These Labs are from Chapter 17(Anti-Virtual Machine Techniques) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
Tools used:
- IDA Pro
- X32Dbg
Lab 17-01
Analyze the malware found in Lab17-01.exe inside VMware. This is the same malware as Lab07-01.exe, with added anti-VMware techniques.
Note: The anti-VM techniques found in the lab may not work in your environment.
Question and Answers:
Question 1: What anti-VM technique does this malware use?
Answer: The malware is using x86 instructions to check whether it is running inside the VM or not.
Question 2: If you have the commercial version of IDA Pro, run the IDA Python script form Listing 17-4 in chapter 17(provided here as findAntiVm.py). What does it find?
Answer: Given script was using IDA6.x backward APIs which are no longer supported by the newer versions of IDA. SO i changed the older functions with newer ones by using the hex-rays offical document.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
from idautils import *
from idc import *
heads = Heads(get_segm_start(get_screen_ea()), get_segm_end(get_screen_ea()))
antiVM = []
for i in heads:
if (print_insn_mnem(i) == "sidt" or print_insn_mnem(i) == "sgdt" or print_insn_mnem(i) == "sldt" or print_insn_mnem(i) == "smsw" or print_insn_mnem(i) == "str" or print_insn_mnem(i) == "in" or print_insn_mnem(i) == "cpuid"):
antiVM.append(i)
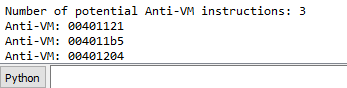
print(f"Number of potential Anti-VM instructions: {len(antiVM)}")
for i in antiVM:
set_color(i, CIC_ITEM, 0x0000ff)
ida_kernwin.msg("Anti-VM: %08x\n" % i)
Load the file into IDA Pro via File -> script file…, choose the script file. It tell us the location of 3 anti-VM techniques used by the malware.
THe instructions detected:
- 0x00401121: sldt(No Pill)
- 0x004011b5: sidt(Red Pill)
- 0x00401204: str
Question 3: What happens when each anti-VM technique succeeds?
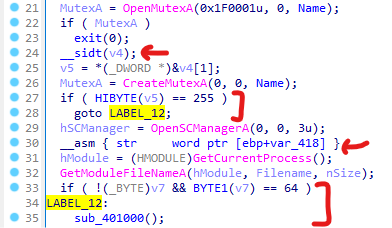
Answer:If sidt and str succeeds then the malware calls a function sub_401000 which deletes the executable.
sldt is employed in function sub_401100. If sldt succeeds then the malware exits.
Question 4: Which of these anti-VM techniques work against your virtual machine?
Answer: I am on VirtualBox, so none of the techniques worked on my system.
Question 5: Why does each anti-VM technqiue work or fail?
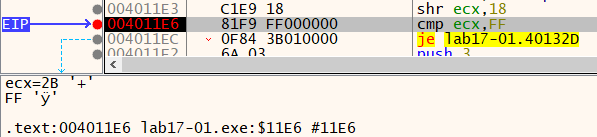
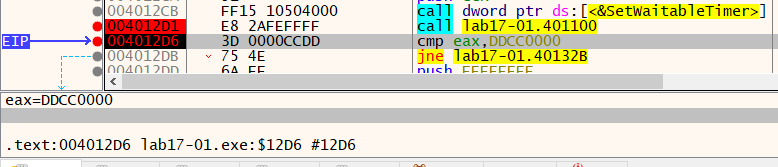
Answer: For sidt, we can check the reason for failure, by setting a breakpoint on 0x4011E6, we can see that the value in ecx is 0x18 not 0xFF(the signature for VMware).
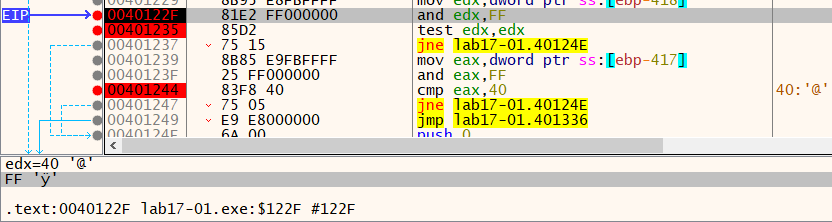
Str instruction is at 0x401204, but the comparison for the returned value is at 0x40122F which also fails as it doesn’t return the expected value.
For sldt, we set a breakpoint at 0x4012D1 where it compares the value with 0xDDCC0000 which also fails.
Question 6: How could you disable these anti-VM techniques and get the malware to run?
Answer: We can manually change the values by setting breakpoints at the cmp instruction or we can NOP-out the anti-VM instructions.
