Content
Challenge Description
Challenge Name : B1ll_Gat35
Author : ALEX BUSHKIN
CTF : PicoCTF
1
Can you reverse this Windows Binary?
The challenge binary can be downloaded from [here]](https://jupiter.challenges.picoctf.org/static/0ef5d0d6d552cd5e0bd60c2adbddaa94/win-exec-1.exe).
Hint1 : Microsoft provides windows virtual machines https://developer.microsoft.com/en-us/windows/downloads/virtual-machines
Hint2 : Ollydbg may be helpful
Hint3 : Flag format: PICOCTF{XXXX}
Solution
The first step involves checking the binary type and executing it in the terminal. 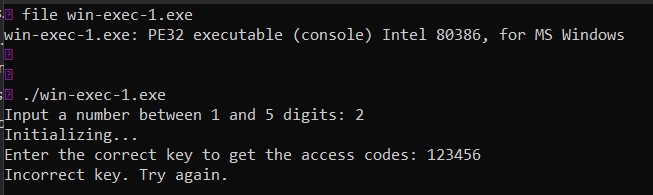
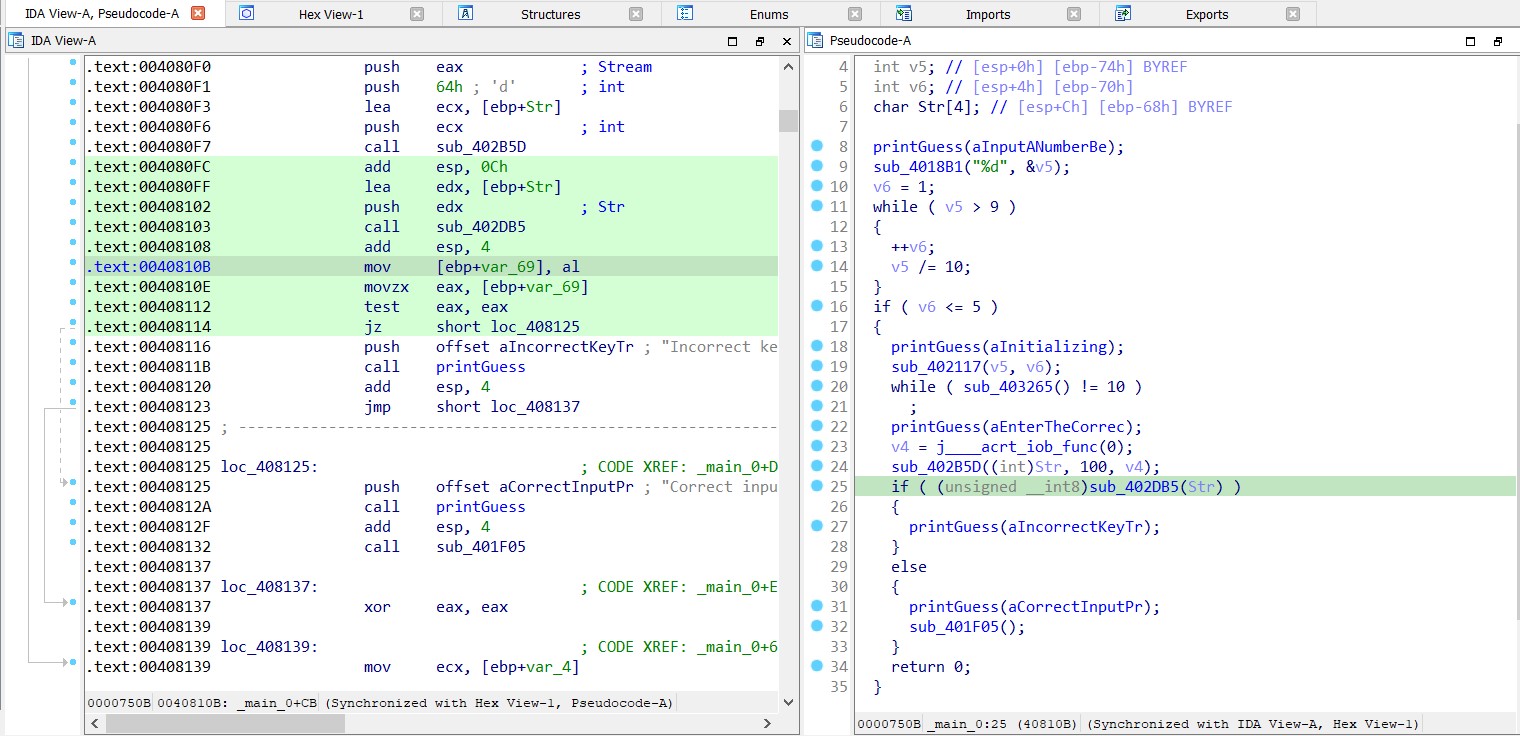
The binary is identified as a PE32 executable. It prompts the user for two inputs, and if the provided key is incorrect, it displays the message: “Incorrect key. Try again.”
