These Labs are from Chapter 16(Anti-Debugging) for practice from the book “Practical Malware Analysis” written by Michael Sikorski and Andrew Honig.
Tools used:
- Detect-it-Easy
- PEview
- IDA Pro
- X32dbg
- OllyDbg
Lab 16-01
Analyze the malware found in the Lab16-01.exe using a debugger. This is the same malware as Lab19-01.exe, with added anti-debugging techniques.
Question and Answers
Question 1: Which anti-techniques does this malware employ?
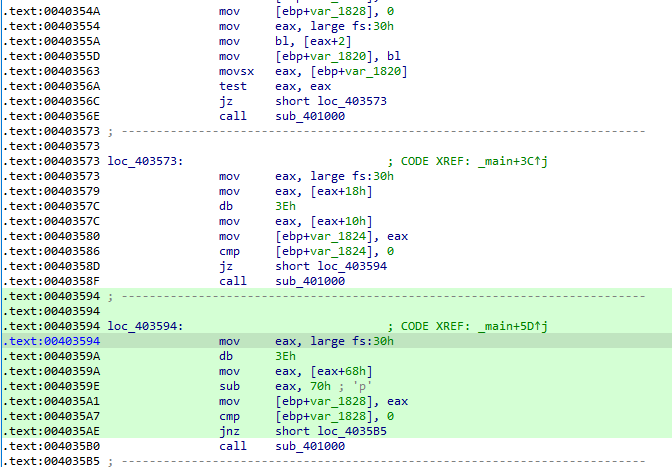
Answer: After opening the malware in IDA Pro, we can clearly see that it is accessing BeingDebugged, ProcessHeap and NtGlobalFlag to check, if it is running in a debugger or not.
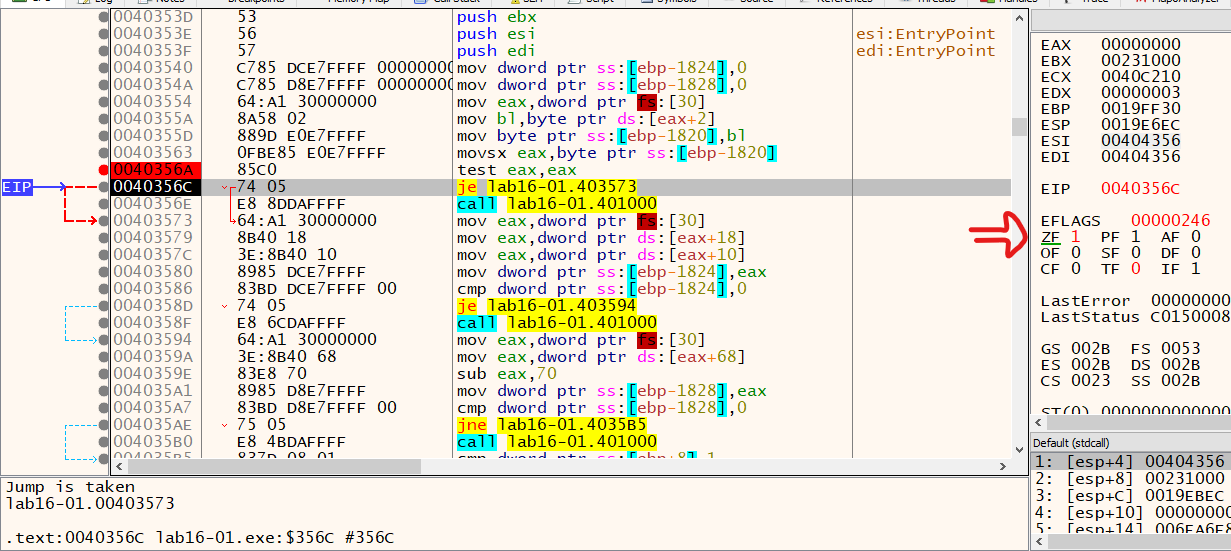
We can see at 0x40355A, it checks for (fs:30h)+2 which contains the value of BeingDebugged flag.
Similarly, at in loc_403573 it checks for ProcessHeap at offset (0x30 + 0x18 + 0x10) and at loc_403594 it checks for NtGlobalFlag at offset (0x30 + 0x68).
Question 2: What happens when each anti-debugging technqiue succeeds?