Lab 17-02
Analyze the malware found in the file Lab17-02.dll inside VMware. After answering the first question in this lab, try to run the installation exports using rundll32.exe and monitor them with a tool like procmon. The following is an example command line for executing the DLL.
run dll32.exe Lab17-02.dll, InstallerRT (or InstallSA/InstallSB)
Question and Answers
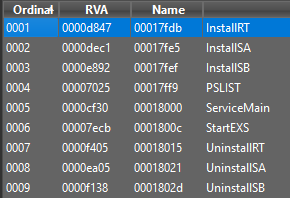
Question 1: What are the exports for this DLL?
Answer: Exports functions are : InstallRT, InstallSA, InstallSB, PSLIST, ServiceMain, StartEXS, UninstallRT, UninstallSA, UninstallSB.
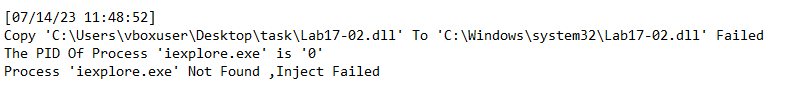
Question 2: What happens after the attempted installation using rundll32.exe?
Answer: I tried to run the malware using rundll32.exe, but it just terminated.
1
rundll32.exe Lab17-02.dll, InstallRT
Question 3: Which files are created and what do they contain?
Answer: It created a xinstall.log file in the same directory of the dll.
Question 4: What method of anti-VM is in use?
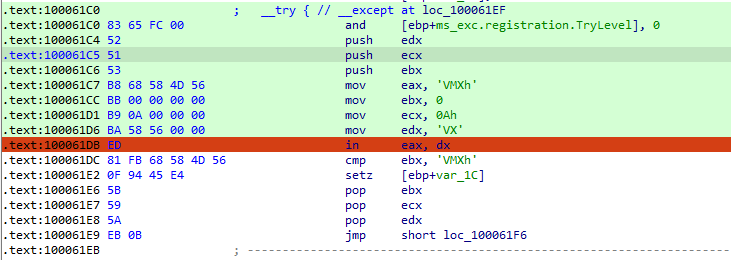
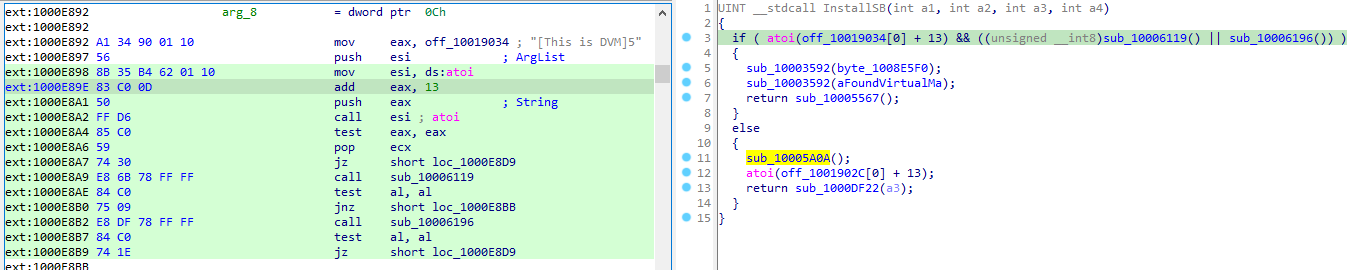
Answer: In sub_10006196, malware queries the VMware backdoor I/O communication port using the magic value VX by using the x86 in instruction.
By pressing x, we can see the cross-reference of this function. It is used in all the install exports.
Question 5: How could you force the malware to install during runtime?
Answer: To run the malware during runtime, patch the in instruction at 0x100061DB.
Question 6: How could you permanently disable the anti-VM technique?
Answer: At the starting of every install export, it check for a byte at the end of stream 0ff_10019034. we can use a hex editor to modify the static string in the binary from “[This is DVM]5” to “[This is DVM]0”.
Alternatively, NOP-out the check in debugger and write the change to disk.
Question 7: How does each installation export function work?
Answer:
InstallRT: It retrieves the pid of a process, either iexplore.exe by default or a custom process name passed in as an argument. Then it gets higher privilege by changing token to SeDebugPrivilege. Then it performs DLL injection on the pid retrieved.
InstallSA: It performs installation via service installation. It uses Irmon or custom string passed in as an argument as the service name.
InstallSB: It performs installation via service install and DLL injection if the service to overwrite is still running.
Lab 17-03
Analyze the malware Lab17-03.exe inside VMware. This Lab is similar to Lab12-02.exe, with added anti-VMware techniques.
Question and Answers:
Question 1: What happens when you run this malware in a virtual machine?
Answer: The malware immediately terminates.
Question 2: How could you get this malware to run and drop its keylogger?
Answer: We can change the value of zero flag before the jump instruction.
Question 3: Which anti-VM technique does this malware use?
Answer:
- in instruction(backdoor I/O communication port)
- Searches for the string “vmware” in registry key “SYSTEM\CurrentControlSet\Control\DeviceClasses”
- checks for common MAC addresses using GetAdaptersInfo
- checking for process name starting with “vmware” by comparing hash