Next, the executable is opened in IDA (Interactive DisAssembler) for further analysis.
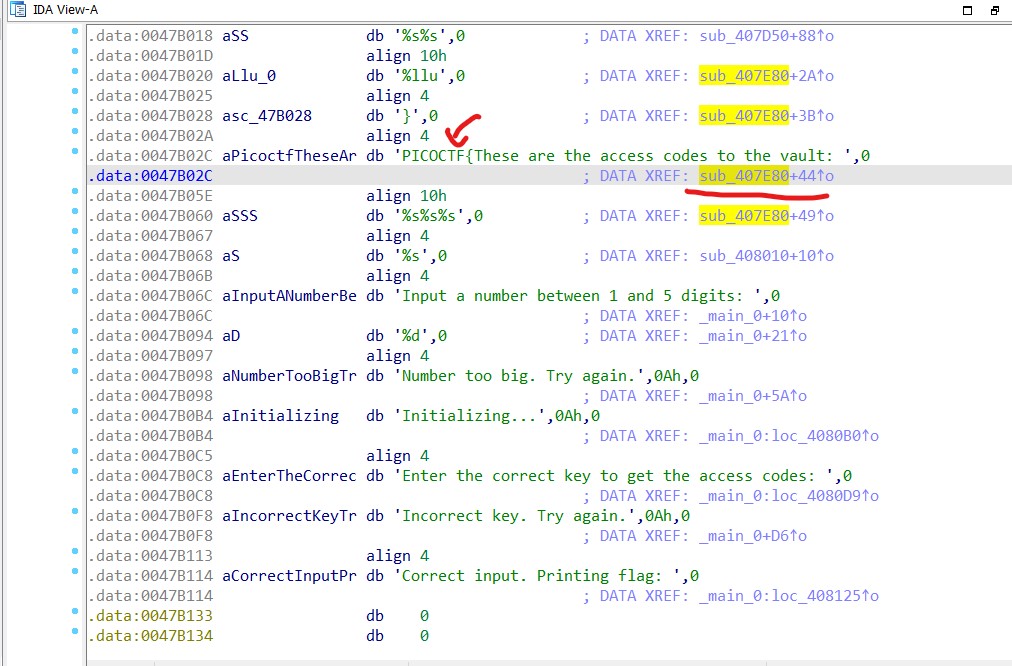
Upon examining the strings section, one string particularly caught attention.