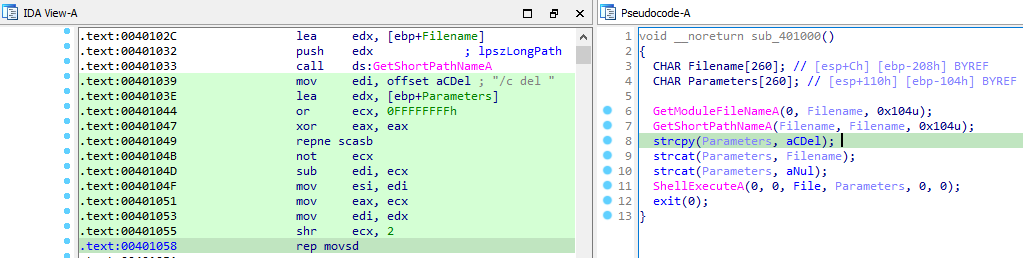
Answer: If any technique succeeds then it calls a function sub_401000.
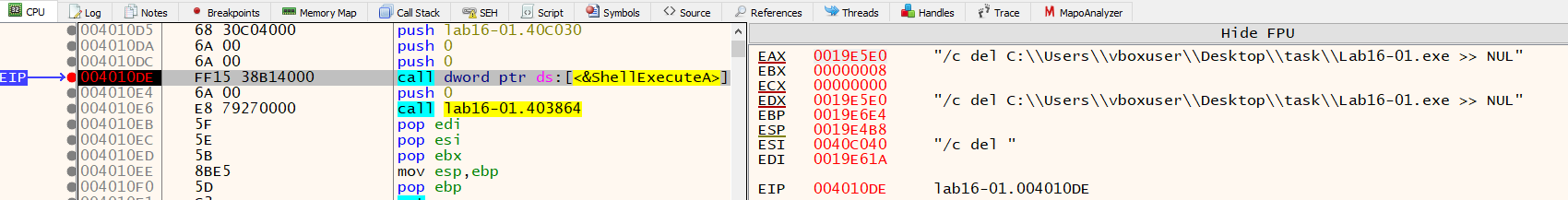
Where it frames a command(“/c del C:\Users\vboxuser\Desktop\task\Lab16-01.exe » NUL”) to execute in cmd.exe by calling ShellExcuteA. This functions is used for self deletion.
Question 3: How can you get around these anti-debugging technqiues?
Answer: We can manualy set a breakpoint before the cmp instruction ad change the path of the jump. By chaning the zero flag or by changing the eax value.
But there are more than 70 occurences of the instruction “mov eax, large fs:30h” which is used to get a pointer to the PEB structure.
So, instead of doing it manually, we can use x64Dbg plugin named ScyllaDbg which has a lot of options in debugger hiding. It will automatically hide the debugger from the malware.
Question 4: How do you manually change the structures checked during runtime?
Answer: When eax gets the pointer to the structure after the instructions like “mov eax, dword ptr ds:[eax+10]”, you can follow the pointer into the dump and modify it.
Question 5: Which OllyDbg plug-in will protect you from the anti-debugging technqiues used by this mawlare?
Answer: I used x64Dbg, for that you can use ScyllaHide.
Lab 16-02
Analyze the malware found in the Lab16-02.exe using a debugger. The goal of this lab is to figure out the correct password. The malware does not drop a malicious payload.
Question and Answers
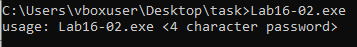
Question 1: What happens when you run Lab16-02.exe from the command line?
Answer: It exits after printing “usage: Lab16-02.exe <4 character password>”.
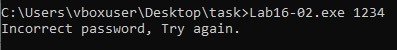
Question 2: What happens when you run Lab16-02.exe and guess the command line parameter?
Answer: It exits after printing “Incorrect password, Try again.”.
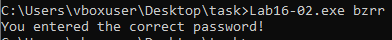
Question 3: What is the command-line password?
Answer: bzrr is the correct password.
Question 4: Load Lab16-02.exe into IDA Pro. Where in the main function is strncmp found?
Answer: strncmp is at 0x40123A in main function.
Question 5: What happens when you load this malware into OllyDbg using the default settings?
Answer: Process immediately terminates when loaded into OllyDbg.
