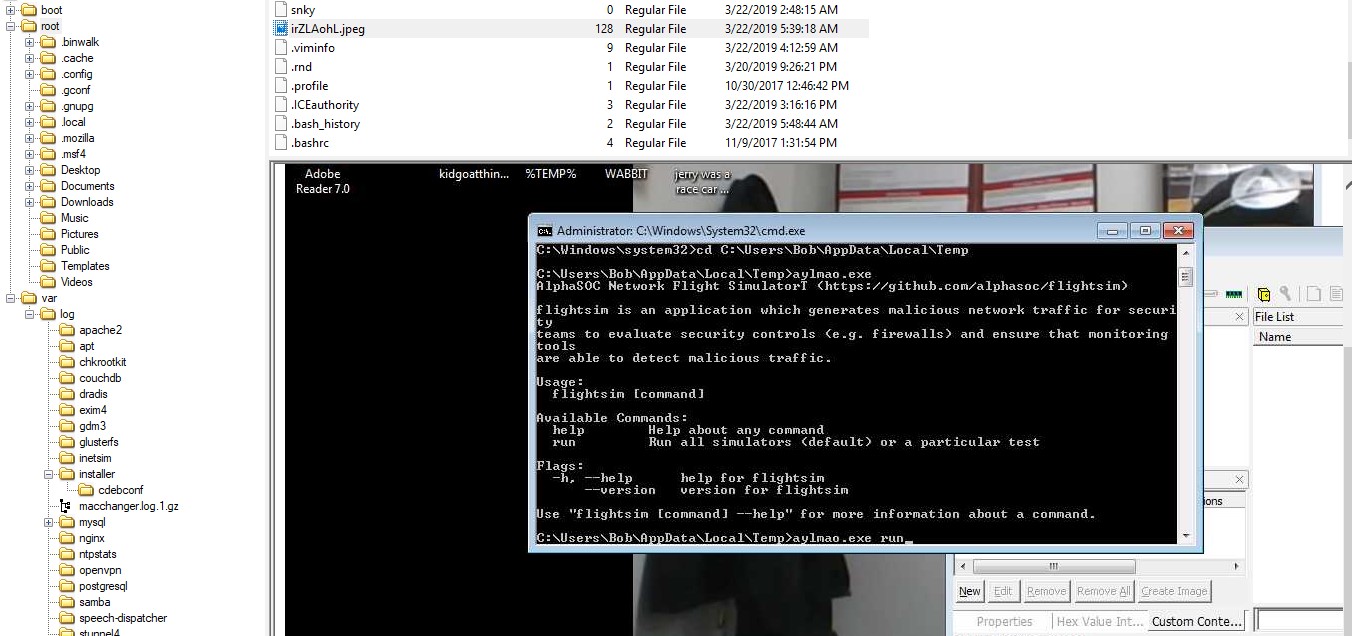
Q8. It is believed this machine was used to attack another. What file proves this?
Ans. /root/irZLAohL.jpeg
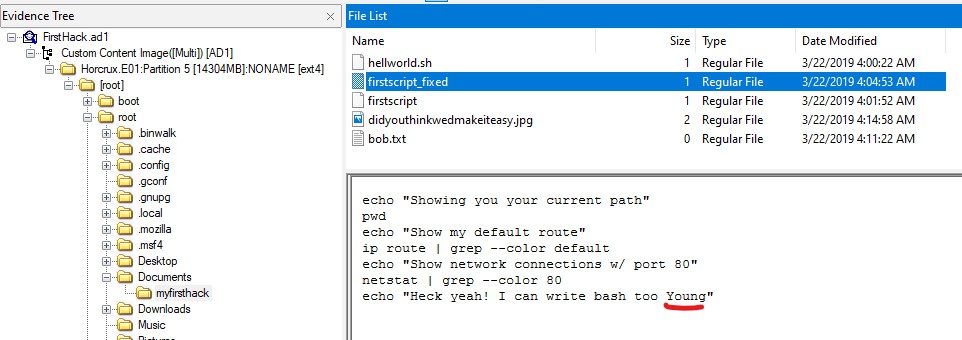
Q9. Within the Documents file path, it is believed that Karen was taunting a fellow computer expert through a bash script. Who was Karen taunting?
Ans. It looks like in /root/Documents/myfirsthack/firstscript_fixed, Karen is taunting “young.”
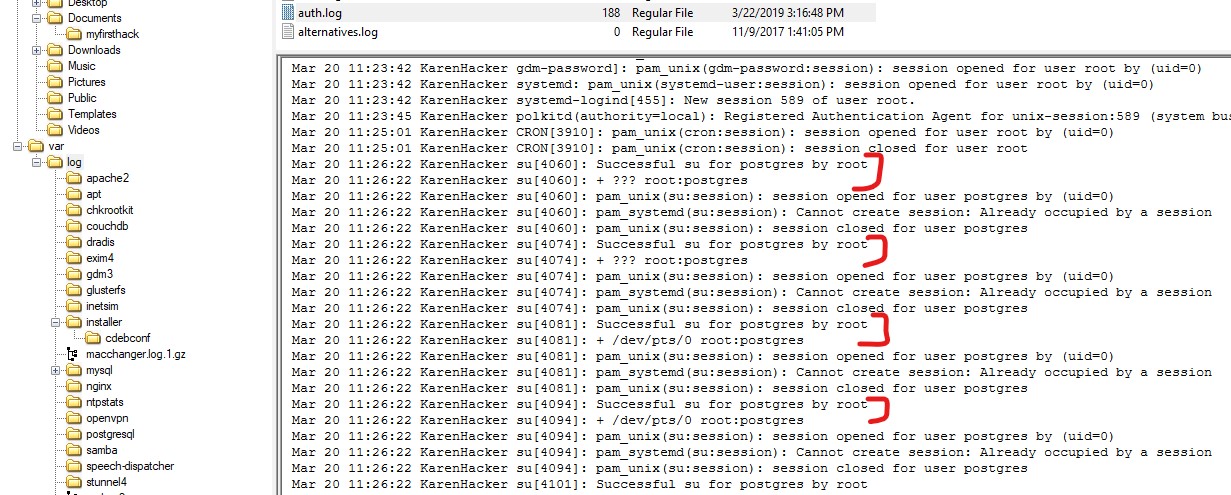
Q10. A user su’d to root at 11:26 multiple times. Who was it?
Ans. In /var/log/auth.log, we can see that the user postgres su'd to root.
Q11. Based on the bash history, what is the current working directory?
Ans. “cd ../Documents/myfirsthack/” is the last cd command in the bash history.
Voila! Challenge completed. Thanks for reading.