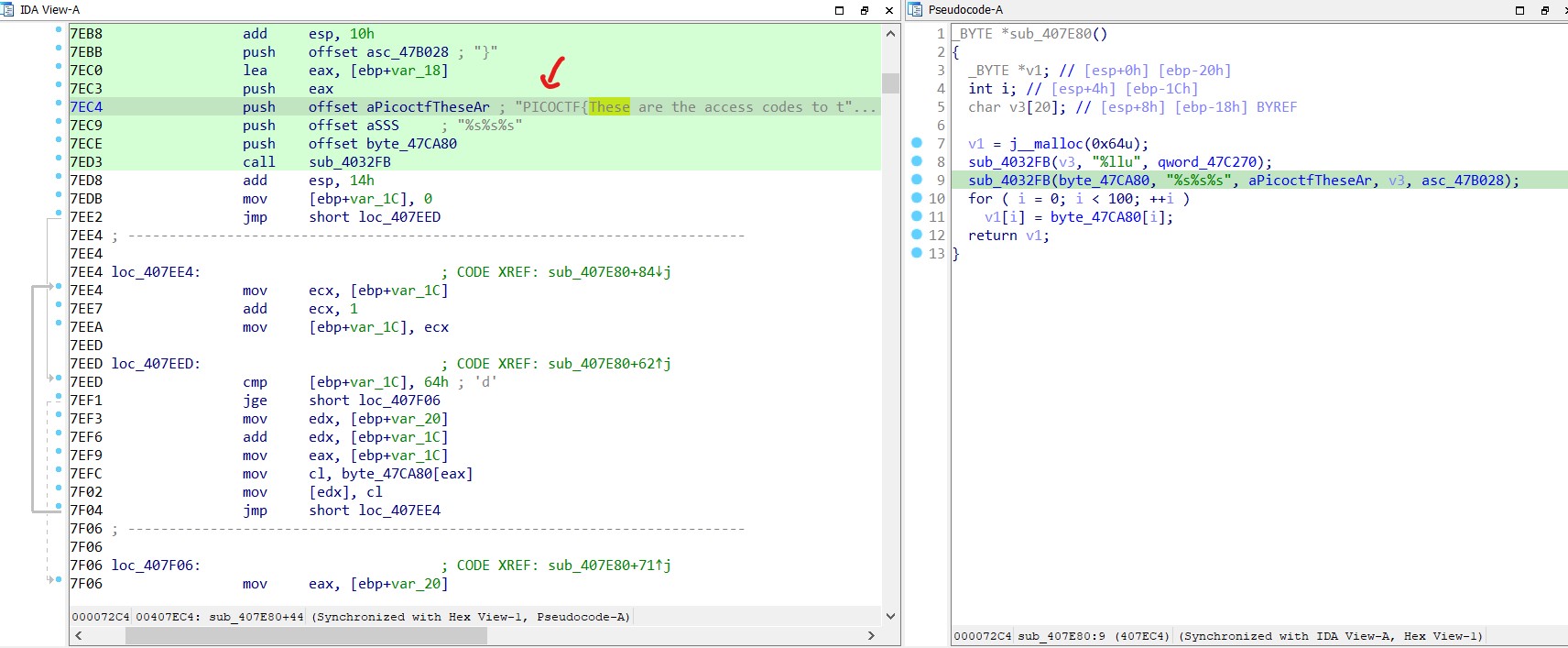
The function where this string was utilized was examined through cross-references, revealing that it was being appended to other strings to complete a flag.
Retracing the steps to the cross-references of this function revealed a series of interconnected function calls.