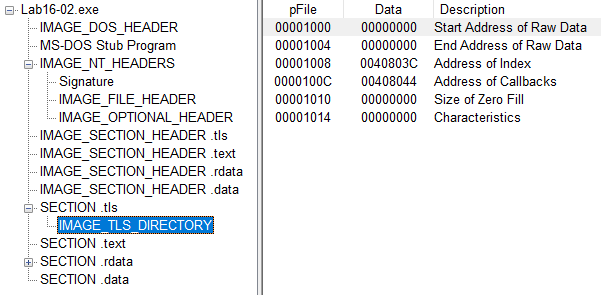
Question 6: What is unique about the PE structure of Lab16-02.exe?
Answer: Malware contains a .tls section. We can see it in PEview.
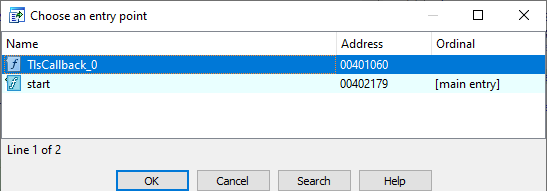
Question 7: Where is the callback located? (Hint: Use CTRL-E in IDA Pro.)
Answer: We can see that TlsCallback_0 is at address 0x401060.
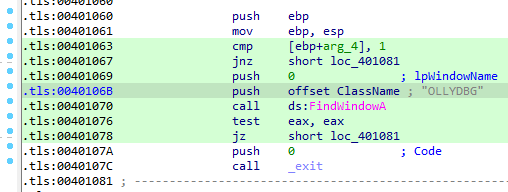
QUestion 8: Which anti-debugging technique is the program using to terminate immediately in the debugger and how can you avoid this check?
Answer: In TLS callback, it checks for a windows named “OLLYDBG” using FindWindowA. If it is present then it will exit.
We can manually change the value of eax before jz instruction to avoid the exit call or it can also avoided by using the PhantOm plugin.
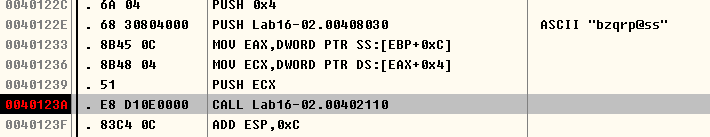
Question 9: What is the command-line password you see in the debugger after you disable the anti-debugging technique?
Answer: We can set a breakpoint at strncmp after disabling the plugins. bzqr is the password that we see.
Question 10: Does the password found in the debugger work on the command line?
Answer: bzqr doesn’t work on the commmand-line.
Question 11: Which anti-debugging technique account for the different passwords in the debugger and on the command-line, and how can you protect against them?
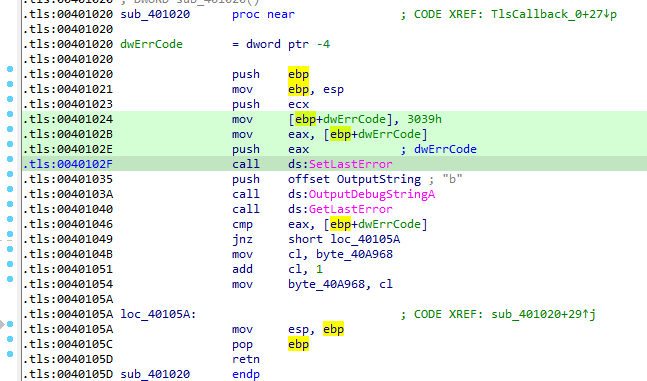
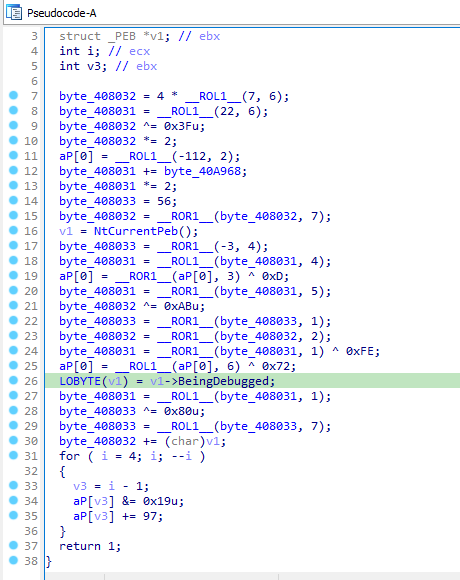
Answer: TLS callback function calls a function sub_401020,in which the malware uses OutputDebugStringA to check for the debugger.