sub_401F05 -> sub_408010 -> sub_403F21 -> sub_407F20 -> sub_401028 -> sub_407E80
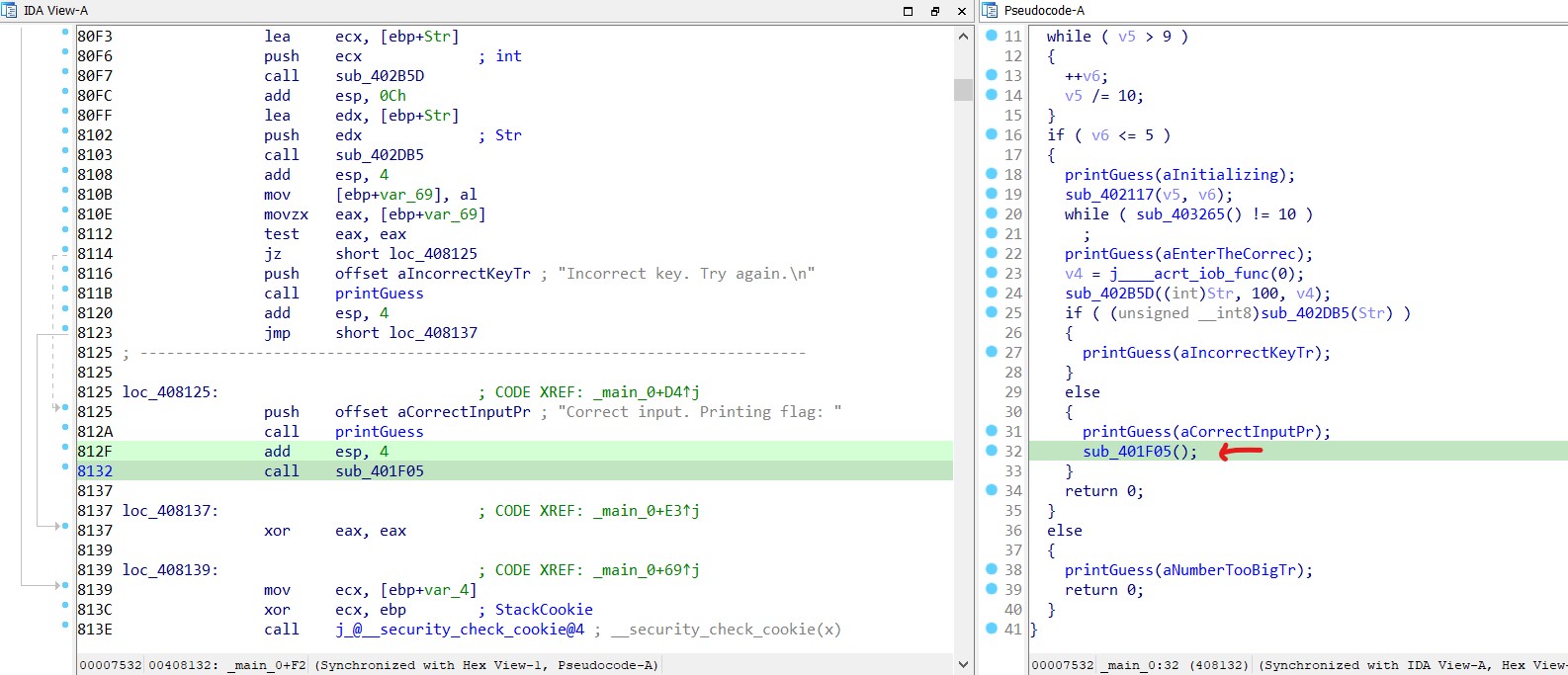
In this context, the function sub_401F05 is called after a function that resembles a print operation, using the argument “Correct input. Printing flag:”.
If there is a way to invoke this function, it will result in the flag being printed.
The function can be invoked using two methods:
1. Patching the Binary in IDA
The binary was modified in IDA by altering the instruction from jnz short loc_408137 to jmp short loc_408137. This change ensures that the function is called regardless of the input provided.
The patched binary can be downloaded from here.
2. Dynamic Analysis Using OllyDbg
The binary can be loaded in OllyDbg, and navigation to the desired address can be accomplished by pressing Ctrl+G.
A breakpoint should be set at address 0xfa8108 . Once the program is executed, it will prompt for input.