In StartSddress function, it gets the value of BeingDebugged flag.
It uses the results of these techniques accordingly to decode the password.
Lab 16-03
Analyze the malware in Lab16-03.exe using a debugger. This malware is similar to Lab09-02.exe, with certain modifications, including the introduction of anti-debugging techniques. If you get stuck, see Lab 9-2.
Question and Answers
Question 1: Which strings do you see when using static analysis on the binary?
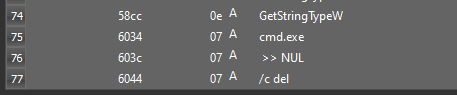
Answer: We can see the strings by opening the malware into Detect-it-Easy. “cmd.exe”, “» NUL”, “/c del” are present in the malware which can be used for self-deletion.
Question 2: What happens when you run this binary?
Answer:Nothing happens after running the the binary, it just terminates.
Question 3: How must you rename the sample in order for it to run properly?
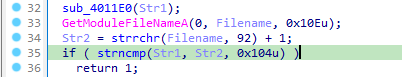
Answer: In main function it seems to be comparing two name using strncmp after a call to GetModuleFileNameA. If the file name doesn’t match then it returns from the main function.
We can set a breakpoint at the call to strncmp and see the name of file it compares with.
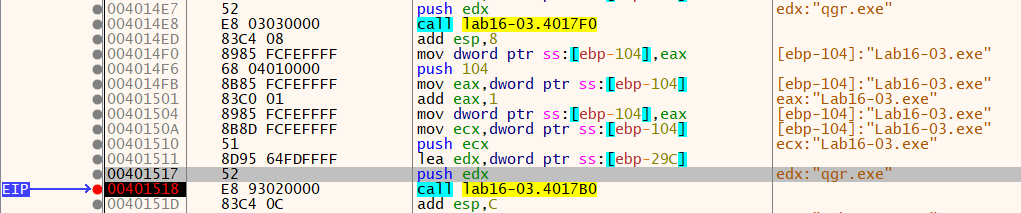
At first we see that it compares the name of the malware(Lab16-03.exe) with “qgr.exe”. But even then the malware doesn’t seem to be sending the request to domain.
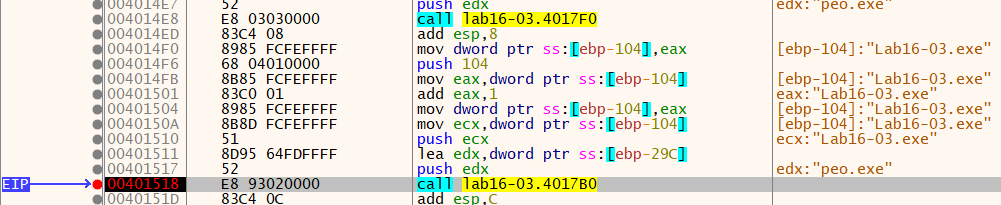
After disabling the anti-debugging techniques, we again check for the name at the call to strncmp, this tiime we can see that it compares the name with “peo.exe”.
If we change the malware name and try to run it, this time we can see that it tries to connect to a domain named “adg[.]malwareanalysisbook[.]com”.
Question 4: Which anti-debugging techniques does this malware employ?
Answer:
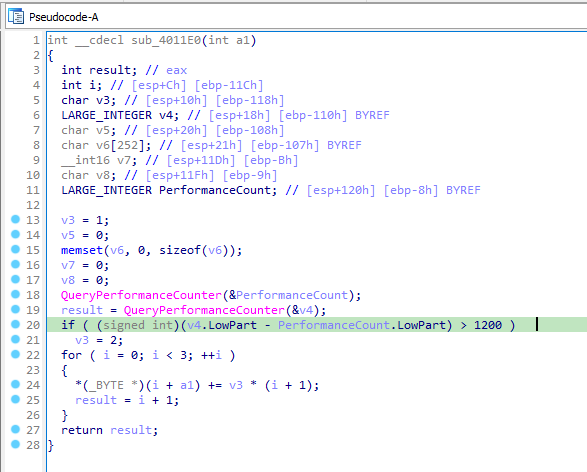
QueryPerformanceCounter
In function sub_4011E0, it calls QueryPerformanceCounter twice. If the difference between the results of these calls is greater than 1200 then it changes the value of a variable. Here a unhandled exception is caused by divide by zero instruction, on which the debugger automatically stops. This causes time delay.