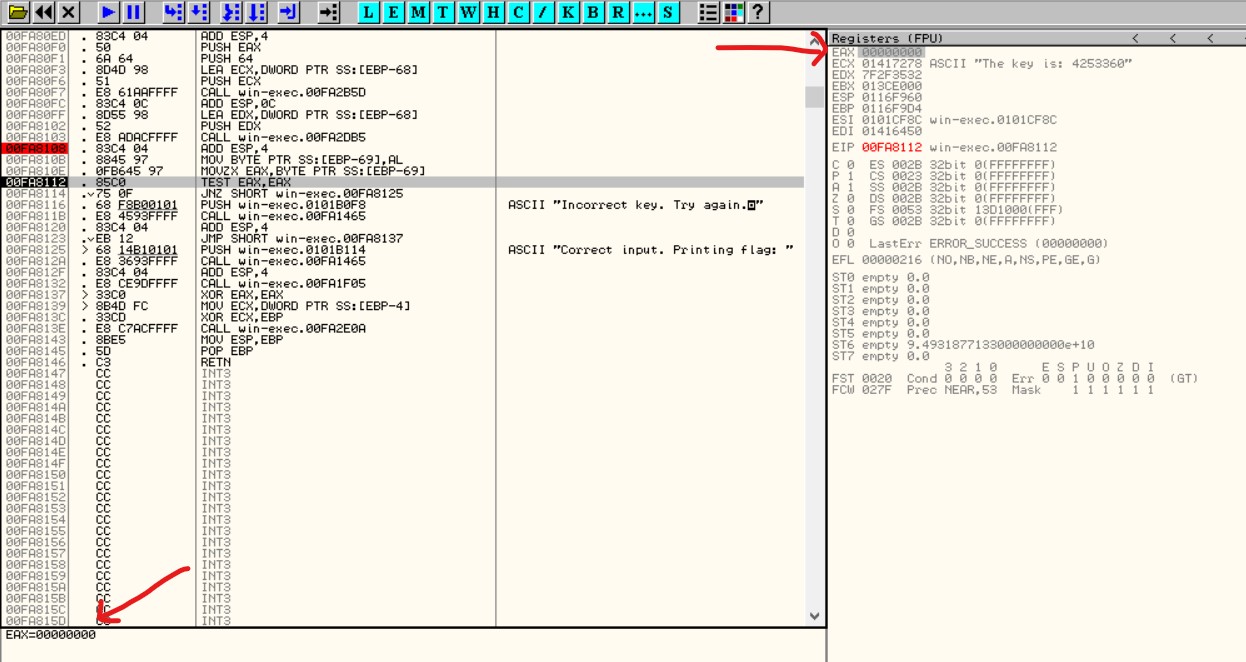
After providing any valid input, the program will halt at the breakpoint. By stepping over the instructions, it can be observed at address 0xFA8112 that the value of EAX is 00000000. Consequently, the jump will be executed based on the value of the zero register.
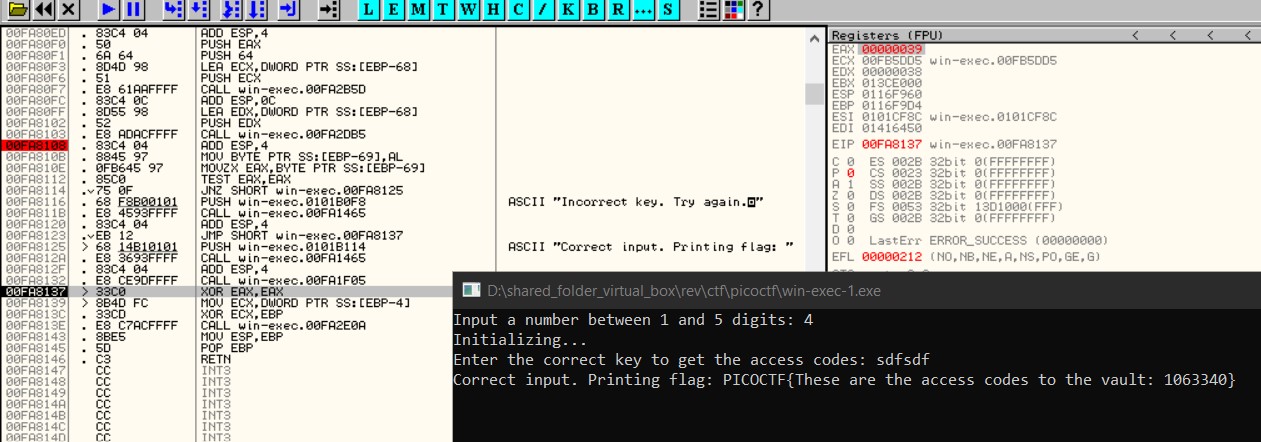
By simply changing the value of EAX and continuing execution, the flag will be printed successfully.
The flag is : PICOCTF{These are the access codes to the vault: 1063340}