Check file residue
At 0x401518, it calls strncmp where it comapres the name of the malware with a another string. The another string is modified by accordingly by the result of the above technique. If it fails then the malware exits.
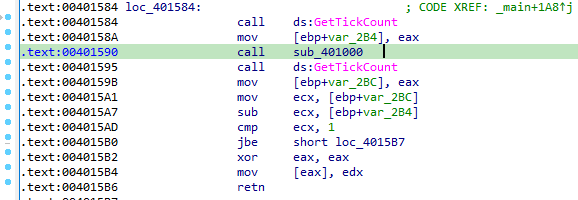
GetTickCount
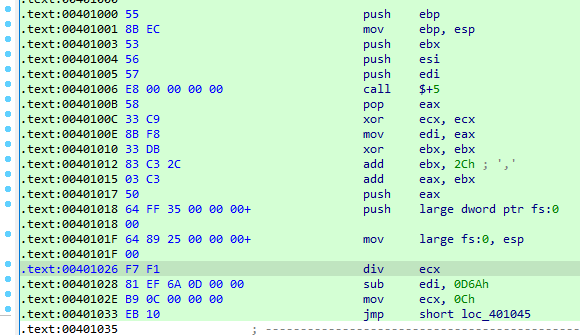
At loc_401584, the malware calls sub_401000 between two GetTickCount calls.
Function sub_401000, the malware causes an unhandled exception that the causes breakpoint at instruction “div ecx”. This breakpoint causes time delay that fails the check at 0x4015AD.
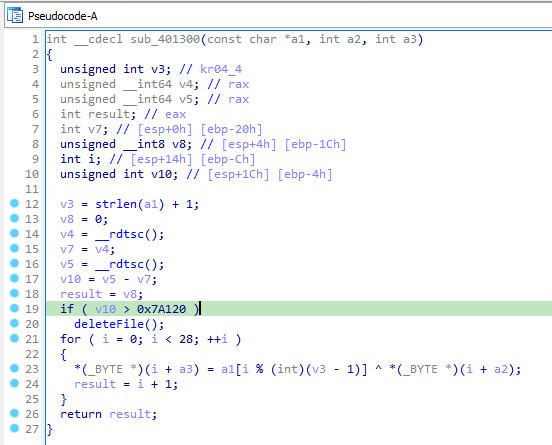
rdtsc
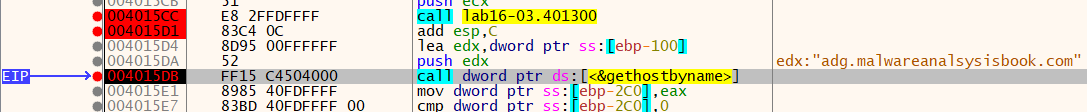
At 0x4015CC, a function sub_401300 is called with three parameters(“1qbz2wsx3edc”, buffer copied from unk_40604C, name variable). There are two rdtsc instructions in this function between them is the exception. After that the difference is compared to 0x7A120 at 0x401377. If this comparison fails then the malware deletes itself by calling the function sub_4010E0.
Question 5: For each technique, what does the malware do if it determine it is running in a debugger?
Answer:
- QueryPerformanceCounter: It changes the value of a char that is used to deocde the value of the filename.
- Filename Check: It exits if the filename don’t matches the expected.
- GetTickCount: If it fails then it causes an exception at 0x4015B4.
- rdtsc: If this check fails then the malware delete itself.
Question 6: Why are the anti-debugging techniques successful in this malware?
Answer: The anti-debugging timing checks are successful because the malware causes and catches an exception that it handles by manipulating the Structured Exception Handling(SEH) mechanism to include its own exception handler in between two calls to the timing checking functions. Exceptions are handled much more slowly in a debugger than outside a debugger.
Question 7: What domain name does this malware use?
Answer: “adg[.]malwareanalysisbook[.]com”, it can be checked by setting a breakpoint at gethostbyname call.